Which edition of Shadowrun is right for me?
An attempt to answer an impossible question
This is the multi-page printable view of this section. Click here to print.
An attempt to answer an impossible question
The one that started it all
Not currently written up; can you help contribute?
The ultimate evolution of the OG game mechanics
The ‘second era’ of Shadowrun game systems
The last ‘complete’ version
The latest? Yes. The greatest? Hmmm.
My personal favourite
A master list of all my Shadowrun houserules and rule ideas
Design goals, summary of changes from RAW
Discussing what I am trying to achieve here
Trim the number of skills back
Matrix attributes, types of devices, commlinks
Rebalance spirits to make them less overwhelming in combat
Things to do between missions
How to find things, and avoid being found
Nerf foci, but make them more flexible too
How to know a guy who knows a guy
Various kinds of Matrix damage, link-locking, biofeedback, etc
Change reagents to add a new option - trinkets
What it does and how to get it
A streamlined set of Matrix actions
Cap initiation, cap max number of quickened spells, but make quickened spells more durable
How to figure out who goes when and what they can get done
Decks, programs, agents
Hosts, common devices, and IC
All about the Grid’s po-po
Drugs are bad, mmmkay
Actions done in meatspace
The next stage of human evolution
Actions done in the matrix (for riggers & deckers)
Gun modifications and accessories
All magic-related actions (in meatspace or the astral)
Cyberware, bioware, and other augmentations
Short examples of common tasks for criminals
Acting defensively out of turn
Footnotes, miscellaneous stuff
An attempt at streamlining this ungainly beast
Links, resources, and ideas for Shadowrun GMs
Tips and tricks for first-time tables
Links for Shadowrun GMs
An (incomplete) attempt to re-write the in-game Matrix to make more sense
Why I wrote this & what I hoped to achieve
The devices that make up the Matrix’s infrastructure
Augmented reality and virtual reality
How your commlink decides what to show you and where to put it
The ins and outs of proving you are a member of society
How normal people protect their Matrix stuff
Finding stuff out
How the Matrix works for criminals and those who hunt them
How the Matrix interacts with cyberware and other gear
Bits and pieces
Being a Matrix backport attempt, presented for your delight (doubtful) and utility (maybe)
What I’m trying to do
How to use (most of) the 6e Matrix rules in 5e
Line-by-line comparison of the Matrix rulesets
compiled and edited by PenLlawen (twitter, reddit, SR forums)
discuss this document: (Reddit thread)
When it comes to Shadowrun editions, there are no easy answers; only annoying compromises. Sorry!
Each version of SR comes complete with a significant number of foibles and fiddly bits, and I can all but guarantee that some of those are going to drive you mad. Every version of SR comes with bits you’re going to want to patch or houserule over. There is no clear winner in that department.
To make things worse, a lot of people get emotionally attached to their favourite edition, come to terms with its faults, and then like to get in arguments online about it1. So this can be a contentious topic to discuss, despite the fact that it’s a really common-sense question for a new player to ask.
So, setting out to write this doc, I thought the fairest way to do it was: attempt to give you some moderately objective facts about each version, then give the microphone to one or more ride-or-die megafans of each version in turn to make the case why this is the one you should play. Hopefully this will give you a rounded perspective; though not, perhaps, the easy answer you were seeking.
Given that there is no right answer, there’s a couple of factors that might make the decision for you without much further thought:
I am not innocent of this, either. ↩︎
I also have a doc that breaks down key game systems (combat, initiative, spellcasting, …) and compares them, line by line and side by side, in all six major releases of Shadowrun.
It’s difficult to present as a web page - it has very large tables - so you can download it as a PDF instead.
| 1e | 2e | 3e | 4e/4e20A | 5e | 6e | |
|---|---|---|---|---|---|---|
| Publisher | FASA | FASA / Wizkids | Wizkids / Catalyst | Catalyst | ||
| Core mechanic | Skill or stat; variable target number | Skill+stat; variable dice pool | ||||
| Tone | Retro-futuristic | Some transhumanist/sci-fi themes | ||||
| Matrix & comms tech | Wired & chunky; voice-only cellphones & PDA-like pocket computers; some “dungeon crawling” Matrix | Wireless & sleek; smartphones; Matrix stuff somewhat more integrated into gameplay | ||||
| Deckers exist as a distinct role? | Yes | Sort of | Yes | |||
| Editing quality / organisation | Good | Mostly good; later books poor | Poor | Poor | ||
| Roll20 charsheet? | No | Yes | Yes | Yes | Yes | WIP |
| Foundry system? | No | No | No | No | Yes | No |
| Sourcebook selection, community support, quick ref material, digital tools | Good | Good | Great | Good | ||
1e-3e feature deckers who are quite “disconnected1” from the rest of the team: they have Matrix “dungeon crawls” that can involve a prolonged exploration of computer systems while the other characters might not have anything to do. This can be a challenge for GMs to manage.
4e attempts to address this by adding the ability to get hacking done to any character willing to spend money on gear, so at least all the characters can participate in hacking together. The addition of the wireless Matrix means hackers also have things they can hack in real-time during combat. But this dilutes the iconic cyberpunk hacker tropes. Many people felt this was a net loss. (But they are wrong! -Tony, 4e advocate)
5e & 6e revert back to having a distinct decker role, but continue to try to offer deckers the ability to act in concert with everyone else through wireless hacking. But again, complex Matrix actions can involve the decker doing their own thing for prolonged periods while the rest of the team is idle. GMs still need to work to manage this, although it’s not as tricky as with 1e-3e. Some tables still take an “all decking is done by NPCs” approach.
Shadowrun started in 1e with a kitchen sink approach to dice mechanics: variable target numbers, dice pools, and two different vectors of modifiers for difficulty – plus opposed and resisted rolls, and other mechanics. Some of these were phased out gradually, others still exist in modern Shadowrun.
Variable targets were phased out over 2e & 3e, for a static target number of 4, although sometimes they could still vary, and it would still be modified up or down by situational modifiers.
In addition to the above, SR1-3e have “dice pools”: some number of dice that the player can choose to use on important or difficult tasks. Once used, though, they couldn’t be used again until the pool refreshed - typically the next turn. These dice pools are derived from your character’s skills and attributes and are the primary way attributes affect their chances of success. This can be a fair bit of book-keeping, as each character has multiple pools to draw upon, that must all be tracked as they are used and later refreshed. However they do give players a good amount of tactical agency.
From 4e and onwards, there is a major change to these mechanics. The “dice pool” term is re-used, now defined to mean “your skill rating plus the rating in a linked attribute”; for example, to shoot a gun, you might use a number of dice equal to the number in your Pistols skill plus the number in your Agility attribute. The target number is always 5 and situational modifiers only influence the number of dice you roll. This results in a smoother probability curve, but you’re rolling (and counting) a lot of dice. 20+ is quite common; 30+ is possible; for very powerful characters 40+ isn’t unheard of.
5e introduced a system-wide mechanism called “limits” in an attempt to curb powergaming. Each character has a set of intrinsic limits, derived from their attributes, which cap the maximum number of successes they can achieve on a test, regardless of how many dice they roll through combinations of high skills, expensive gear, magic spells, etc. It is also used for some gear, eg. the accuracy rating of a gun is applied as a limit on the hits when rolling to attack with it. Limits are often criticised for being fiddly to apply and ineffective at stopping players becoming very powerful. They were dropped in 6e.
Pun intended. Sorry. ↩︎
Source: https://www.reddit.com/user/AstroMacGuffin/comments/f4j9o9/why_1st_edition_shadowrun/
The root of my undying love for first edition Shadowrun is that it is too good to be left behind. Second edition isn’t simply a “1e but fixed”, it’s also fundamentally changed in a few places. Comparing 1e to later editions generally, nobody will ever convince me that a 300 page book is somehow a streamlined version of a 200 page book. Meanwhile, plenty of people make almost all of 1e work to great effect (frag you, vehicle combat rules). My nostalgia is happy sticking up for the underdog edition.
But besides that, some other reasons I’m on this weird hill:
There’s a “less is more” effect in play: 1e puts greater emphasis on the heist, or on being a detective, or whatever’s your flavor of underbelly RP, and it adds that emphasis by having fewer rules (and sometimes simpler rules).
Every player has a chance to shine in their unique way because at the same time the rules are diverse and thus bent toward emphasizing play style. There is no same-y-ness between magician, decker, muscle, and detective play styles, nor is there any of that pesky streamlining to narrow down the number of viable play styles per role. This is a game for going as far off the beaten path with a character concept as you could want and still be viable as a shadowrunner, all in barely 200 pages.
Variable staging numbers on weapon damage represent important parts of the simulation and were a key part of characterizing weapons. Higher staging numbers mean a character must be skillful in order to do extra damage, and that the target had better stay out of the field of attack. Lower staging numbers mean you could accidentally decapitate yourself with the weapon, but it’s reasonably easy to deflect with a little skill. That’s a lot to lose in the name of streamlining and so I still don’t know what they thought they were going to gain by removing variable staging from the game.
The classic priority system and other parts of character generation all dictate that the player must get creative. Harsh constraints just have that effect, and 1e’s character build rules are both generous and difficult to overcome.
1e is the most basic system. If something isn’t covered in the rules you do some kind of Test and move on with the game. It’s more personal, tactile, that way.
By keeping the simulation a little simpler, 1e’s rulebook is smaller and looks more approachable. The game requires patching and house ruling, and the GM must take extensive notes, but I like that. The structure of the book’s information needed a lot of work, and sometimes I’m thankful for a clarification from 2e or 3e, or for something introduced in the 2e equipment chapter; but I find that a physically thicker, larger book is intimidating to new players, and more expensive as a ticket price, and that’s before you count the extra cost of time getting familiar.
Sometimes described as “a polished version of first edition”, it’s close enough that a lot of game material and expansions barely need changing to work across both versions. However, there are still a good few differences.
Nobody has contributed yet!
If you want to contribute a writeup about why SR 2e is the One True Edition, contact me via the links in the page footer on Twitter, Reddit, or Discord.
Source: https://www.reddit.com/r/Shadowrun/comments/f89hka/which_edition_of_shadowrun_faq/finibbk/
If I misremembered something or forgot something, please feel free to correct, but I’ll just ignore any “but X edition is better because Y” responses, that’s not what I’m here to do. I just want to clarify a few things that are often misunderstood, and explain key differences.
I’ll try to keep it sweet and compartmentalised, and I won’t get bogged down in which is best and why you should play it. I play 4eA at the moment, and we’re unlikely to go back to 3e but it definitely did some things better than later editions in my opinion.
People get bogged down and scared because ‘high target numbers’, but in most circumstances it’s no more or less crunchy than 4eA, indeed many of the modifiers are literally the same number, they just modify the base of 4 rather than adjust from your dice pool. In either case, number of successes equates to degree of success. The difference is simply rolling a fixed dice pool based on skill+stuff against that modified number, or rolling your modified dice based on skill+att+stuff pool against 5.
3e also has dice pools based on your stats. (not the same as what 4e onwards calls “dice pools”) - Combat/Spell/Hacking - which allow you some flexibility as to where you want to really put in the extra effort. You also have a Karma Pool, which naturally grows over time as you earn karma. In later editions, these mechanics became ‘Edge’ but as taht is just an attribute you can boost it doesn’t reflect gaining experience the same way.
It’s a more deadly system, the way damage is stepped from L through to D means a lot of damage can happen very quickly, you only need 4 net hits to step from M (3 boxes) through to D (10 boxes). You can bleed out fast, and you only ever get one Hand of God, which is very costly. Furthermore, armour acts to reduce the target number of a soak roll, but the roll itself is only your Body dice - so a Body 2 mage is going to get hurt no matter how much kevlar you wrap them in.
However, while more deadly, 3e is more forgiving of cinematic action gameplay. Your dice pool will never say ’no’: Jonny the Mage can pick up that discarded shotgun, take that shot in the rain through eyes filled with blood from casting drain, and take down that last bad guy whose only illumination is a flickering street light to save the day. It probably won’t happen with 2 dice against a target number of 37, but he can try (and I’ve seen people pull off even more remarkable feats that the whole table enjoyed).
I think that may be the point where people get the bad impressions from it, as there isn’t really a ’no you can’t’ point of running out of dice, because there will be a number you can crunch out to say ‘you need this to do it’. That can make it a little slower to work out the nuances, as those less than practical actions come up a little more, but the payoff is characters pulling off superhuman efforts, which is part of role playing and part of why you spent a fortune on that ‘ware.
Defaulting between weapon types is more logical; you take a +2 modifier for, say, picking up an Assault Rifle when you do not have the Rifle skill. +4 to default to a stat.
Perception is just an Int roll, not a skill. Athletics and Stealth are their own skills as well, so between these I think you’re not stuck with quite so many “must have” skills, like Climbing, Running, Infiltration, Shadowing, and indeed Perception which limits choices outside of them. That streamlines things a lot outside of combat, as well as in creation.
There are a couple of creation systems, both point build and priority.
No Vampires, no AIs, no Free Spirits, no Pixies, no Sasquatches… Changelings came in in YotC.
Mages and Shaman are much more distinct.
Mages are depicted as scholars, they summon Elemental which they must bind to their will, they’ll have a Hermetic Library, they’re not bound by the whims of a Totem, although they might have a bent based on their Tradition.
Shaman are more primal, they have to follow a Totem which gives them bonuses and penalties, and a path of behaviour. They summon Nature Spirits which are bound by Domain, and can’t call upon an army of them as Mages can Elementals - however, they’re free, on demand, and offer a little more versatility. Some Totems switch out Nature Spirits for Spirits of the Elements.
There are other Traditions with their own selections of Spirits and rules such as Voodoo and Wuxing.
Spellcasting is much the same regardless of tradition. However, unlike later editions, spells are learned by Force, so if you want to overcast a Force 9 Powerbolt, you’ve got to learn Force 9 Powerbolt as an individual spell - which is a tough roll just to learn the spell.
Magic Loss is kind of a big deal, it can happen just from taking Deadly wounds, it isn’t recoverable except through initiation, and you have to offset with Geasa - so you’re not likely to risk using slap patches. If you don’t offset, you lose it forever.
Spell Defence also means allocating some of your Sorcery and Spell Pool to that, which means you have less to be offensive with. Because yeah, Sorcery is a skill, Ritual and Counterspelling aren’t separate, nor are Binding and Banishing separate from Conjuring.
I think Magic is a little less strong in 3e than 4e because of how spell defence works.
Cyberlimbs allow for breaking down of pieces and partial installations, like if you have a cyberarm, you cut the price of the dermal sheathing on the rest of you by 20%, or if you want to install a smartlink and already have an image link and the induction pad can be installed in that cyberarm, you only need the limited simrig and processor. Limbs add more body rather than damage boxes, because you get 10 boxes regardless of how tough you think you are. Dermal plating, bone lacing etc also adds to Body, not armour.
Having loads of ‘ware would also increase your signature for targeting by sensor weapons.
Bioware uses its own “bio-index”, which is even worse on magic than cyberware, as it doesn’t just reduce your magic rating, it does so in a way you can’t offset with geasa.
I think this actually offers better granularity and they are actually easier to track as separate systems than “one costs half the Essence of the more expensive pile”. Though the effect on magic is really harsh.
Drone-riggers and getaway-driver-riggers are more distinct through skillsets, expense, and do not mean you can also try your hand at decking. Learning to rig a CCSS system to take over a building can be useful though.
Is very much its own thing, probably a bit too far from the rest of the group. You have data size and memory to think about, I/O speeds of your connection, and might end up running a different dungeon crawl to the rest of the team. Definitely possible to run a combat decker and go in with the team, hack standalones/closed systems, depends how your GM sets you up, but it’s also entirely possible to be playing a completely different game.
Your own team is also less liable to get Hacked themselves, Electronic warfare is something only the rigger might worry about, because Wireless is a very limited thing, so no Hacking the security team’s guns either. There might be sentry guns and stuff you can play with, but the kind of Matrix overwatch is I think a bit different.
There are no technomancers, and otaku (a sort of prototypical technomancer) are bad.
Source: https://www.reddit.com/r/Shadowrun/comments/f06b1w/what_edition_to_start_with/fgs0sch/
I’m going to keep this general… I don’t see the benefit of arguing about specific skills or anything. So…
One of the things I love about future fiction is that it tends to heavily reflect the time in which it was written. Old Atomic Age fiction is fascinating to read as a person of this time and place.
Cyberpunk, and hence Shadowrun, is heavily rooted in the 80s. The hair, the punk, the neon, the dark dystopian future full of acid rain and big hair.
But it’s not the 80s any more. It’s inevitable that Shadowrun updates to the times. It was getting rather silly that the cyberpunk future didn’t have wireless everything. We needed to capture the zeitgeist of our time. Cellphones are cheap and ubiquitous. Megacorporations know more about our shopping habits than we do. The problems with end stage capitalism are staring us in the face. And we can keep the neon, the hair, the ‘tude, etc.
So, we update from 3e and we get wireless, AR, cheap computers, cheap drones. And a certain “Apple-ification” of tech, yes.
Shadowrun had a problem. It was the “Everyone go get pizza, it’s time to do the decker minigame.”
4e makes everything wireless and that gives the hackers stuff to do in combat. Hack the opposition’s ‘links, sign them up for spam, turn off their firewall, mess with their drones, listen in on their coms, disable their smartguns, etc etc etc. Judicious use of wifi blocking walls made it necessary for the hacker to come along for the ride too.
Wireless and cheap computers allowed people to “rig” on the cheap. Nothing beats a dedicated rigger, but the Street Samurai could keep a couple of cheap drones for peeking around corners or watching the escape route. Everyone could, and that is futuristic and good.
Virtual Reality is so…. Lawnmower man. 80s. AR is a more up to date and believable interface that lets you check out that hot elf chica’s social media profile on the dance floor, which fits the zeitgeist better.
I get that many people like the tone of earlier editions, but tone is largely set at the table anyway. You can have neon and mohawks and punk with 4e rules. You just also get ubiquitous cell phones and network connectivity.
4e also did away with a priority character generation system. I think the point buy allows for more nuanced characters. I think priority gen forces stereotypical characters.
I liked the metaplots. I thought the Brackhaven political stuff was interesting and plausible, for example.
I think the 4e matrix rules make sense. I’m a techie by trade. I get the 4e matrix rules. They make sense. They’re not complex, but they ARE…. there’s a lot. Trying to explain all of that to my friends felt like I was trying to give them a networking certification. I get why 5e tried to simplify the matrix rules. I just think they made it worse….
So why not play 5e? 6e?
The editing is atrocious. The 20A book had all the splat books in the main book index. You could look up anything from all the books in one spot. That is awesome. (So does the 5e Master Index Edition, to be fair —Editor)
I find 5e and 6e hard to read. Again, the editing sucks. There’s too much gratuitous filler text, and they changed the background color to blacks and reds. Ooooohhhh. Edgy! Ugh. The language took a tone change too. I liked the “drek” of previous editions. Really though, after the beautiful editing and cross referencing available in the 20A book, reading 5e and 6e makes me angry… Why? Why’d they have to mess up something so basic? It makes it so hard for new people…
I already have all the splat books, and 5e/6e gave me gratuitous filler text instead of… gear, weapons, adept powers, etc that I had taken for granted as being “Standard”. I don’t appreciate being charged for something I already have.
The 4e Seattle book is awesome. I feel like 5e and 6e tried to go away from Seattle, but never released a good meaty book on other locations, so everything got kind of…. Fuzzy… for locations. That might just be me though.
They brought back priority generation after 4e. The standard priority gen is… well, everyone uses alternatives for a reason. Try making a troll decker. You need high priority for Troll, you need high priority for money to afford the stupid expensive cyberdeck, and you still need stats and skills. It doesn’t work. So people use alternatives. Also, it felt like a naked attempt at “We’re going retro!” without a good reason to do so.
Cyberdecks are expensive again. Some cyberware got more expensive too. Why? Tech gets cheaper, not more expensive with time! It beggars belief. It flies against the zeitgeist of the time. And again, it felt like a naked attempt at “Look at us, we’re going retro!” without a good reason to do so.
I hate 5e limits. I loathe them. If they’re an attempt to cut down on power gaming munchkins, they suck at it and instead of saddling every single roll in the game with something to check, they could have just imposed limits on dice pools ONE time at character generation. If they’re an attempt at “realism”? They’re not needed, and they saddle every single roll in the game with something to check. They’re no benefit, high cost.
I don’t like the 5e or 6e metaplots. They feel recycled. Another crash! Another Chicago, but with nanites this time! And 6e feels even worse.
I don’t like the matrix Foundation runs. If I want to play Wild West or Fantasy or whatever, I’ll go play a different game.
I don’t like the matrix rules. They don’t make SENSE, from a technical standpoint. They brought in moveable matrix stats, which is just more headache to keep track of. The matrix needed a simplification, not a completely new ruleset with completely new problems.
I loved the 5e idea of grids. It brought in the Net Neutrality issues of our time. And then they did away with them….
I’m rambling…
4e20A. Better than 1-3e because of more believable tech, no pizza run/matrix time, better character generation.
4e20A. Better than 5-6e because the editing doesn’t SUUUUUUCK, better character generation, more believable tech, no limits, and the plot isn’t recycled. Again.
Source: https://www.reddit.com/r/Shadowrun/comments/f06b1w/what_edition_to_start_with/fgs0sch/
5e is the most recent complete edition, as a result it has the most sourcebooks and most up-to-date vision of what the 6th World would like in relation to real life.
Core mechanics work pretty well and are quite simple and oddly elegant (attribute + skill = pool).
Situational modifiers that add or subtract from the dice pool are easily fine tuned by the GM, impose meaningful variables on the chance of success, and reflect the reality of the environment / world pretty well.
Success thresholds (how many successes you need to succeed) are easily understood and reasonably reflect the difficulty of succeeding at any particular task.
In 5e speed (initiative / dodge), competency (dice pool) and resilience (armor and body) works as one would expect in a game that reflects “Matrix” movie style combats. Depth and nuance of character building allow you to build a “Neo” type who can literally dodge bullets or a “Hulk” who can shrug off smaller caliber firearms and light melee weapons. It’s “cinematic” but retains enough relation to reality that armor can stop bullets and a 600 pound Troll hits with more force than a 6 lb Pixie. Gear choices significantly affect the outcome and bear a reasonable relationship to action movie reality. While it’s possible to “break the game” by building for the extreme this is mostly controlled by the realities of the 6th World – your GM isn’t going to let you walk down the street in heavy armor with an assault rifle or combat axe without attracting Lone Star and likely heading to jail. This creates the all-important dynamic of choosing your gear to suit the situation.
Weapons and armor include significant variance and customization options (important for the combat focussed PCs) that import meaningful choices on the player/ PC.
This nuance and depth is critical for delivering meaning to the combat focussed characters’ choices. It’s one of the shining successes of Shadowrun in general going all the way back to 1e.
One of the requirements of a heist type game like Shadowrun is usabe rules for social interaction and cons. Luckily 5e’s social rules don’t suffer from the inane rules bloat that other sub-areas do (looking at you, rigging and matrix). Social is mostly a question of opposed dice pools and modifiers and that’s just fine. Toss in some bonus modifiers for good RP and you’ve got all you need. Need more depth and nuance? Cutting Aces provides some good ideas on how to essentially use teamwork tests within the scope of conning someone.
5e’s magic system is very similar to prior versions and works out of the box without modification, well almost. The core issue of “magicrun” (whereby magic trumps everything else) is an unfortunate side effect of the continuous expansion of magic power within the mechanics and supplements. You know this is a problem when all your players turn up to the table with a mage or mystic adept. There are some very easy ways to mitigate this via houserules (ban reagents for increasing limits, restrict the number of active spirits at once, ban mystic adepts, etc). You might not feel this too much if your players are relatively low-powered, but even straight out of chargen savvy players with mage characters can be almost obnoxiously powerful. This only gets worse the longer you play. GMs should keep a weather eye on it, lest the mage players start to overshadow the rest of the table.
While 5e’s Matrix does address the shortcoming of 4e’s script-kiddie syndrome that rendered deckers irrelevant, it feels like it was written by someone who was reaching for detailed, nuanced mechanics and edited by someone who failed to playtest it. The end result is a confusing mess of overly complex, nested systems that utterly fail to address the core aspect of any RPG; IT MUST BE FUN. The action economy also renders almost all Matrix activity less effective than just shooting the person / thing / target. The supplements help, a little, but it’s hard to fix the core rules without fixing, you know, the core rules. This is sad and a terrible miss in a game that is meant to embody a mashup of Cyberpunk and Fantasy.
Perhaps the worst aspect of Shadowrun 5e, the entire vehicle rules section is utterly atrocious. Riggers are a confused mess where it’s not even clear what attributes to use with the various vehicle control options and even if you do figure it out / houserule it riggers still suffer from Multiple Attribute Dependency (MAD). The vehicle chase and movement rules are an example of what goes wrong with poorly abstracted mechanics. Due to this abstraction simple questions like “how fast does my vehicle go” are not even answered. Rules that were bolted on afterward in Rigger 5.0 don’t help much either. The Swarm rules are terrible from a balance perspective and inane from a common sense perspective. Overall it’s best to ignore the chase rules and heavily edit what’s used from the supplements.
Like all Catalyst Shadowrun products 5e suffers from extensive copy-pasta, resulting in rules that make no sense, that reference non-existent rules from prior editions and mechanics not matching the descriptions. The worst offender is the Street Grimoire but you will find this particularly pathetic example of editing in almost all Shadowrun products somewhere.
5e is perceived as a complex system, but is it? Yes and no. As you can see from above the core mechanics are very simple and easy to grok. The complexity comes from all the small details and the three overlapping subsystems of meat, matrix and astral. While those three subsystems have always been present in Shadowrun (and hence always upped the complexity level) it’s also true that 5e’s complexity was increased by the many “fiddly details” for these subsystems and the many supplements across which these are strewn. To some degree that’s what happens when a game has as many supplements as 5e does, however it’s exacerbated by Catalyst’s poor layout and editing. This is not unique to 5e, it’s present in all Catalyst products and is a product of their poor line editing in general. This can be dealt with to some degree by the judicious use of cheat sheets that summarize and condense these modifiers however it can be very daunting for someone learning the system for the first time. There are ways to manage this information overload by chunking how you learn Shadowrun into meat, matrix and astral sessions, using the aforementioned cheat sheets and simplifying/ hand-waving stuff you cannot remember in the moment.
So we’ve covered why Shadowrun in general and 5e in particular is complex and often perceived as more complex than it is. The question that follows naturally from this is “why would I want to play a complex system instead of one where I can learn it in one session”? The answer is nuance and depth. Systems that tilt towards simple are great for introducing new players but tend to be terrible for long term durability. In the end all characters of a specific type end up feeling the same with little differentiation. With 5e there are so many ways to build AND PLAY a character that they almost never feel or work the same. Everyone’s an individual with nuanced and unique options that drive characterization in a meaningful way.
6e, aka Sixth World Edition, aims to be a fast-playing version of Shadowrun. This is meant to contrast with the previous editions where the natural flow of roleplay tends to be repeatedly interrupted by searching for dice pool modifiers or obscure rules.
For good or for ill, much of the crunch from previous editions has been weeded out. On the upside it keeps the game (and therefore the fun) moving, but on the downside many players who are used to Shadowrun’s long-established run as an ahem “game with a high threshold for system mastery” may find this 180 degree change in direction jarring, unfun, or both.
6e has matured considerably since initial release in 2019. It’s uncharitable, but fair, to say it was rushed out at that date. Since that initial release there has been significant errata to clean up sloppy editing and choppy rules. However, you never get a second chance to make a first impression and unfortunately for some players these improvements simply were too little or too late to change their minds.
As of this writing, the expansion rulebooks for combat (Firing Squad), magic (Street Wyrd), rigging (Double Clutch), and pop culture/media (No Future) are available, with more resources (Companion, Matrix) coming out later this year.
Please consider an updated-for-2022 Pro/Con list:
Simplified skill list – there are two or so skills every shadowrunner should have, and most archetypes only require 2 more skills on top of that. The 5e corebook’s 79 skills becomes just 19 in 6e.
Simplified initiative and action economy – there are no “initiative passes” as existed in previous editions… everyone gets one turn per round. Bonuses like wired reflexes now give you more actions during your one turn per round.
Matrix hacking rules are the fastest-playing version yet – they are functionally very similar to those in 5e, with the major difference being access is gained at the entire network level rather than icon by icon. In 6e you don’t have to waste time rolling dice to get marks on every single file or device you want to hack… once you’ve hacked access to the host, you’ve got access to everything the host controls!
Any metatype can do any role – in 6e everyone’s attributes begin at 1 and you can pick any metatype right from the get go at priority E (higher metatype pick gives you more attribute points for the attributes where they’re ‘better than humans’).These design changes serve a couple desirable ends: metatypes that have always been thinly veiled analogues for racial minorities are no longer mentally penalized, and you can build any metatype to perform any role without having made the “wrong” choice. Trolls are just as good at being deckers as anyone else, and anyone can be as good a close combat specialist as a troll!
Status effects – this is a new concept to 6e. There are 25 different “statuses” in the CRB that give consistent rules for all sorts of different conditions like being blinded, in cover, on fire, etc. Many effects inflict statuses rather than having their own custom rules that might be slightly different from a mechanically similar one.
For example, rather than there being slightly different rules for invisibility vs concealment, there’s a single status that both the spell and critter power apply and use the exact same rules for.
Combat is generally less dangerous than prior editions – arguably, the least lethal Shadowrun has ever been in any edition. While some might think of this as a downside because it’s somewhat more difficult to one-shot anyone in 6e… I’d call it an upside because honestly who has fun being one shotted? NPCs can use snipers too, ya know!
The two most common complaints you’ll hear about 6e is that “strength does nothing” and “armor doesn’t help”. Both statements are really talking about the same thing: when you get hit you get hurt, but you probably won’t die. These complaints should be taken in the spirit of “I don’t think strength helps ENOUGH” and “I don’t think armor helps ENOUGH”. Because it’s objectively true that you do in fact benefit from strength in close combat and you are in fact better off wearing armor than not.
If a complaint is not about strength or armor, then it’s likely about not liking the new Edge system. There’s nothing wrong with opinions, but bear in mind that 6e is as big a break from 4e/5e as 4e was from 1e/2e/3e and the new Edge system is the reason why. People are going to have opinions about that, and hostile viewpoints tend to be more vocal!
Rather than being a measure of luck that manifests as meta dice manipulation tech, Edge in 6e has a hugely expanded role. In addition to dice manipulation, Edge also serves as the mechanic by which positive and negative modifiers are applied to a test. Lastly Edge also serves as a meta currency you spend to perform special actions like calling a shot or disarming someone.
Sooo…. 6e. The newest and without much doubt most divisive edition of Shadowrun with the big overarching goal of simplifying things. While having several similarities with 5e, it also features some huge changes.
The biggest of them is the new edge system. Instead of being a limited resource used for powerful effects, gaining and spending edge is now common during a session and can also be used for smaller effects, e.g. rerolling one die or increasing the number of a die by one. Many modifiers and qualities were changed in gaining edge and it is now a central part of the system. It also is the most debatable mechanic of the system, bringing its own slew of issues. Many of the problems I am mentioning later on are at least a bit tied to the edge system. Therefore, before starting with 6e, I highly recommend reading more about it beforehand. If the problems it creates might be a dealbreaker to you, don’t try this edition. Edge is so deeply embedded in 6e that it is nearly impossible to houserule it out without changing half of the book.
I’m giving now a quick overview of the most mentioned pro’s and con’s of 6e. If not explicitly stated otherwise, you can assume that I share the public opinion due to my own experiences with the edition.
“Simplification” of Matrix. Some say it’s noticeably simplified, others say it’s no better than 5e. For me, most of the noticeable simplification in the matrix is due to the simplified skill list and simplified initiative. Taking that out, the rest is only slightly simplified and slightly more intuitive due to rewording things, removing one mark/access level and removing grids. So yeah, it’s improved, but not as much as other ones let it seem in my opinion. Still, I take it :) However, I urge you to houserule matrix search, in its current state it’s broken and actually not intended to work this way.
Attack Rating and Defense Rating. Some weapon stats are merged into Attack Rating, which describes the general effectiveness of weapons. Armor (and some other things) adds to Defense Rating. The concept of simplifying offensive and defensive stats this way is interesting, but in its current state, it’s heavily underbaked. It just determines the gain of one single point of edge (or the non-gain of it). Also, with the range of possible numbers being quite limited (base Attack Rating is from 1 to 14), weapons all feel the same. There was a tease though that in the incoming splatbook Firing Squad these two stats are getting more meaningful, so hope is not lost here.
Priority table. A huge improvement here is that every metatype is available for Priority E to C. You can therefore always take the metatype you like without gimping your character. However, it has problems in other areas. Several options are near impossible to take for building a viable character (Attribute E), others are way too powerful or too cost effective (Attribute A, Metatype C). Humans are not a viable metatype. The options are therefore actually more limited than they already are due to using the priority table chargen. I just did an homemade version of karmabuy for my players.
Strength is almost meaningless. With the recent errata, there is nowhere a direct impact on the damage of melee attacks. The most it does is increasing your Attack Rating (a bit more on that later), which translates to an edge, which most times only translates to ⅔ of a hit. So basically a little child can challenge a dragon to a boxing match and both will do the same base damage. Other than that, it’s used almost nowhere.
Armor is almost meaningless. It isn’t relevant for the soak test anymore. That leads to problems like the ones we have for strength. If you ever see the joke of bikini trolls, it’s because of the crazy nerf to armor in 6e.
Skills cost the same as attributes. Because an attribute affects several skills, it is something that just can’t be right.
The majority of qualities and flaws are off at least karmawise and sometimes even effectwise. The usual suspects here are Analytical Mind, Focused Concentration and Impaired Attribute. Analytical Mind in its original form is so cost effective that in my opinion there is not a single character who should not take this quality. In Debt is nicely done though, really like this flaw.
Confusing, missing or contradicting rules, While also true for (at least some of?) the other editions, 6e is the worst here. It is said sometimes that without knowledge of 5e, it is harder or even impossible to play 6e.
Bad editing and layouting. Similar to the point before, while also true for 5e, it’s worse for 6e. German rulebooks excluded though.
Rules contradicting shadowrun lore. By far the biggest offender here are the changes to bullets which would lead to a complete turnaround of the weapon industry lorewise without a reasonable benefit AND also violating rule zero of Shadowrun.
Rules contradicting the design goal of simplification. Again, ammunition, which price calculation suddenly got an additional layer of complexity. It’s often said that 6e missed their design goal. For me, it’s only partially right because of the listed pro’s which are quite impactful. It’s also debatable if the edge system is a simplification or actually brings more complexity.
Mages being even stronger than in 5e. Have to see it more in action, but so far, I would share that opinion. Direct combat spells are a total joke though.
Driving rules. The amount of vehicles you can choose that have doable piloting tests for an average driver is quite limited. January errata did an essential buff to rigger controls though, so riggers are at least a bit playable now (but still in a bad position overall).
Keep in mind that right now we are in a phase where there can still come a potentially bigger amount of errata. So maybe, with just a bit of patience, some of the issues are going to be addressed. If you want to try it out now, DON’T buy the physical version as of now. Because the first printing is missing an huge amount of errata, it’s unusable. Get the PDF (which can be updated) and wait at least for the second printing if you like physical copies. That also applies to the german core rulebook.
Editors note – I personally think SSDR is over-stating this as a “con”. If RPGs had a sort of 1-to-10 scale for crunchiness, with (I dunno) GURPS being an 8 and Honey Heist a 1, then Shadowrun 6e is only ½ or 1 point below from the other editions. It’s a bit less crunchy in a few places, and asks a bit more of GMs to adjudicate details, but don’t confuse it for a narrative style game like Fate or Shadowrun: Anarchy, or even a middleweight game like Savage Worlds. It’s still not that style of game. But that’s just my opinion! And it’s not SSDR’s! ↩︎
Savage Worlds ($10 PDF, $40 hardback) is a generic RPG engine which has numerous supplements and rulesets in all sorts of genres, from the high fantasy of Savage Pathfinder to the Weird West of Deadlands and the post-apocalyptic The After. But no matter the setting, Savage Worlds prides itself on always being Fast, Furious, and Fun!
This cartoon is an excellent overview of the core Savage Worlds game mechanics, if you want a taste of the basics.
Savage Worlds has many characteristics that make it a good fit for playing Shadowrun:
It’s worth noting there are some characteristics that make it not to everyone’s tastes, however.
SWADE’s core dice mechanics are a little more chaotic than Shadowrun’s. The interaction between the exploding dice mechanic and how SWADE determines success level means a small number of rolls – less than 1%, but not none – will produce results that surprise you. This is quite different to Shadowrun, where the boundary of outcome of a roll is much more pre-determined; the odds of a critical failure are almost zero and staggering successes are capped by the number of dice being rolled.
Whether it’s the PC getting a lucky shot at the Big Bad and taking half his life in the first round of combat, or the single NPC goon who refuses to die because he keeps passing Soak rolls, once in a while the dice will shock you. Your mileage may vary if you think this is a bug or a feature. My table loves it!
Savage Worlds been a popular choice for playing Shadowrun via various fan-made hacks for many years. I’m going to mention two specific options based on more polished commercial releases.
Weighing in at a svelte 71 pages, Sprawlrunners ($7 PDF, $25-35 POD) is the all-killer-no-filler Shadowrun ruleset you need.
Sprawlrunners takes the core Savage Worlds rules and adds everything you need to play in a classic era Shadowrun 2050s setting, including:
The book is careful to make the minimum set of adjustments to Savage Worlds necessary, making it easy to learn and easy to modify and tweak.
For example, all character improvements (including getting cyberware fitted, learning new spells, increasing skills, etc) is handled via Savage Worlds’s Advances (basically, levelling up.) Nuyen-tracking is eliminated, and replaced with a flexible pool called logistic points. LPs are used to purchase the gear needed for the mission ahead, which the characters then discard and replace for the next mission – just like in a heist movie.
Sprawlrunners covers a wide range of options for weapons with a few dozen basic statblocks (“light pistol”, “compact SMG”, “assault rifle”, etc) which the players can combine with a few dozen modifications and variations (“burst-fire mode”, “smartgun adapter”, “folding stock”, etc.) It walks a good middle line between allowing players the breathing room to build signature items of gear for their character, without overwhelming new players with too many options.
The author of Sprawlrunners, Manuel Sambs, is quite open that it was designed first and foremost as a toolkit for GMs to build the game they want. As such, it has been kept easy to tinker with; a neat and tidy base that can be used as-is or expanded to your tastes.
I have my own extensive houserules and expansions for Sprawlrunners elsewhere on this site, including wireless Matrix, rules for downtime actions, expanded cyberware, and more!
In addition, there are several excellent commercial expansions for Sprawlrunners.
Beyond these, Savage Worlds has a wide range of settings and expansions to draw upon for inspiration for further modifications. Compared to hacking on the Shadowrun ruleset, this is process is a joy; I find Savage Worlds to be much easier to work within.
If you prefer a crunchier approach, another option for using Savage Worlds to play Shadowrun is the cyberpunk setting Interface Zero 3.0 ($20)/. Unlike Sprawlrunners, IZ has more of a maximalist take on gear, with a very large selection of weapons, cyberware, etc. Take those two, and add on this (free) fan-made hack (which cleverly uses pre-existing Savage World rules for fantasy elements like magic and metahumans) and you get yourself a pretty neat Shadowrun system.
There are various hacks of Shadowrun into rules-light narrative-first RPG engines. These fall into two broad categories:
This style of RPGs can be divisive; many people love them2, some find their light-touch GMing style and emphasis on narration over crunch to be too far away from the Shadowrun feel they crave. You’ve little to lose by checking them out though!
For SR play, a few rules-light narrative-first options I really like are:
Catalyst themselves have had a pass at the idea of a less crunchy Shadowrun, in the form of Shadowrun: Anarchy. As a system it has good bones but is criminally underbaked in lots of different ways. You’ll likely quickly find yourself looking for more houserules to bolt on. If so, start by taking a look at Surprise Threat!, which has lots and lots of thoughtful suggestions.
(The world would be a better place if the author of Surprise Threat! was given free reign to write Anarchy 2e, but we are where we are.)
This section contains a variety of houserules. Some of these were canon for my campaign when we still used Shadowrun; others are ideas we were discussing; others are just sketches of ideas.
These rules are canon for my current campaign.
These rules are designed to hopefully prune back the skill list a little in ways that make sense and make some skill-heavy archetypes have a little bit of an easier time of it (most notably, riggers and deckers.)
Reduce karma cost to level up a skill group from 5x new rating to 4x new rating. Skill Groups are less powerful than attributes, so shouldn’t cost the same to advance. In addition, few Skill Groups contain three or more equally useful skills, so charging them as double the normal skill cost seems more balanced.
This is designed to make it less painful to use Skill Groups as a way of mitigating the large numbers of skills needed for some archetypes.
Remove skill group points entirely at chargen. Instead, increase skill points available as follows:
At chargen, allow Skill Groups to be taken for 2x Skill Points per point going into the Skill Group. This is so players are free to mix and match skills and skill groups as they desire.
Sally Samurai puts a B into skills during chargen. She wants to be good with all sorts of instruments of murder, so she takes the Firearms skill group to rating 5 - this costs her 10 of her 46 skill points.
Later, during play, she decides to improve her skills. First she takes her Firearms skill group from from 5 to 6, which costs 24 karma. Then she decides to focus on rifles, so she takes her Longarms skill (which is part of the Firearms skill group) from 6 to 7. This costs a further 14 karma.
The skill group is now “broken.” She won’t be able to improve it further unless she first takes each of the other skills in the group up to 7.
In the below tables, changes to SR5 RAW will be highlighted in yellow.
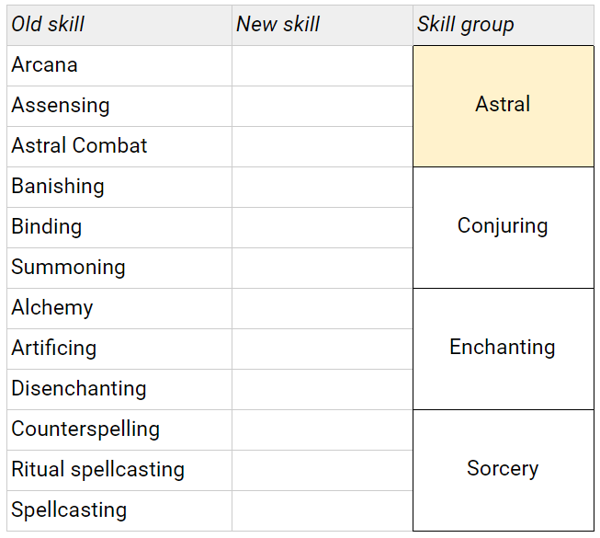
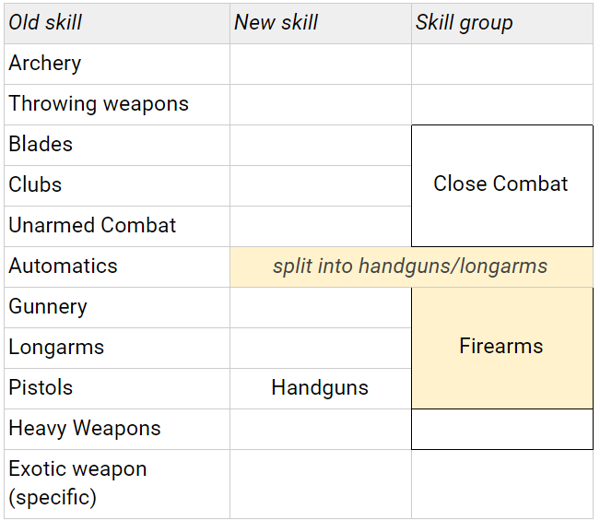
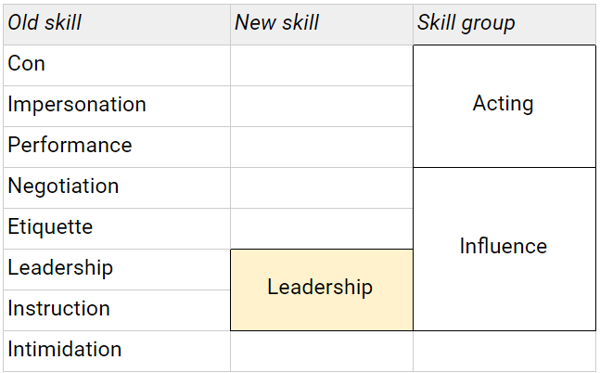
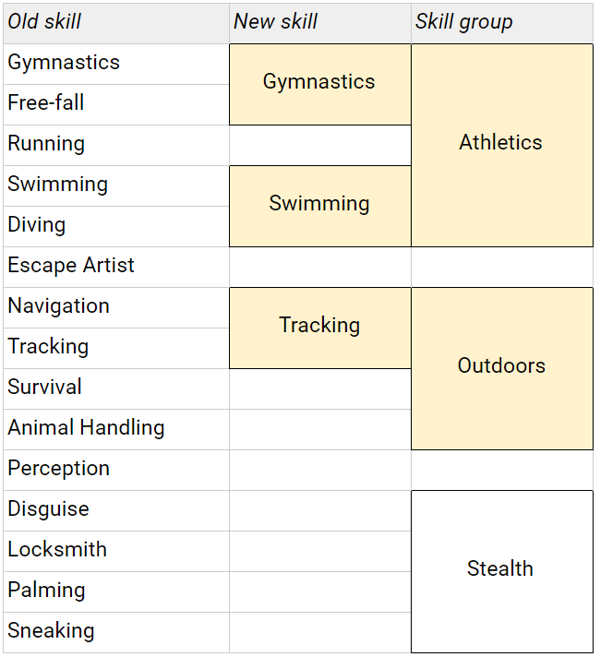
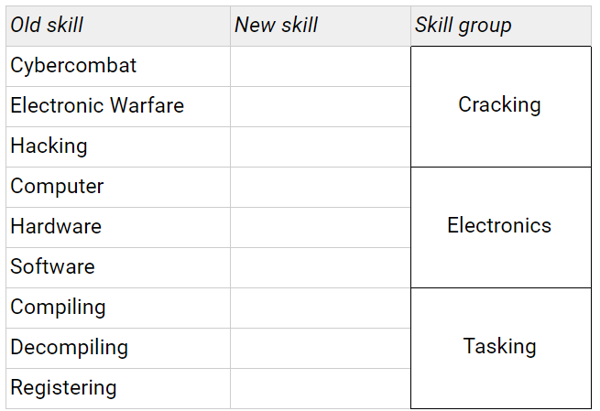
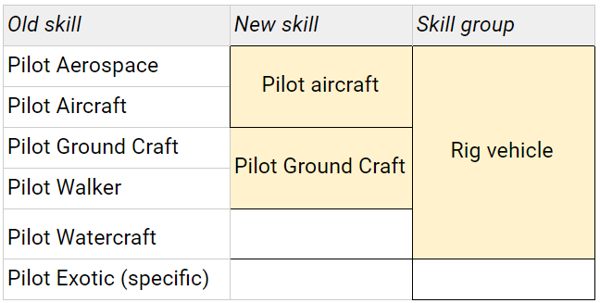
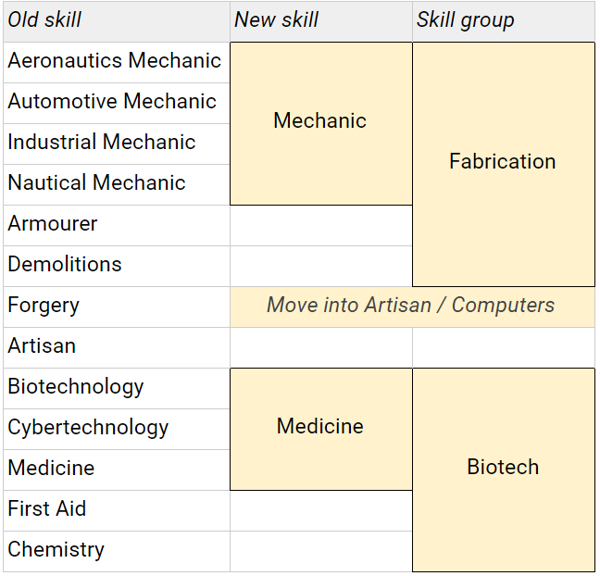
No changes to 5e’s RAW, so to summarise:
Non-goals: Radical upheaval that requires significant changes elsewhere in the system. I’ve mostly stuck to merging existing skills, rather than redrawing the boundaries of skill areas entirely.
These rules are canon for my current campaign.
After each mission, your characters will (usually) enjoy a downtime phase. During this phase, you get four “scenes” that you can allocate to activities as you please. You also have to pay one amount of your lifestyle costs.
You get two bonus scenes - so, six in total - if you have any of the following augmentations: sleep regulator bioware (CRB); metabolic control adept power (CRB); booster endosont symbiotes (CF pg 123) or hyper-glucagon geneware (CF pg 160).
Spending one scene can give you any of the below options and benefits. Note: almost all tests for activities should be resolved by buying hits, except for a few noted exceptions, and Edge cannot be used in downtime to effect test outcomes. Ask me if you’re not clear if you should roll or buy hits.
Also note: you have to spend at least one scene on Leisure. All work and no play makes Jack an unhappy shadowrunner. If something happens that prevents you from spending a scene on Leisure, you cannot heal stun damage or refresh your Edge pool. Yes, ouch.
A scene spent on leisure gives you:
You can save these karma points up, and you can combine them with regular karma to buy knowledge skills or qualities.
You gain 1 karma, to spend on whatever you want.
Convert nuyen to karma or karma to nuyen, at a rate of 2000¥:1. You can convert up to five points for one scene. You can only do this once per downtime phase.
Except where noted below, increasing skills or attributes doesn’t require any scenes. You pick it up on the job, so to speak. Knowledge skill increases never require a scene.
However, these increases do need some investment during downtime:
You spend time pitching your skills to do side jobs for your contacts and your contacts’ contacts. See calculation below. Most characters can earn 750-2000¥ for one scene spent on Side Hustle. You can only spend one scene on this; your contacts and their contacts only have so many opportunities for these sorts of off-the-books odd jobs.
See side hustle calculation for details on how to calculate the money earned.
Earn a number of Favour Markers equal to your Charisma. You can use these to pay off markers you owe or bank them against future times you ask the contact for help. You don’t need to declare which contacts the markers apply to now, you can hold them as a pool and use them for whichever contact you want later.
You should expect to have to owe contacts Favour Markers when you ask them for help during play. See TBD link
You can raise a contact’s loyalty by spending a number of markers equal to twice their new loyalty value. I will encourage you to do a bit of roleplaying around this event! However, note you cannot raise a contact’s loyalty if you owe them any Favour Markers.
Try and make a new contact, of any type you want.
Choose a contact rating for your new contact. Do an opposed test between your Charisma and the contact rating. If it succeeds, you find someone who will trust you enough to become a contact.
Yes, this means you’re unlikely to make friends above connection 3-5 this way. More powerful friends will need GM approval or to be made during normal play.
At the end of the downtime, the new contact will have loyalty 1.
One scene is enough rest to heal any amount of physical damage short of being in overflow. If the character went into overflow on the last run, it takes two scenes to heal up. If you have a medical support contract, this is free. Otherwise it costs one favour marker per scene used.
If you didn’t gain any notoriety during your last mission, you can spend 1 scene to reduce your notoriety by 1. You can only do this once per downtime phase.
First, find the base number of markers this is going to cost you, depending on the item’s price:
| Cost of item | Number of favour markers |
|---|---|
| Below 5000¥ | 0 |
| 5000 - 50k¥ | 1 |
| 50k - 100k¥ | 2 |
| 100k - 250k ¥ | 3 |
| 250k+ | 4 |
You have to pay these markers for anything you buy, even legal items. They represent the extra hassle of buying expensive items when you don’t legally exist.
Now, work out if you can get it. Each pass through this table takes one of your downtime scenes, except for the first row.
| Avail score (legal gear) | Avail score (R or F) | Outcome |
|---|---|---|
| Below 18 | Below 9 | You get it automatically. This doesn’t need you to use any scenes, either. You still pay markers as above. |
| 18+ | 8-12 | If you have any gear-related contact, you get it automatically; if not, you or any contact can roll. If you use a non-gear contact, this costs +1 marker. |
| 13-18 | If you have a gear contact specialising in this type of gear, you get it automatically. If not, you or any gear contact can roll (again, this costs +1 marker.) | |
| 18+ | A gear specialist contact can roll. This costs +3 favour markers. |
(These numbers err somewhat on the side of generosity.)
If the result is “can roll”, remember you are rolling against the availability of the item, as a dice pool. You can purchase extra dice on this test at a cost of 25% of the item per dice. Remember, for very big-ticket items (high-end cyberware, big vehicles, cyberdecks, etc) it can be more effective to negotiate to receive them as ‘run payouts rather than sourcing them through contacts.
If you have an appropriate skill (Hardware for Matrix damage, Mechanic for vehicle/drone damage, etc), you can repair up to your total dice pool in damage track boxes across any of your gear for one scene’s worth of your time. You can spend multiple scenes on this if your gear is really badly banged up.
You have to have access to a facility; either a Garage/Workshop/Facility in your dwelling or access to one via a contact.
There is no further cost; a supply of parts comes with the nuyen you paid for the garage/workshop/facility.
It takes time to have ‘ware installed, recover from the surgery, and then learn how to use your new abilities. This varies with how invasive the ‘ware is:
Take an extended test: Arcana + Intuition [Astral] (initiate grade, 4 scenes)
If you can’t get all of this done in one piece of downtime, you can “bank” the scenes you have spent and to return to it during the next downtime phase.
First buy the formula (see below.) Then resolve a test of (Spellcasting + Intuition) [magical lodge’s force]
Like most downtime actions, don’t roll actual dice, just buy hits.
Substitute in Ritual Spellcasting or Alchemy if that’s what you’re learning
Learning the spell takes two entire scenes, divided by the number of hits on the test. This means you can learn more than one spell in a single scene, as long as you have 4+ hits on the test. Other than that, you don’t get any sort of refund for part-used scenes, however.
You can create a number of trinkets equal to your Alchemy skill in a single downtime scene. See Reagents in the Magic section for more information.
NB: Regardless of resulting power, all the reagents you declared in step 1 are consumed.
See addiction houserules for full details on these.
You can’t combine indulge and rehab.
Each scene can be used for 60 hours of downtime to do things like binding spirits, enchanting, making gear, etc. Anything that needs extended tests in the book and isn’t mentioned above can be done via this scene.
Shadowrun has many, many qualities, and probably lots of them should affect the rules above. These are just the ones I’ve thought of so far.
Other qualities I think should affect these downtime rules, but I haven’t yet had a player take them so don’t have numbers at the moment:
First, choose a skill you are going to use to freelance. Find your highest relevant skill dicepool on this list:
| Skill | Base |
|---|---|
| Medicine, Biotechnology, Cybertechnology | 4 |
| Technical skills (except the ones above) | 3 |
| Pilot Aircraft, Pilot Aerospace, Pilot Exotic <br/> Sneak | 2 |
| Social Active skills<br/>Combat Active skills<br/>Professional knowledge skills<br/> Arcana <br/>Pilot Walker, Pilot Watercraft | 1 |
| Academic knowledge skills <br/> Pilot Groundcraft | 0 |
Add +1 to this for every rank you have in the skill over 4. Don’t include things like improved ability, reflex recorder, etc - just the normal skill score.
Add bonuses (these all stack):
| Skill | Bonus |
|---|---|
| One or more specialisations in your chosen skill | 1 |
| At least 4 ranks in any Influence skill (Leadership, Negotiation, Etiquette) that you are not using for the skill you are selling | 1 |
| At least 4 ranks in a skill related to the skill you have chosen | 1 |
| At least 4 ranks in 4+ skills related to the skill you have chosen | 1 (plus the 1 above) |
| Have a rating 6 fake SIN, or a real national/corporate SIN | 1 |
| You have a control rig & are using a vehicle skill | 2 |
| You have the Fame quality at National or higher level | 1 |
| Your best fake SIN is of rating 3 or below | -1 |
| No fake SIN, or your best fake SIN is rating 1 | -1 (plus the -1 above) |
| Lifestyle is Squatter | -1 |
| Lifestyle is Street | -2 |
Add all these together to get your multiplier.
Finally, work out how many hits you can buy in your chosen skill - that’s your dice pool, divided by 4, rounded down.
Each scene spent freelancing will earn you:
multiplier * bought hits * 50¥
Twitch the decker decides to do some computer freelancing on the side. He has the Software skill at 6, which is a Technical skill, so has a base multiplier of 3, plus 2 for his skill level. He also has four other computer related skills at rank 4 or above (giving +2). His final multiplier is 7.
His Software skill dice pool is 15, so he can buy 3 hits.
Each scene of freelancing will earn Twitch 7350 = 1050¥.
Blitz the rigger has a go too. She has Pilot Aircraft skill at 7, Agility 6, and a level 2 vehicle control rig. She has various other vehicle related skills, a specialisation in Pilot Aircraft, and Negotiation rank 5. Her multiplier is 11, her bought hits are 4, and so her earnings are 2200¥.
This is a fair bit of crunch but each character should only need to do it once.
Remember, characters can only spend one scene on doing this sort of work before there are no more opportunities to be done. They don’t have the right sort of criminal networks and reputation to find these jobs endlessly. If they did, they probably wouldn’t be shadowrunners.
Side hustle example activities:
I didn’t realise I wanted downtime rules until I looked at the ones from A Light In the Dark… then I immediately saw that I did. A few things didn’t fit though; they’re optimised for a living campaign, so they’re a bit too detailed in places and a bit too simple in others.
So I wrote my own, which you can read here.
I’ve never been completely happy with how I’ve handled downtime. It felt a little like an underbaked idea, a randomised tax the GM imposes; “well done for finishing that run. It’s now going to be… ummm, let’s say three weeks until your next one. Pay lifestyle costs. OK next run!” This system puts players in control, with a series of options they can pursue. Hopefully, the balancing works where all the options have their own attractions, without anything being overly powerful or creating a cognitive dissonance around “well, why are these people shadowrunners, then?”
I’ve tried to minimise dice rolling, including a speedy gear acquisition path that makes stuff easier to get hold off when the schedule isn’t tight. I’ve added a sort of resource currency for contacts, to represent the flow of favours back and forth to them, and hopefully give a little flavour of being part of a group of criminals. I’ve added zero-cost healing and repair options to recover between runs.
I’ve also taken the chance to buff a few things I feel are a little underpowered in RAW. Sleep regulators become quite potent, for example. Faces should shine here, able to butter up contacts for future favours as well as find new contacts more easily. People with good technical skills might make a non-trivial amount of nuyen on side hustles, which is more for feel and plot hooks than anything else.
Feedback welcomed! I’m still very much moving some of the numbers around, and trying to balance options against each other; I expect this will continue as it gets a proper playtest. But to tell me if you spot any egregious oversights or exploits.
For all the work I’ve done, this remains very closely based on these houserules for A Light In The Dark SR living campaign. All credit for any goodness here belongs to them. Anything you don’t like was probably something I added. More credit goes to u/mercilessming_, from whose houserules I derived further inspiration & the term “scene” which was much better than what I had before..
These rules are canon for my current campaign.
These rules introduce a simple currency for contacts: favour markers. Certain services from your contacts will cost markers; either instead of, or in addition to, nuyen.
Contacts will generally refuse to help you when you owe them more markers than they have Loyalty rating with you.
Markers are an in-universe concept; characters can talk about them. They can even be traded around (“You still owe me for that time in Cuba. But if you help my boy here out, we’ll be square. OK?”)
For each contact you should declare a speciality, an area of expertise. Some examples are below but feel free to ask for more if you feel these don’t cover something you want:
Contacts don’t generally have stats. Unless otherwise specified, when it says “roll” below, the roll is:
| Action | What the Contact Does | Cost |
|---|---|---|
| Legwork (Knowledge Skills) | Rolls vs threshold based on obscurity of knowledge | For Legwork contacts: free.Otherwise, 1 marker. |
| Legwork (Asking Around) | Rolls vs threshold based on obscurity of knowledge | For Legwork contacts: 1 marker.Otherwise, 3 markers. |
| Networking | Rolls vs threshold of the target NPC’s connection rating. Even on a success, you might only meet with a subordinate. | For Networking contacts, none. Otherwise, 1 marker. Arranging a meeting with dangerous people (like mafia dons or dragons) might cost more, at the GM’s discretion. |
| Gear | Rolls vs. Availability of item (opposed test, not threshold.) | For Gear contacts, see above. Otherwise, as above, plus 1 additional marker. |
| Services | Rolls their appropriate active skill or uses their special ability. | For service contacts, 1 marker for up to 8 hours of work. Otherwise, 3 markers per 8 hours. |
If you want to make use of someone else’s contacts, they need to pay the favour markers, not you.
These rules are not yet canon for my current campaign. Although simpler than RAW, they are still too complex, I feel.
(Unchanged from RAW; repeated here for ease of reference.)
Dry Addict (also in mild/moderate/severe/burnout levels, at 50% of the karma of the above qualities): must pass a composure test at thresholds 1-5 (depending on stress level) to turn down an offer of the addictive substance. Take a 1-4 dice pool penalty on addiction tests following use of substance.
| Addiction Threshold | Recovery Period | Addiction Period | Addiction Type | |
|---|---|---|---|---|
| Alcohol [*] | 2 | 1 | 3 | Both |
| Bliss | 3 | 1 | 3 | Both |
| Cram | 3 | 1 | 3 | Psychological |
| Jazz | 3 | 2 | 2 | Both |
| Kamikaze | 3 | 3 | 1 | Physiological |
| Long Haul | 1 | 1 | 3 | Psychological |
| Nitro | 3 | 3 | 1 | Both |
| Novacoke | 2 | 2 | 2 | Both |
| Zen | 1 | 1 | 3 | Psychological |
| BTL (Dreamchip) | 1 | 2 | 2 | Psychological |
| BTL (Moodchip) | 2 | 2 | 2 | Psychological |
| BTL (Personafix) | 2 | 2 | 2 | Psychological |
| BTL (Tripchip) | 3 | 2 | 2 | Psychological |
| Essence Drain | 2 | (Critter’s Magic)/3 | [*] | Psychological |
For the purposes of my campaign, I won’t be enforcing addiction rolls against soykaf, skillwires, simsense, or foci. I’ve removed them from the table above. I will only ask for rolls for addiction to alcohol when the character already has the qualities ie. an existing addiction can get worse but a character cannot acquire an addiction during play.
I’ve also deleted psyche completely. Deepweed has no addictiveness ratings in CRB, nor in any errata I can find. I’ve left it out for now.
Addiction Period is a new field, calculated as RAW’s “addiction rating” divided by 3. Recovery Period is calculated as (4-Addiction Period.) You can use these formulae to work out the stats for other drugs in SR5e not included above. That’s also how you calculate the values for Essence Drain addiction, should it come up.
When asked to roll an Addiction or Withdrawal test, the dice roll is:
If you have an addiction and start a mission after not indulging in your addiction during the last downtime, you must roll for withdrawal. Roll an addiction test as above. If you fail, you take an ongoing penalty on all rolls, according to your addiction level, as listed above. This will vanish immediately if you use the drug again.
If you use any addictive drugs during the mission that you do not already have an addiction to, make a note that during the next downtime you will experience cravings.
Drugs are more-ish. That’s kinda their whole deal.
After any use of an addictive substance, your character will crave it. This will last for a number of downtime sessions equal to the drug’s Addiction Period. Keep track of how many missions you use the drug on while this is happening.
At the end of the Recovery Period, make an Addiction Test. Subtract one from the drug’s Addiction Threshold for each entire mission where you didn’t use the drug at all. You cannot use Edge on this test. If you pass the test, the cravings end and you’re in the clear. If you fail the test, bad news: you now have the Addict (Mild) quality.
Characters with the Dry Addict quality take a penalty of -1 to -4 on this test, depending on the level of their former addiction. In addition, if they fail the test, they get the Addict quality at the same level as their Dry Addict quality, not at the Mild level.
If you pick up an addiction quality this way, you do not receive any karma for it.
Addictions place certain requirements on you between your missions, as per my downtime houserules.
You can choose to Indulge your addiction. This means you will suffer no ill-effects during your next mission. However, you lose a number of downtime scenes according to your addiction level:
Instead of indulging, you can go cold turkey: you will have to roll for withdrawal at the start of your next mission, and take the penalty for withdrawal if you fail (or choose to get a fix during your next mission.)
Finally, you can choose to rehab, for 1-3 scenes of time. Each scene will grant you +2 dice on your next Addiction Test. There is an escalating cost associated with this, as your character spends time in therapy, purchases detox meds, undergoes magical treatments, etc. In a given downtime phase, the first rehab scene costs 1000¥, the second costs 2500¥, and the third costs 10k¥.
After a number of consecutive downtime phases and missions during which you indulge your addiction equal to the drug’s Addiction Period, you must roll an Addiction Test. You cannot use Edge on this test. If you fail, the addiction gets one step worse (Mild -> Moderate, Moderate -> Severe, etc.) You do not gain karma for the worsening addiction. If you are at Burnout and fail this test, you stay at Burnout, but also permanently lose one point of either Body or Willpower - whichever is higher.
To get clean, a character must:
They can then swap the Addiction quality for Dry Addiction. They do not receive karma for this new negative quality.
After another period of (Recovery Threshold) downtimes of complete abstinence (ie. you cannot have rolled any Addiction Tests at all), they can once again pay karma (at 2x the cost of the Dry Addict quality) to remove that as well.
These rules are not currently canon for my current campaign.
Just as metahumankind’s understanding of magic has altered in the decades since it returned to the world - with the emergence of UMT providing a framework for understanding all magical traditions - so too does its understanding of the effect of cybernetic augmentations on the manaflow through an individual. The old theories - that cyberware was fundamentally antithetical to the flow of life force and that as cyberware increased so the subject’s essential humanity inevitably ebbed away - no longer hold true. Instead, a new, deeper understanding is emerging from theoretical thaumaturgists in leading research labs.
It is true that cyberware seems to disrupt the flow of mana being channelled for magic, and it continues to be the case that even small amounts of augmentation is devastating for an individual’s ability to wield magic. But studies of people receiving posthetic limbs or transgender surgeries revealed surprising results - if anything, their interaction with the mana flow improved as the physical reality of their bodies moved into closer alignment with their mental self-image. It now seems that the harmful side-effects of disrupted mana flow are not inevitable, and come not from some immutable law of nature but rather from conflict between the individual’s body and that internal sense of self.
Furthermore, that sense of self is not fixed, but can change over and time through the individual’s will.
For many of metahumankind, it remains harmful to take too much cyberware. On some deep level, their psyche rejects it. But there is an emerging trend of people who choose to see the world, and their place in it, differently. For these people, their relationship with the mana flow is altered in such a way as they can choose greater amounts of augmentation. Their self-image is that as they alter themselves, they are not straying away from what they were meant to be; rather, they move closer to it.
They do not become less than human. They become… something else, something different. Posthuman.
Posthuman is a quality that can only be taken post-chargen and only by characters whose current Essence is 2 or less. It costs 20 points of karma, plus 10 points per level (so 30 points for level 1, 40 for level 2, 50 for level 3…) Each level gives the user a 1-point essence “hole” they can choose to install cyberware, bioware, or other body modifications into without changing their current essence score.
Posthumanism does not mix well with awakened abilities. The total penalty to a character’s magic score is always equal to the sum total of the essence cost of all ‘ware installed, regardless of the Posthuman quality.
Posthumans pride themselves on the perfection of their altered bodies and should always seek to install the highest quality ‘ware they can. They also shun and pity cyberzombies, their twisted cousins, as unnatural creations.
These rules are mostly canon for my campaign (see sub-pages.)
First and foremost, to reduce book-keeping and confusion:
Second, to make some mechanical/balance changes:
Third, to explore an idea. With the exception of 4e, Shadowrun has always tightly coupled together two concepts: how soon in a turn a character acts (their initiative roll) and how much they can get done in a turn (how many passes they get.) These houserules decouples these and allows them to vary independently under some combinations of character abilities.
Unlike 6e-style “anytime” actions, which mean a character can use Major or Minor actions outside their normal phase, which means you need to keep track of how many they saved from their last phase. ↩︎
These rules are currently canon for my campaign. Although they are a bit experimental.
Initiative time is split into a series of turns, with each turn representing a few seconds of in-game time. During a turn, each character gets a phase in which to do their actions. The order in which characters get phases is determined by the initiative roll.
Each combat turn runs like this:
On their phase, everyone gets one normal Complex or two Simple actions as usual, and they might also get bonus Simple actions3 (see below).
Complex and Simple actions can be freely interchanged as usual (one Complex = two Simple and vice versa.)
A character’s normal Complex action can be used for any type of action, but their bonus Simple actions can only be used to perform specific types of action (physical / Matrix / magical), depending on where the character got the bonus actions from.
Each character can take a Free action on any phase, including their own. They can do this as many times during the turn as there are phases.4
What you roll is determined by “where” your character is:
| Where | Roll |
|---|---|
| In the physical world (including AR) | Rea + Int + 1d6 |
| In VR, cold sim | DataProc + Int + 3d6 |
| In VR, hot sim | DataProc + Int + 4d6 |
| Astrally projecting | (Int × 2) + 2d6 |
Summary table; discussion follows below:
| Bonus actions | ||
|---|---|---|
| Wired Reflexes / Improved Reactions (etc) | Rating 1 | +1 Simple (physical) |
| Rating 2 | +2 Simple (physical) | |
| Rating 3 | +3 Simple (physical) | |
| Drugs | None | |
| AR with DNI or cold-sim VR | +2 Simple (Matrix) | |
| Hot-sim VR | +3 Simple (Matrix) | |
| Initiated magician | Grade 1 | +1 Simple (magic) |
| Grade 2 | +2 Simple (magic) | |
| Grade 3 | +3 Simple (magic) |
Note that no metahuman brain can cope with the multiplicity of inputs of being active in more than one “world” at once. Hence, characters can receive bonus meatspace actions, bonus matrix actions, or bonus magic actions; but only one. If they are eligible for more than one at once, through whatever combination of gear/augments/spells/etc, they can choose freely when rolling for initiative which “world” is getting their attention and hence which bonus minor actions they will receive.
Characters can receive bonus physical actions via any sort of normal initiative augmentation: this includes wired reflexes, Improved Reflexes adept powers, and other cyberware, bioware, or magical initiative augments (including spells like Increase Reflexes). But not drugs; see below.
Example: Alice (streetsam, with Wired Reflexes III) and Bob (ganger) are fighting.
For every initiate grade from 1-3, mages get an extra Simple action that can only be used for magical actions (incl spellcasting, summoning, banishing, etc). This bonus applies equally in the physical world and while astrally projecting.
(Note that this means after their first initiation, a mage can summon a spirit (Complex action) and order it (Simple action) in a single phase.)
Bonus Matrix actions depend on the decker’s or rigger’s interface mode.
As usual, the bonus actions received can only be used for Matrix actions. These include driving tests if the character is piloting a vehicle via AR.
Drugs that increase your initiative roll do not grant extra actions. However, their effect does stack with extra actions gained from other sources. So an initiated mage using Kamikaze can go earlier in the turn and still use their normal Complex action and any bonus magical actions from initiating.
Obviously, combat drugs come with other downsides.
These rules eliminate multiple passes. ↩︎
Or keep the values same and start over without re-rolling as SR 6e does, if you prefer. I like the dynamic feel of re-rolling each turn though. ↩︎
These bonus actions replace the multiple passes mechanic of normal Shadowrun 5e. ↩︎
This restores how Free actions worked in older editions of Shadowrun. It faciliates team communications via the “speak/text/transmit phrase” option. I don’t think there are any game balance consequences to speak of, but we’ll revisit this rule if I’m wrong. ↩︎
Characters move at different rates, measured in the number of metres they travel during their phase.
Assuming there is some nearby suitable object, this grants the in cover bonus (+2 or +4 to defence rolls) until the character moves again. Note they might get flanked, though.
Drop to the ground or get back up again2.
You can do as many attacks, during your turn, as you have actions to spend; the only exception is for single-shot (SS) weapons, which can only be used to attack once per turn4.
Recoil is no longer tracked across turns, but it does apply (in total) across all the attacks done within a single phase.
If the attacker has either:
or:
…then they can use a new type of multiple attack, Carnival of Carnage.
To use CoC:
Note that you cannot use Carnival of Carnage to attack one target multiple times.
This is deliberately a fair bit less than RAW for many characters. My table plays theatre-of-the-mind and we hardly ever have accurate grids during combat. So I wanted there to be a clearer difference between ‘walking’ and ‘running’ rates. ↩︎
I have removed the requirement to pass a test to stand up if the character is wounded. ↩︎
This is changed from RAW; I have removed the Quick Draw action and instead made quick draw holsters a Free action. Larger weapons become a Complex action rather than a Simple to ready up. ↩︎
Although you can dual-wield them and attack once per turn per weapon, if you wish. ↩︎
Shoutout to the rad action movie RPG Feng Shui, from whence I stole this name. ↩︎
All the vehicle actions listed below count as Matrix actions for any character using AR or VR, and thus can be done with a character’s bonus Matrix actions.
TODO(check CRB pg 202-203)
The SR5 core rulebook has 37 normal actions plus 9 magic actions. It also has 42 Matrix actions. Kill Code adds another 11. This is too many. See my matrix houserules for a streamlined set.
When a rigger is jumped in, Control Vehicle becomes a Free Action ie. a rigger no longer needs to spend one Complex action per turn to stop the vehicle going uncontrolled. This is only true when jumped in, and jumped in continues to require VR.
Activate focus (Simple)
Shift perception (Simple)
Astral projection (Complex)
Summon spirit (Complex)
Call bound spirit (Simple)
Command spirit (Simple)
Banish spirit (Complex)
Dismiss spirit (Simple)
Reckless spellcasting (Simple)
Cast spell (Complex)
Remove Reckless Spellcasting (the ability to cast a spell for a Simple action at +3 drain.)
Spell defence now requires a Simple action to declare, which must be a deferred action from the mage’s last phase. However, it protects up to (Magic Rating) targets, all of whom get the mage’s full Counterspelling skill to add to their spell defence dice. This can be done as many times as the mage has actions.
There are two different systems for interrupt actions here; one is the ones we are currently using. The other is a more radical system that uses Edge instead of changing initiative score. These are not currently in use.
These rules are currently canon for my campaign. Although they are a bit experimental…
Interrupt actions no longer change your initiative score by -5 or -10 when taken. Instead:
Example: Alice (streetsam) and Bob (ganger) are still fighting.
These rules are not currently canon for my campaign. Although I plan for them to replace the rules above in time.
TODO
Like:
Or:
| Spellcasting | Summoning | |
| 1 Simple action | Force <= Magic/2 | |
| 1 Complex action | (in between above and below) | Force <= Magic/2 |
| 1 Complex + 1 Simple | Force > Magic | (in between above and below) |
| 2 Complex | Force > Magic |
| Dancer | ||
| Old rules (RAW) | Proposed new rules | |
| Initiative roll | 12+3d6 | 12+3d6 |
| Phases per turn | 74% chance of 3x 26% chance of 2x | Always 1x |
| Actions per phase | 1 Complex | 1 Complex (anything) +1 Complex (physical) |
| Max attacks per turn | 2x or 3x | 3x |
| Eddie | ||
| Old rules (RAW) | Proposed new rules | |
| Initiative roll | 9+1d6 | 9+1d6 |
| Phases per turn | 83% chance of 2x 17% chance of 1x | Always 1x |
| Actions per phase | 1 Complex | 1 Complex (anything) +1 Simple (magical) |
| Mr Atom | ||
| Old rules (RAW) | Proposed new rules | |
| Initiative roll | 10+1d6 | 10+1d6 |
| Phases per turn | 2x | 1x |
| Actions per phase | 1 Complex | 1 Complex (anything) |
| Max attacks per turn | 2x | 1x |
| Project: Heartbreak | ||
| Old rules (RAW) | Proposed new rules | |
| Initiative roll | 9+1d6 | 9+1d6 |
| Phases per turn | 83% chance of 2x 17% chance of 1x | Always 1x |
| Actions per phase | 1 Complex | 1 Complex (anything) |
| Max attacks per turn | 2x | 1x |
| Twitch (physical) | ||
| Old rules (RAW) | Proposed new rules | |
| Initiative roll | 14+3d6 | 14+3d6 |
| Phases per turn | 0.5% chance of 4x 83.3% chance of 3x 16.2% chance of 1x | Always 1x |
| Actions per phase | 1 Complex | 1 Complex (anything) 1 Complex (physical) |
| Max attacks per turn | 2x - 4x | 4x |
| Twitch (matrix AR DNI / VR cold sim) | ||
| Old rules (RAW) | Proposed new rules | |
| Initiative roll | 14+3d6 | DataProc+6+1d6 |
| Phases per turn | 0.5% chance of 4x 83.3% chance of 3x 16.2% chance of 2x | Always 1x |
| Actions per phase | 1 Complex | 1 Complex (anything) 1 Complex (Matrix) |
| Max attacks per turn | 2x - 4x | |
These rules are not yet canon for my campaign.
Factors effecting: visibility (rain/fog/smoke), light level (darkness/glare), wind
Penalties stack across categories eg. if it’s dark and there’s fog it’s -8. Compensation does not stack within a category eg. if you have low-light cybereyes plus thermal vision goggles, you take -2.
Define weapon rages as:
Take penalties as follows:
| Hand | Close | Near | Far | Extreme | |
|---|---|---|---|---|---|
| Pistol, Taser | 0 | 0 | -4 | no | no |
| SMG | 0 | 0 | -2 | no | no |
| Shotgun | -2 | 0 | -2 | no | no |
| Rifle | -2 | 0 | 0 | -4 | no |
| Sniper rifle | -4 | -2 | 0 | -2 | -4 |
| Machine gun, Assault cannon | -4 | -2 | 0 | -4 | -6 |
| Bow, crossbow | -4 | 0 | -2 | no | no |
| Grenade launcher | no | 0 | 0 | -4 | no |
| Rocket launcher | no | no | 0 | -2 | no |
| Missile launcher | no | no | 0 | -2 | -2 |
| Thrown | 0 | 0 | -4 | no | no |
This is the magic rebalance section. In addition to the specific sections below, here’s a few generic notes:
I believe that, per RAW, the enchanting rules are very weak and uninteresting. They need a ground-up rewrite if they are to be as useful as spellcasting or summoning.
Mystic adepts, like magical adepts, must choose one of the three magical skills to specialise in: spellcasting, summoning, enchanting. They cannot do the other two.
Even with this change in place, I suspect mysads are still over powered. This is a start though.
Large swathes of these rules owe debt to: Lormyr for this post and this post (see also this thread) (and this post) u/dezzmont for these (quite radical!) suggestions
Something else I’d like to tackle but haven’t currently found a way: give physads a different mechanical feel to “samurai, but magic” and also give them more benefit from the (expensive) decision to increase their Magic attribute versus just initiating again and again and taking the Power Point metamagic. I am considering doing this by allowing them to take more powers than they have power points and swap them in and out in a ritual process that takes several hours. This would give them some role flexibility that cybernetic characters couldn’t match.
These rules are canon for my current campaign.
Binding a spirit now requires the creation of a binding trinket, consuming a number of drams of reagent equal to the spirit’s force. No extra roll is done for this, it’s just part of the binding process. As with other trinkets, this lasts a few weeks but then fades away, releasing the spirit. Binding is no longer permanent.
You have to have the associated trinket on your person to call the bound spirit.
At any time, a summoner can bind a number of spirits with a total force equal to 2× their Charisma.
Remove the following bound spirit services:
Change Aid Alchemy, Sorcery and Study: instead of a flat bonus to your roll equal to the spirit’s Force, treat this as a standard Shadowrun teamwork roll. The spirit rolls (2×Force) dice. Each hit on that test contributes a bonus die to the magician’s test and raises the mage’s limit by 1. The maximum number of bonuses is equal to the magician’s skill rank.
Example: Alice the mage has summoned Bob the Force 4 fire spirit. Alice asks Bob to help her cast a Fireball. Alice has Spellcasting 4 (she’s a novice.) Bob rolls F×2=8 dice, scoring 5 hits (lucky Bob!). That would get Alice 5 bonus dice, but she has Spellcasting 4, so she can only get 4 dice.
thanks to u/mitsayantan for this idea. ↩︎
These rules are canon for my current campaign.
Idea to discuss but don’t yet have full rules for: foci can be attacked via Astral combat. After a certain amount of damage, their link to their user is disrupted. The focus can no longer be used until it is re-bonded to the user in the usual way (ritual + karma cost.)
A Power focus adds its Force to the user’s Magic attribute, and hence all spellcasting and summoning dice pools.
| 5e RAW | Houserule version | |
|---|---|---|
| F1 | 6 karma, 18 k¥, 4R | unchanged |
| F2 | 12 karma, 36 k¥, 8R | 12 karma, 72 k¥, 14R |
| F3 | 18 karma, 54 k¥, 12R | 18 karma, 162 k¥, 21R |
| F4 | 24 karma, 72 ¥, 16R | 24 karma, 288 k¥, 28R |
For spell foci: for one school of magic (chosen at time of binding the focus), it adds its Force to the dice pool used for one of spellcasting, ritual spellcasting, or counterspelling. Or it can sustain a spell from the chosen school of Force less than or equal to the Force of the focus.
For spirit foci: for a specific type of spirit (chosen at time of binding the focus), it adds its Force to the dice pool used for summoning, banishing, or binding that type of spirit. Or it can be used to increase the user’s Magic rating by its Focus rating for the purposes of determining the maximum total Force of spirits that can be summoned at once.
| 5e RAW | Houserule version | |
|---|---|---|
| F1 | 2 karma, 4 k¥, 3R | unchanged |
| F2 | 4 karma, 8 k¥, 6R | 4 karma, 16 k¥, 12R |
| F3 | 6 karma, 12 k¥, 9R | 6 karma, 36 k¥, 18R |
| F4 | 8 karma, 16 k¥, 12R | 8 karma, 64 k¥, 24R |
| 5e RAW | Houserule version | |
|---|---|---|
| F1 | 3 karma, 7 k¥, 4R | unchanged |
| F2 | 6 karma, 14 k¥, 8R | 6 karma, 28 k¥, 14R |
| F3 | 9 karma, 21 k¥, 12R | 9 karma, 63 k¥, 21R |
| F4 | 12 karma, 28 k¥, 16R | 12 karma, 112 k¥, 28R |
| 5e RAW | Houserule version | |
|---|---|---|
| F1 | 3 karma, 9 k¥, 3R | unchanged |
| F2 | 6 karma, 18 k¥, 6R | 6 karma, 36 k¥, 12R |
| F3 | 9 karma, 27 k¥, 9R | 9 karma, 81 k¥, 18R |
| F4 | 12 karma, 36 k¥, 12R | 12 karma, 144 k¥, 24R |
Not currently sure. Might make them the same as power foci.
I cannot imagine why any PC would ever want one of these, so I haven’t houseruled them yet.
These rules are canon for my current campaign.
Trinkets are small objects that are linked to the caster’s tradition or personality in some way and can offer a one-time boost to a magic test. They are crafted by using reagents:
NB: Regardless of resulting power, all the reagents you declared in step 1 are consumed.
Similar to foci, trinkets can be used to add a number of dice equal to their force to any given magic roll. Unlike foci, trinkets burn out after one use. You do not need to declare how a particular trinket will be used until you come to use it.
Unlike foci, trinkets do not have their own aura on the astral when not being used; they can be noticed but only if someone assenses your aura (and they can be disguised by Masking in the usual way). Therefore carrying one does not immediately mark one out as a magician to anyone who glances at you on the astral plane; they have a stealth advantage over foci. If a trinket is actively sustaining a spell, it can be seen at a glance, however.
A magician can only bind a number of trinkets at once equal to their Magic attribute.
These rules are canon for my current campaign.
My v1.0 Matrix houserules are based on a backport of most of the new ideas from Shadowrun 6e to 5e, while maintaining as much of the original system as possible. These are (hopefully) going to be replaced by the other Matrix rules presented here. These rules are also canonical for my currently campaign. For now, you can read my backport rules here.
The rest of this section represents an early draft of my v2.0 houserules, which further builds on the backport to streamline some areas.
These rules are not yet canon for my current campaign, as they are incomplete. But I hope to finish them soon (at least to a playable state.)
Note that these rules are intended to be used in conjunction with my re-written Matrix fluff.
Some loose, probably incomplete notes on what I’ve changed and why.
Changes intended to make the fluff and mechanics align better:
Changes intended to make play faster by either reducing steps to resolve outcomes or making the steps easier to remember:
Changes intended to increase player flexibility or offer players hard choices between trade-offs:
These rules are not yet canon for my current campaign.
This is covered in more detail in Matrix fundamentals in my fluff writeup, but a quick summary:
Unchanged from RAW; used as a combination of limits for tests and part of a dice pool for resisting tests done against you.
Every Matrix-enabled device - and in the Sixth World, that’s a lot - is represented in the Matrix by an icon.
Some of these are persona devices: these are the subset of devices that can let people get onto the Matrix, in the process creating a persona so they can interact with other devices. Examples include commlinks, cyberdecks, and RCCs.
When you sign into the Matrix via a commlink, cyberdeck, or RCC, the device gets a special icon called a persona. Personas are your own personal digital mirror image. Persona’s appearances are often very elaborately customised, particularly by wankers.
You cannot steal anyone else’s persona, nor can you have two personas at once. (More on why here.)
“Spotting” is the process of your persona device becoming aware of some other device’s icon so it can show it to you.
Spotting is an automatic function of basic Matrix protocols within a short horizon; typically around 100 metres, although it can vary with network conditions (more noise = shorter range). Your device is constantly keeping track of these devices as it helps to route traffic around in the local mesh. To detect icons further out, you can instruct your commlink or cyberdeck to actively monitor local mesh connections. See Matrix Perception, below.
Cloud hosts are always spotted, from anywhere on the planet. Local hosts are spotted the same as any other device.
Once your persona has spotted an icon, it receives an approximate physical location and direction of travel for it, typically accurate to a couple of metres but can randomly vary. In AR, this positioning information is used by your commlink/deck/etc to decide where in your vision to place the icon. In VR, your device will probably play a little looser with reality, and icon positions will be optimised for usability (for example, overlapping icons will be spread out a bit to make them easier to see.)
For more information on the in-universe experience of spotting icons in AR and VR, see Spotting & Positioning.
Once a persona has spotted an icon, they can keep track of it as long as it is within local mesh range. They will automatically get an approximate physical location and direction of travel, and if they also have (hacked or legitimate) access they can make that perfectly accurate via Trace Icon actions. If someone knows or suspects they are being tracked this way, they have a few options to escape:
Note that rebooting your device is not enough to break spotting, but the persona being tracked could turn all their devices off completely instead.
Devices can choose to remove themselves from the local mesh, refusing incoming connections and effectively vanishing from sight. This is called running silent.
A naked device, outside of a PAN or WAN, cannot run silent. Any PAN or WAN can freely choose to run silent, however this setting applies simultaneously to all devices in the PAN or WAN. If the PAN controller is a commlink, without a Sleaze stat, it will remain very easy to detect.
TODO
“Naked” devices - low-end things connected directly to the Matrix - are notoriously at risk of being hacked. Most people therefore protect their stuff by creating a Personal Area Network (PAN) and using their commlink as a shield against incoming hacking attempts.
Personal Area Networks - PANs - are local networks of devices all sheltered under a controller. The controller must be a device running a persona, so a commlink, cyberdeck, or RCC. The controller monitors all traffic within the PAN and between the PAN and the public Matrix, guarding against hack attacks.
PANs always run across the local mesh part of the Matrix, and have a restricted range to around 500 metres, depending on local network conditions (it gets smaller if the area is noisy). Devices that pass out of range will drop off the PAN. (Note that riggers can extend their PAN to greater ranges for drone control, as their RCCs have heavy-duty antennas. This also makes them physically bulky however.)
PANs can have dozens of devices attached to them; for most game purposes it isn’t worth keeping track of.
A device in a PAN can choose to roll the PAN controller’s device rating and the PAN controller’s ASDF stats instead of its own to defend against any Matrix action. However, it does not have to do so, eg. if it has a better Firewall stat than the controller does.
Wide Area Networks - WANs - are very similar to PANs, but the controlling device is a host instead.
Like PANs, WANs only work on the local mesh, so have a restricted range and must be controlled by a local host. Cloud hosts cannot be PAN controllers.
WANs have essentially no limit in how many devices can be attached to them.
It is common for WAN controller hosts used in wageslave offices to be running silent and also protected by RF-blocking building measures. See spotting for more information.
Your persona can have three different access levels to any given device, host, PAN, or WAN on the Matrix:
These access levels apply to an entire PAN or WAN at once. If you have User access to a PAN, you have User access to every device connected to that PAN. If your persona is running on a device controlling a PAN, then you have always have Admin access to everything in the PAN.
If an attacker can achieve a direct, physical connection to a device that is part of a PAN or WAN, they can bypass most of the protections. The device must roll its own Device Rating against the hacking attempt, and it is treated as having a Firewall stat of 0.
This is doubly dangerous, as from that compromised device the attacker can move into the rest of the network. Any access levels obtained on the device apply to the entire PAN or WAN.
Direct connections are not always easy to obtain. For many secure devices that use wireless connections to their hosts (eg. an external camera or maglock), they may only be present as physical connection points on the internal mechanisms, hidden behind reinforced casing. These are difficult to jerry-rig.
Some secure devices use wired connections to their WANs instead. These devices are impossible to wirelessly hack, but the tradeoff is that it’s much harder to armour their controlling cables and hence a lot easier to attackers to get a physical backdoor.
To achieve a direct connection, roll Hardware + Logic:
These are not hacking rolls, and there are no implications for OS tracking etc.
If a decker is listening in to an active connection (can be a voice call, a video stream, a text message chat, etc) via a Snoop action, they gain extra opportunities to hack remote targets by inserting hacking commands into the datastream.
Unlike other hacking attempts, they do not need to spot their target for this, so they can use this vector to hack one end of a phone call, then hack the device at the other end, even if it not within the decker’s local mesh.
These rules are not yet canon for my current campaign.
All resistance rolls below are expressed as an Attribute plus one of the ASDF stats. However, this only applies when the defender is a persona. When it is a host or device, substitute values for the roll as follows:
Determine threshold and base time as below. Hits over threshold used to divide the base time. If the test fails, the character spends the full time looking before coming up empty-handed.
| Threshold | Time | |
|---|---|---|
| General knowledge / public | 1 | 1 min |
| Of limited interest / not publicised | 3 | 30 min |
| Hidden / actively hunted & erased | 6 | 12 hrs |
| Protected / secret | N/A | N/A |
Suggested dice pool mods:
When looking for specific files inside a host, use thresholds as above. The base time is always 1 minute.
To spot nearby silent running icons on the local mesh: do an opposed test as above (ie against the icon’s Logic+Sleaze.) The decker rolls once against every silent running icon, and spots all the ones that fail the test in one go.
Repeated attempts within a short period of time take a cumulative -1 penalty, as usual.
To examine a device, roll a simple test. Each hit answers one question from CRB page 235.
Roll: Hacking + Logic [Attack] or [Sleaze] Resist: Willpower + Firewall
Roll: Hacking + Logic [Attack] Resist: Willpower + Firewall
Roll: Hacking + Logic [Sleaze] Resist: Willpower + Firewall
Ideally, the decker first does Probe to scout the target for security vulnerabilities: roll as above, take net hits, split into two groups as decker wants.
To actually hack the system the decker does Backdoor Entry to use the discovered vulnerabilities to get access. Same test as above.
Probe opposed test has 4 net hits. Decker uses 2 hits to reduce the time, keeps the other 2 hits back. The Probe action takes 30 minutes.
Decker rolls for Backdoor Entry and gets 4 net hits, choosing to take Admin access. They’re not maintaining access to any other systems. Later, the decker has to use a Data Spike against hostile IC. That would normally start the Overwatch Score clock, but the decker has 2 Combat Turns before that happens because of the Probe result.
If the decker then goes on to Brute Force a second system, the OS score starts counting up immediately, including for the first system that was hacked via Probe.
Roll: Cybercombat + Logic [Attack] Resist: Willpower + Firewall
Ways to deal damage or crash software. These are all Complex actions.
Data spike: does (net hits + Attack) boxes of Matrix damage, resisted by the target with Device Rating + Firewall.
Popup (requires User access): Target must be a persona using AR. Flooded with Matrix spam. Takes (net hits) as a negative ongoing dice pool penalty to all tests until the end of the next turn.
Denial of Service: Target is one or more specific devices. Target’s data streams are polluted with noise. Take 2*(net hits) as an ongoing penalty to all use of the device until the end of the next turn.
If the decker has no access, this can only be used against a single device. If the decker has User access to a PAN or host, it can be used against up to 3 devices that are in that PAN/WAN. If the decker has Admin access, it can be used on 6 devices.
“Devices” can include smartguns and cyberware. If a given action is affected by Denial of Service more than once - eg. if DoS is used against a character’s cybereyes, and cyberarm, and smartgun - then the penalties stack.
Roll: Computer + Logic [Data Processing] Resist: Willpower + Firewall
Once you have access on an icon (or the PAN/WAN that it is part of), you can do the following actions to it without any further tests.
If you have User level access:
Edit file (no test, Complex action) - create, change, copy, delete, or protect any type of file.
Note that some of these actions (particularly copy) may not complete instantly. The decker doesn’t need to spend any other actions, but they may need to wait.
If the edit is particularly intricate or tricky, GM may call for a test of Computer + Logic [Data Processing] vs a threshold to determine how successful it was.
Send message (Simple action) - send a message to a person or an order to a drone or other semi-smart device. Can be textual, audio, a picture, or a short video clip.
Control device (Simple/Complex depending on what you’re doing) - may require a test depending on what the goal is eg. shooting a turret requires a Gunnery roll. Control Device cannot override the neural connections used control cyberware.
If you have Admin level access:
Some actions still need tests however. These both need User level access to the file in question:
TBD
Roll: Electronic Warfare + Logic Resist: Willpower + Firewall
These are all Complex actions.
Snoop (no access required): listen in on the link between any two or more devices. Can be used to monitor a video feed, listen to an audio call, intercept commands sent to drones, etc.
Note that if you have Admin access to any device in the link, you can perform Snoop without any test being required. You only need to roll the above test if you do not have access to the devices.
Once you have performed Snoop, you can also insert hacking commands into the datastream to hack the remote device. This can even be achieved if the remote device is outside of local mesh range. Roll Probe/Backdoor Entry/Brute Force as normal.
Spoof Command (no access required): send a single command to a device, carefully constructed to look like it came from a legitimate source. See below for discussion.
Subvert Infrastructure (requires User access): Take control of up to (net hits) simple infrastructure devices connected to the PAN/WAN. Control continues as long as the decker maintains access to the host. Examples of devices include traffic lights, vending machines, home appliances, desk lamps, etc. Different commands can be issued to multiple devices for a single Simple action.
Squelch (no access required): prevents target device from calling or sending any messages for (net hits) number of minutes. If the target is a host subsystem, it prevents alerts leaving that subsystem and deploying IC in other subsystems for (net hits) combat turns.
Spoofed commands are considered to have User level access, not Admin. This causes some limitations in what you can do with Spoof Command, such as:
But some things you cannot do with Spoof Command:
Stats are unchanged from RAW; Cyberdecks have an attribute array that can be allocated across the four Matrix stats. Takes a Free action to swap any two stats. Remember you can only do one Free action per turn. If you want to do more reconfiguring than that, you can use Matrix Simple Actions.
Cyberdecks are reduced in price to 25% of RAW. See the gear houserules for more information and statblocks.
Maybe
Typical device ratings:
Devices from rating 4 up might run additional protection software that grants a further +2 to +4 to its Firewall stat.
Unattended vehicles with active GridLink subscriptions automatically connect to a GridLink firewall service, giving them +2 to Firewall.
| Naked device | Vehicle | Commlink/PAN | Host | |
|---|---|---|---|---|
| 1 | 2 / 0 | 2 / 0 | ||
| 2 | 3 / 0 | 4 / 1 | ||
| 3 | 5 / 1 | 7 / 1 | 6 / 1 | 8 / 2 |
| 4 | 6 / 1 | 8 / 2 | 8 / 2 | 10 / 2 |
| 5 | 8 / 2 | 10 / 2 | 10 / 2 | 12 / 3 |
| 6 | 9 / 2 | 12 / 3 | 14 / 3 | |
| 7 | 14 / 3 | 16 / 4 | ||
| 8 | 18 / 4 | |||
| 9 | 20 / 5 | |||
| 10 | 22 / 5 | |||
| 11 | 24 / 6 | |||
| 12 | 26 / 6 |
First number is the dice pool, second number the bought hits.
For more information, see Matrix fundamentals.
xxx
Why don’t the corps put all their valuable secrets on impregnable cloud hosts, outside of the grasp of shadowrunners? Sadly for the corps, it’s not that easy.
xxx
Many larger local hosts are internally divided into different subsystems. Each subsystem has a different purpose and different access levels.
For example, a corp R&D facility might have:
In game terms, each subsystem is treated as a separate host in terms of hacking rolls. Access levels are per-subsystem. Completing a hack on the general host doesn’t give access to the security subsystem, and so the invading decker needs to complete a second round of hacking. However, for the purposes of Overwatch Score accumulation, the entire host is tracked as one value. For example, if a decker has Admin access to the secure file storage subsystem and User access to the general host, it’s still only +2 OS per turn.
Note that there is no “map” of these hosts; the internal architecture is flat. Any user can see all the subsystems at once and move between them with ease.
When most hosts are not in an alert state, they are only running patrol IC (see below.)
Once a host is in an alert state (same conditions as tracking OS - a failed sleaze action or any attempted attack action), it starts deploying attack IC:
IC stats:
TODO
The Grid Overwatch Division is the Matrix police. TODO: MORE
Overwatch is a 12-segment clock. This clock is public, ie. the decker player can see it. (Delete: baby monitor program, check OS action.)
The clock ticks up when:
The clock resets only when the deck reboots and the decker’s persona logs off entirely. The decker loses all access to systems at that time, although any vulnerabilities discovered through Probe and not yet used for Backdoor Entry remain active.
Once the clock fills, GOD is alerted to the decker. A demi-GOD agent starts hunting them.
At the end of each turn, the demi-GOD rolls a number of dice equal to the clock vs a resistance from the decker of Intuition + Sleaze. If there are any net hits, the decker suffers convergence immediately. If there aren’t, the number of hits rolled (not the net hits) are added to the clock, and the demi-GOD will roll again at the end of the next turn.
Same as RAW:
Convergence does not change if the persona is in a host or not when it happens.
GOD is run by the Corporate Court and staffed by loaned headcount from all the AAA megacorps. Despite that, the corps do not completely trust it. They worry about a demi-GOD who is loyal to their parent corp using their position to leak information back to them. (Of course, they also attempt to convince their own demi-GOD agents to do the same. In practice, GOD keeps its deckers on very short leashes, so this rarely works - but not never.)
As such, the corps sometimes take measures to keep their darkest secrets outside of GOD’s purview. This can include:
Riggers!
These rules are not canon for my current campaign.
All vehicular action happens in one of two types of environment:
As vehicles travel, the type of environment may change. Characters may seek to use this to their advantage by steering the action to an environment that favours them and their vehicle.
All vehicle driving checks use Intuition when a rigger is jumped in. Reaction continues to apply for vehicles being piloted in AR or via physical controls.
As per RAW, stunts are an unopposed driving tests with a threshold of between 1 and 4+, depending on difficulty of the manoeuvre being attempted. Stunts are always limited by Handling, even in speed environments.
When a vehicle is attacked - either shot at or rammed - we need a dice pool to defend against that damage. What this dice pool should be is pretty unclear from RAW. I am borrowing the below wholesale from A Light In The Dark; that link has further discussion about why they made these choices.
A vehicle can only roll this test if it is in motion. Stationary vehicles do not get a defence test.
A person controlling a vehicle manually must spend at least one Complex Action per turn on a Control Vehicle action, otherwise they will lose control of the vehicle at the end of the turn. Uncontrolled vehicles impose -2 dice pool penalties on all occupants as they skid around, and will either be brought under control by the autopilot or crash.
However, if the driver is controlling the vehicle via AR and choose to receive two bonus Matrix simple actions, they can use those actions to control the vehicle, effectively doing so for “free.” This does mean they cannot receive any bonus meatspace actions, however. See the action economy page for more information.
A jumped-in rigger can do their Control Vehicle for a vehicle with a Free action.
Filling a vehicle’s damage track does not destroy it; it immobilises it. Hence repairs are cheaper.
Jerry rig - mechanics roll, same mechanics as First Aid but for removing boxes of vehicle damage to get it running again, takes a few minutes (extended test?)
shooting: choose to shoot at passengers (use cover/barrier rules, no damage to vehicle) or shoot at vehicle (counts as called shot, -4 penalty, does damage to vehicle’s damage track as normal)
First, work out the impact speed:
Second, roll to hit:
There is no clean miss here. If the defender gets more hits, they can still end up damaging the attacker - keep following the below.
Third, work out the damage code done to the defender: take attacking vehicle’s Body, subtract defending vehicle’s Body (minimum 1.) Add attacker’s net hits. Multiply by the impact speed. This is the number of boxes the defending vehicle has to soak with Body + Armour.
Fourth, work out the damage code done to the defender: take defending vehicle’s Body, subtract attacking vehicle’s Body (minimum 1.) Subtract attacker’s net hits. Multiply by the impact speed. This is the number of boxes the attacking vehicle has to soak with Body + Armour.
Alice is jumped in and driving a Ford Americar (Body 8, Armour 4, Acceleration 2) and tries to ram Bob who’s riding a Suzuki Mirage (Body 5, Armour 6, Acceleration 3). It’s a Handling environment. Bob is trying to get away, so we use the difference in the stats.
Alice rolls Int+Pilot+VCR and gets 4 hits, Bob rolls Rea+Pilot and gets 2 hits. The impact speed is only 1, as Bob’s bike is faster.
Bob’s Mirage now has to take damage: the difference between the Body stats is 3, plus 2 net hits, times impact speed 1 = 5 boxes of damage, soaked with 11 dice.
Then Alice’s Americar has to take damage: the difference between the Body stats is -3, which becomes 1, minus Alice’s net hits means she takes no damage.
This time, Alice tries to ram Bob in a head-on collision. This time the impact speed is 2. Same test result: 2 net hits to Alice.
Bob’s Mirage now has to take damage: the difference between the Body stats is 3, plus 2 net hits, times impact speed 2 = 10 boxes of damage.
Then Alice’s Americar has to take damage: the difference between the Body stats is -3, which becomes 1, minus Alice’s net hits means she takes no damage.
crashing (like ramming but against immobile objects)
damage to passengers:
Attacker declares as a Complex action. Resolve initial test as for a ram, but if there are any net hits to the attacker then before damage is taken, the defender has a choice: they can avoid all damage and come to a halt, or they can keep moving but resolve it as a ramming attack with full damage for both sides.
For each pairing of vehicles, start a four-segment clock to represent the distance between them. The clock represents the distance between the vehicles, from very close (empty) to very far (full). For example, if the PCs are being chased by two NPC vehicles, there’d be two clocks. (If there are large numbers of NPCs, combine their clocks as appropriate.)
For special circumstances where a longer range applies - eg. air combat - use a six-segment clock instead. (I don’t expect to do this often, if at all.)
At the end of each turn, roll a vehicle test, limited by each driver’s vehicle’s [Handling] or [Speed] depending on what kind of environment the vehicles are in. Compare each pair of rolls for each clock. The winner of the test can choose to increase or decrease range by one step, as they prefer.
If the clock is empty, the vehicles are almost on top of each other, and either driver can attempt to ram or force a stop. If the clock is full and any driver adds another segment to it, they get away clean, and the chase is over.
As a Complex action during the turn, any driver can attempt a stunt to try and increase or decrease the distance clock. The driver nominates a stunt difficulty, then both drivers roll separately against the stunt’s threshold. If one driver succeeds and the other fails, they can increase or decrease the clock by one tick.
A gently streamlined list of clock segments and ranges for different types of guns:
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | |
|---|---|---|---|---|---|---|---|
| Pistols | Medium | Long | Extreme | - | - | - | - |
| SMGs, shotguns | Short | Medium | Long | Extreme | - | - | - |
| Rifles, long arms | Short | Short | Medium | Medium | Long | Extreme | - |
| Machineguns | Short | Short | Medium | Medium | Medium | Long | Extreme |
| Assault cannon, rocket launcher | Short | Short | Short | Medium | Medium | Long | Extreme |
If a gun is being used manually (either via a pintle mount or manual/AR remote controls of a mobile turret), the standard roll is Agility+Gunnery. The character can choose to roll Agility+appropriate weapon skill instead with a -2 penalty. Smartgun bonuses apply to both the above rolls if appropriate.
If a turret is being controlled via VR (either a jumped-in rigger or anyone else in VR), it’s Logic+Gunnery.
Vehicles (ratings are body / armour):
Barriers (ratings are structure / armour)
These rules are not yet canon for my current campaign.
Taking heavy inspiration from Blades in the Dark:
The limitations:
In theory I could keep doubling here, but I plan to handwave it away at some point. Don’t take the piss and declare that because you have a machine gun you also have 10,000 knives, or I will engineer the situation so you really wish you had a spoon.
Here’s some common items of gear grouped into load levels. Some GM moderation will be necessary to slot other items into this list as they come up.
| Level | Perception modifier | Weapons & ammo | drones | Electronics and other gear |
|---|---|---|---|---|
| Always hidden | micro drone | RFID tag, bug, slap patch, credstick, chips | ||
| “Naked” | -8 | Hold-out pistol. Knife, sap. Revolver speedloader. Throwing knife, shuriken. | Commlink, jammer, lockpicks, goggles | |
| Light | -4 | Light pistol. Monowhip, collapsible baton. Magazine. Microgrenade. | mini drone | medkit (R1-2) |
| Medium | 0 | Heavy pistol, machine pistol (stock folded). Club. Extended mag. Grenade, flashpak. | Cyberdeck, RCC | |
| Heavy | +4 | SMG, sawn-off shotgun (stock folded). Sword. Ammo belt/drum. | small drone | medkit (R3-4) |
| Loaded for bears | +8 | Sport / assault rifles, shotgun, grenade launcher, crossbow. Katana. | ||
| Loaded for dragons | Always spotted | Sniper rifle, machine gun, rocket launcher. Claymore, staff. Bow. | medium drone | medkit (R5+), metahuman body |
Direct Neural Interfaces are the process of extending a user’s neural commands onto a generic system that can then be used to control arbitrary electronic devices. Basically, you think it, and the machine does it. What’s not to like about that?
Note that although many cyberware systems - for example, replacement limbs - are controlled via neural shunts, they do not count as DNI. They have their own bespoke cabling into your nervous system. However, in some circumstances, having DNI can help two systems that would otherwise conflict interact more harmoniously, for example Wired Reflexes and Reaction Enhancers.
In game terms: replace all “wireless bonuses” with “DNI bonuses.” DNI bonuses apply whenever the character has a direct neural interface connection to the item of gear, and hence can control its full funtionality via mental commands. You do not need to maintain any access to the wider Matrix to use them, but you do need either a wired or a wireless connections between the devices and your datajack.
In real world analogy terms, think of DNI as being like USB combined with Bluetooth, with one end plugged directly into your brain. Just about anything you own can hook into it and work with anything else, and your brain can command anything hooked into it.
There are two main ways to handle the interface between your gear and your brain matter:
More than half the population have datajacks fitted, and if you exclude the SINless poor that rises to more than 75%. They are cheap and common.
Several items of common cyberware include a datajack for free:
Your datajack can connect to stuff over a wired connection or a local wireless one. Both offer the user equivalent levels of control over their gear. Wireless, however, has the risk of getting hacked. Wireless devices can be targeted by hostile deckers with a variety of offensive Matrix actions.
In game terms, these are largely interchangeable, and you get any DNI bonuses whether you use wired or wireless connections. However, it can require an extra Simple Action to plug cables in if you want to avoid wireless.
These rules are canon for my current campaign.
Cyberdeck prices are reduced to 25% of RAW.
Contacts can no longer accept any vision mods other than image link. For avoidance of doubt, mages can cast spells through these, as the contacts allow natural light to pass through with AR content overlaid. Obviously, contacts must be wirelessly connected.
Smartlinks are now changed to a piece of headware, so are no longer eligible for addition to contacts/glasses/goggles/etc.
Other than that, glasses and goggles are unchanged. Mages cannot cast spells through glasses or goggles when using enhanced vision modes (eg low-light, themographic, magnification, etc) as these rely on electronic post-processing.
Prices and availabilty in RAW are for permanent fake SINs. These last until they are burned.
There is a cheaper option: burner SINs. These will only last a few days before being discovered by routine scans in the SIN database. These are good choices when a criminal needs a good-quality SIN for a mission but doesn’t need it to last a long time.
In game terms, a burner SIN is subjected to an escalating dice pool of verification checks each day: 1 die on the first day, 2 dice on the second day, 3 dice on the third day, etc until it is discovered. The user will receive no warning it has been discovered until they try to use it.
| Avail | Cost | |
|---|---|---|
| Fake SIN (Rating 1-6) | (Rating × 3)F | (Rating × 2500)¥ |
| Burner SIN (Rating 1-4) | (Rating × 2)F | (Rating × 1000)¥ |
| Any licence for fake/burner SIN | 9F | 500¥ |
Holsters:
Long guns:
Accuracy modifications:
Recoil compensation (RC) mods:
Other mods:
All guns are one of three kinds:
Standard guns, when connected to the user via DNI or cabled directly to goggles or glasses, can use augmented reality to communicate with the user:
Hacking standard guns has limited effect; it can change or disable the AROs but that’s about it.
Smartguns have a full suite of internal sensors and motorised components, including a rangefinder using time-of-flight radar and a tiny gun camera.
With DNI to a smartgun, any user gains the following benefits:
However, to really unlock the full potential, the user has to have DNI and also get the smartlink cyberware. With DNI to a smartgun (wired or wireless), a user with a smartlink gains:
These rules are canon for my current campaign.
Banned. This stuff is terribly OP.
Characters can upgrade cyberware or bioware systems in-place, eg. from Wired Reflexes 1 to 2, by paying the difference between the ratings (in nuyen and Essence.)
Removing augmentations leaves an “Essence hole”. Your Essence doesn’t go back up, but you can now get further augmentations installed without reducing your Essence further until the “hole” is filled.
The following items of cyberware include all the functionality of a datajack, including giving the user DNI and a port for direct wired connections:
All basic cyberware comes with a constantly running wireless Matrix connection. This applies even for ‘ware like cyberlimbs, where all the control the user needs is done via a direct neural shunt, so the wireless connection isn’t needed to use it directly.
This wireless connection is used for downloading firmware updates, running diagnostic routines, and communicating status and error reports back to the user (it’s hard for a cyberarm to tell its user its time for a maintenance routine without this connection. Although some corps have experimented with persistent itching sensations in particular spots, but it has not been popular.)
Where a piece of cyberware has no listed wireless/DNI bonus, a character can disable this wireless connection without penalty. This offers protection against interference from hostile deckers. However, it might attract attention from the authorities if the cyberware is visible but not wirelessly active, as that raises questions.
Corps do not encourage this behaviour in their own security personnel, as they prefer to keep a close eye on their wageslaves - especially the ones with guns, as wireless PANs and friend-or-foe tagging is key in preventing friendly fire incidents when the undertrained and underpaid guards get trigger-happy. Only the most elite troops, above HTR grade, are likely to engage in combat with wireless disabled.
The internal router is the device for streetsams who want to make themselves hacking-resilient without relying on a decker. It replaces the use of ubiquituous wireless connections to link together all your equipment with alternatives wherever possible. Internal cyberware systems are linked via subcutaneous wiring. Induction pads in the users palms are used to communicate with smartguns. Several discreet additional datajacks are included at the wrists, ankles, and base of the spine, for more convenient connection of wired gear.
The internal router also includes processing systems to mediate between otherwise-incompatible cyberware from different manufacturers.
In game terms, the user can benefit from all the usual bonuses for DNI without having to have most devices exposed to wireless hacking via the Matrix. An internal router system includes a datajack for “free”.
Grey/used/basic grade internal routers are extremely obvious to anyone looking at you, as they use visible subcutaneous wiring over large portions of your upper body, including the face and hands. This wiring becomes less visible in alpha and betaware, and is almost undetectable in deltaware. Although internal routers are not illegal, they are commonly used by heavily cybered (ie. dangerous) individuals and so likely to mark the user out for further investigation if openly displayed.
The smartlink is a headware module and software suite that offers an interface between the user’s nervous system and a smartgun. It can only function with DNI to the gun, although this can be wired or wireless.
It offers an advanced co-processor for realtime targeting calculation, 3d modelling of the environment built from the user’s senses, trajectory tracking for each round fired that feed back into the system to make future shots more accurate, and integration from the user’s nervous system into the targeting computation that automatically corrects for movement, hand microtremors, and body posture.
[^1] Reduced from 0.7 in RAW. [^2] No longer eyeware, as in RAW; smartlinks can only be implanted now, and not built into gear or into cybereyes.
Scenario: you and your RPG group want to play Shadowrun. You’ve never played before; maybe you have experience of other RPGs, maybe you don’t. You’re intrigued by the man-meets-magic-and-machine setting but you’ve read some stuff about the game system. It sounds… daunting. Maybe you’ve gotten as far as looking through the rulebook, and thought: eep!
If this is you, I hope to help!
Shadowrun is a pretty tricky beast at first – but I swear it does start to make a degree of sense once you get started. This document presents a grab-bag of tips and suggestions that might help you get past that initial barrier.
Note that this document was written specifically for Shadowrun Fifth Edition (5e), although some of the more generic advice applies to other editions also.
What I’m not going to discuss: to keep this document manageable, I am going to focus only on Shadowrun’s mechanics. I am not going to talk about non-mechanical GMing advice (eg how to write and pace a mission) or suggest houserules to patch over some of Shadowrun’s more annoying problems (these are very much a matter of taste, anyway.) There’s plenty of material already written that covers both of those angles.
There’s a few obvious things that you and your table can agree not to use that’ll make your initial games far easier without leaving any glaring holes in the game:
Oh my god there’s so much stuff.
There is, but there are some things you can do help narrow it down.
You might consider using pregen characters. But pregens suck, and the ones in the rulebook aren’t very good (they have some very weird choices and they aren’t even rules-legal, which is incredible), and dealing with the massive equipment list the pregens have is almost as overwhelming as generating a character. So, maybe skip that, and make your own.
First and foremost: use a tool to help you make characters. Chummer5 is free. Make sure it’s configured to use only the core rulebook.
Secondly, a word about chargen systems. Shadowrun has 3.5 different ways to generate characters (Priority, Sum-to-Ten, Karma, and Life Modules.) Each one has significant downsides. (Yes, I know this beggars belief.)
Priority gen is the one in the core rulebook, with the letters A-E. It’s the default choice. It has two major downsides. Firstly, it makes some characters really difficult to make (famously, troll deckers are almost impossible.) Secondly, it can cause failure feedback loops. You allocate, say, D to resoures. You do all your skills and attributes. You start buying gear… and realise you need a C in resources. Now you need to go back to skills and attributes and re-do them so you can take the C and give it to resources. New players can bounce around this loop at lot and it gets really frustrating.
Sum-to-Ten is a minor variation on priority gen, described in Run Faster. It lets you trade letters eg. you can have AABEE or BBBEE. It fixes the first problem but not the second.
Life Modules (also in Run Faster) is this hippy weirdo thing were you pick different stages of your character’s life and each grants you points in skills or attributes or whatever. Unless you’re really good with it, it makes really, really jack-of-all-trade weird characters who aren’t skilled enough at any single thing. Avoid.
Finally, we come to what the internet tends to call Karmagen (but Run Faster calls “Point Buy”; same thing.) Basically, you start with a pool of karma and 1 in all your attributes, and just buy whatever increases and gear and abilities you need from the pool. The major downside here is that it’s a pain in the arse to do by hand, but Chummer5 frees you from that. The risk is that it can be a bit overwhelming, but I think on balance as long as you’re not doing chargen by hand this is the best option for new players.
Shadowrun is classless, and you can build anything, which is great – but also overwhelming. How do you get started navigating all this stuff?
Even with the splatbooks left aside, the SR 5e core rulebook (CRB) alone is still pretty large. It’s a lot easier to get to grips with if you leave out the less important rules… but the book’s organisation isn’t great, so it doesn’t do a great job of flagging up the rules that you can safely ignore when you’re starting out.
In addition, some of the rules are just plain bad. Either completely confusing, a pain in the arse to use, or both.
Here I’m going to flag up some sections I suggest you ignore.3
I advise you to not even read these.
Characters:
Combat:
Magic:
Matrix:
Vehicles:
Combat:
Magic:
Matrix:
Vehicles:
Other stuff:
Shadowrun has a lot of rules that do not come up very often, and for some reason, not all of them are intuitive. Instead of knowing each specific exception, make sure you know well the basic stuff, like skills, combat mechanics, common infiltration rolls and basic magic and hacking stuff. If a niche case comes up in game, make a quick call that makes sense in the system and move on…. Focus on having fun, cool descriptions and in the characters. – Yomatius6
Your player just said they want to do something, and you know there are rules for this but you can’t remember how they work but you do remember they span several pages and you’ve already paused the session twice in the last hour to look stuff up. This doesn’t feel like a good time to stop play. So now what?
Don’t panic. For all of Shadowrun’s voluminous rules, and 80+ skills, and millions of items of gear, and modifiers, and modifiers that modify the modifiers (!), it almost always boils down to the player:
As GM, you are well within your rights to make this up on the spot. Now, whether or not to do so can be a tricky judgement call, with a few factors to weigh up:
Suppose you want to make a roll up. How do you do that?
Note that there’s a lot of overlap between modifiers and threshold, particularly when ad-libbing a roll like this. This is true on a statistical level as well, as a modifier of +3 is equivalent to changing the required threshold by -1. It’s perfectly OK to skip the modifiers and just change the threshold instead. This is particularly true of tests like Perception, where the result is graduated rather than a flat pass/fail. I rarely modify Perception checks, and instead I vary the information the player received based on the outcome of an unmodified roll.
If there really isn’t a skill to match, you can also ask for an attribute+attribute roll. There’s a few of these defined in core rules, like Judge Intentions (Int+Cha) or Composure (Wil+Cha). You can combine any two you like though.
Character generation is overwhelming enough when you’re only doing one; what if you need six NPCs?!
The very short answer is: don’t. It’s not usually necessary.
A real common GM trick is the “rule of threes”. (This is also similar to the Rule of Twelves, described here in this video by u/Bamce2.) If you need a dice roll for an NPC, pick a level:
In-game, these dice can come from some combination of attribute, skill, and gear - it doesn’t matter which.
When you want to speed play up even further, you can swap out opposed tests against NPCs for a threshold test against their dice pool divided by 3. (Don’t use 4, here, as you usually would for buying hits, unless you want to make your NPCs even more cannon-foddery than they already are.) So a ganger would always roll 3 hits to attack and 3 hits to defend. This can get a bit boring if over-used though.
I suggested above that you set the splatbook content aside at first, but there’s a lot of good stuff in there that you’ll want to introduce as you go along. Some suggestions for the most useful expansions to look at first are below. (These are in no particular order.)
This document was compiled from the many excellent suggestions in these following posts on r/shadowrun. I have only included a small selection of the tips contained in these links, so if you want more, click through!
thanks to u/CelticSurfer for this suggestion ↩︎
Thanks to u/EnigmaticOxygen for these suggestions. ↩︎ ↩︎ ↩︎ ↩︎ ↩︎ ↩︎ ↩︎ ↩︎ ↩︎ ↩︎
Thanks to u/ReditXenon for these suggestions. ↩︎
u/JerekTelorian: https://reddit.com/r/Shadowrun/comments/i6b7l6/_/g0v0a3v/ ↩︎
Thanks to u/LeonAquilla this suggestion. ↩︎
/u/Yomatius: https://reddit.com/r/Shadowrun/comments/i6b7l6/_/g0wlzkw/?context=1 ↩︎
The Shadowrun Matrix rules have undergone years of patching and re-patching, more so than any other aspect of the system. There are many decisions that are made for good game mechanic reasons but have inadequate explanations within the in-game universe. This makes them confusing and counter-intuitive, as the mechanics and the narrative sometimes don’t quite align.
While the rulebooks do a decent job of defining the pieces of the Matrix they don’t go into enough detail about how the pieces fit together inside the game universe. Instead, the books mostly go from piecemeal definitions directly into the rules. Players and GMs are left to infer the workings of the game universe from how the rules function, but this isn’t always clear or consistent.
I wanted to have a go at cleaning this up for my own game. Although unfinished, this document is the result. It attempts to describe the in-universe view of the Matrix and how it works.
Goals of doc:
Non-goals:
NB: Although the below is written predominantly for my own Shadowrun campaign, and mostly uses Shadowrun jargon, I hope it might also be of use for other Cyberpunk RPGs that eschew cassette futurism and instead have wireless networks and augmented reality interfaces.
The Matrix is so far ahead of our current understanding of computing as to border on magical. Nevertheless, there are some ways in which it resembles the networks we are familiar with today.
This is the part of the Matrix that relies on device-to-device connections and is called the local mesh or sometimes the lower grid. The extreme density of devices in a 2080 city, combined with the ability to seamlessly pass traffic from device to device, can get your signal where it needs to go.
The local mesh has a strictly limited range: too many hops, too much distance, or too much interference and the signal degrades to become useless. Fortunately, for a legitimate user, their network traffic only needs to reach an uplink node, so this is rarely an issue.
Any two or more Matrix devices within range of each other will always form a local mesh, even if they cannot route a signal out to the wider Matrix. They will still be able to communicate within themselves as normal.
When you want to communicate with a device that’s outside local mesh range, first you need an uplink node. These are scattered around major metropolitan areas, typically serving an area of a square kilometer or so. Your device sends traffic along the local mesh until it reaches the nearest or most convenient uplink node. Uplinks serve as the onramps to the rest of the Matrix; they bridge your traffic over to the backbone.
Uplink nodes are sometimes called beanstalks by deckers, because they lead to the clouds.1
The backbone, or the upper grid, is the planet-sized interconnected network of fibre cables, satellites, microwave and visible-laser point-to-point communications, and other bleeding-edge-tech ways of getting 1s and 0s from A to B. Once your traffic is on the backbone, distance is no object and bandwidth is functionally infinite.
Security on uplink nodes is fierce, and traffic on the backbone is routinely subjected to deep packet inspection by GOD. Only the most legendary of novahot deckers have ever managed to smuggle illegal traffic over the backbone, let alone compromise an uplink node entirely.
NB: This document removes the “Foundation” as the main operating medium of the Matrix entirely. The “backbone”, as I’m calling it, is its man-made, understandable-tech replacement.
I’m in favour of technomancers; I think the whole concept of “magic”-powered hackers is quintessentially cyberpunk/urban fantasy. But I can’t get past the Foundation being this thing that powers the whole Matrix. It can be mysterious or it can be everyday but it can’t be both at once. And the lore is hopelessly knotted: hosts are “grown” from the Foundation, but we can’t tell you how, and that makes hosts expensive because it’s very dangerous, except every Stuffer Shack has one. I can’t find a path through this.
So I say: get rid of it. Keep the Resonance and Dissonance as mysteries-man-was-not-meant-to-know, like metaplanes and whether or not spirits are summoned or created. But make the core Matrix itself entirely technological.
You can easily keep Foundation hosts, however — restricting them to rare, mysterious, and very powerful hosts only. And they can keep their associated weakness to Foundation dives and the plot possibilities they contain.
The backbone infrastructure is administered and patrolled by GOD, and is theoretically neutral between the megacorps. But the corps didn’t get rich by trusting each other. Where security demands it, it’s not unusual for corporations to run their own private communication lines - for example between a secure, hidden facility and a more public one. This lets the secure facility access the Matrix discreetly without making its location or purpose obvious.
On the local mesh, dark fibre functions like a wormhole. If you can hack the controlling host on one end, you can coerce it to carry your traffic to the other, and suddenly you can “see” devices that could be hundreds of kilometers away. Occasionally, wily shadowrunners use this as part of a smash-and-grab, using a forgotten dark fibre link to hack into a distant host that is too physically well-protected to get near in the physical world.
Hosts are the servers of the Matrix; they’re the guardians of data, the places you go to get stuff done, and the engines that keep the wheels turning. They come in a few types:
Local hosts - quite common, these are small, physical servers that are (literally, physically) local to whatever they control. Low to medium rated security systems, building control, stock-keeping, industrial control systems in factories, etc etc. They are only connected to (and can only be reached via) the local mesh, and hence are only usable at relatively short ranges.
When viewing the Matrix in VR, local hosts appear down at ground level, at a distinct physical location (unless they are hidden.) Well-funded deckers and other criminals might acquire low-end local hosts for nefarious purposes.
Cloud hosts - the grown up version of local hosts, used to run services that have to be accessible by people all over the planet. Distributed across lots and lots of physical servers, roughly analogous to a modern day planet-scale website, and directly connected to (and usually only reachable from) the backbone. As such, you can almost always get a good connection to a cloud host, unless your local mesh is being disrupted or you are far from civilisation.
When viewing the Matrix in VR, cloud hosts float up in the sky.
Cloud hosts are enormously expensive to run, both for the hardware required and for the licencing and necessary security to connect to the backbone.
Offline hosts - local hosts with no connection to a local mesh. Can be used for cold storage of very valuable files, or wires-only ultramax security systems, or old systems still running in abandoned and forgotten buildings, or things deckers have cobbled together. Typically low rating, as the amount of processing power and hardware becomes very serious for higher ratings; but could in theory be anything. Offline hosts might be connected to online ones via dark fibre (see below.)
Not every host advertises its existence. So-called dark hosts are ones that are running silent on the Matrix. Local dark hosts can be detected by getting close to them and looking for hidden Matrix icons in the usual way. Cloud dark hosts are trickier, however, and can normally only be visited if you have the secret co-ordinates to find it.
Commlinks are the most visible part of the Matrix - the device most commonly associated with it in people’s minds. They are analogous to modern-day smartphones, and often take the form of a pocket-sized slab covered in a touchscreen (although they can be much smaller if the user forgoes the screen. They can even be wholly implanted, in case you wanted to become an even bigger hacking target than you already are.)
Most people using a commlink do so via a direct neural interface and augmented reality.
Civilians typically get DNI in one of two different ways: either via a datajack, or trodes. Both offer a wireless connection to the commlink, with a wired option as a backup. Trodes are a terrible experience though, with a noticeably poorer AR quality, and a connection that often glitches out unless the user stays quite still (as the trode net can shift around on the head). You can glue it down, but now you have glue in your hair and it’s gonna sting when you take it off. On top of that, they require significantly more concentration to generate DNI signals to interact with the device - they’re just not as sensitive at reading your brainwaves - which gives most people a headache after a few hours. This is why datajacks are heavily preferred and, consequently, extremely common - despite their invasive nature.
(People with more extensive cyberware can get direct neural interfaces through other options - for example, a rigger’s vehicle control rig cyberware includes all the same functionality as a datajack as part of the package. And some people have commlinks or cyberdecks enitrely implanted, which also give them DNI on demand, without any further hardware.)1
Users who won’t or can’t get DNI can still get a crude form of AR via various pieces of hardware: headphones for audio, plus contacts/glasses/goggles for visual AROs. They can even just about use user interface AROs, although the tactility component is vastly inferior, even if they wear special feedback gloves. It’s a crappy, godawful experience though, and only a Luddite would do this if they had any choice.
Finally, if all else fails, you can always fall back to actually touching the screen on the commlink itself. This still has some usefulness, although in the age of AR it is not most people’s preferred experience. There’s a few reasons people still buy commlinks with screens, though:
Commlinks are the only type of general-purpose computer most people own. With fairly serious onboard compute power, plus the ability to borrow more via fog computing, they can do everything most people need. And through augmented reality, they can expand or contract their interface to fit in the palm of your hand or fill your vision and walls.
Commlinks may be - for most people - the most visible and obvious type of Matrix device, but tags are by far the most common.
“Tag” is a catch-all term for any small, single-purpose device that connects directly to the Matrix. They are often associated with and attached to a single object in the real world, giving that object a presence on the Matrix and a tiny degree of computing smarts.
The most basic kind of tag is a combination of informational and locational, and these are built into almost all durable consumer goods, from socks to jewelry to coffee mugs.
Tags have a dark side: for an unmodified tag, there is no guarantee that the data it is logging is staying private. A law-abiding wageslave is typically being tracked by dozens of tags on their body at all times, all of which are uploading location data and contact tracing data to an endless array of overlapping ad tracking networks. The only kind of privacy they can hope to enjoy is through obscurity; by not being interesting enough to ever be noticed in the sea of data, and by relying on the fact that the data is gathered by competing corps so no-one ever puts the full picture together.
Cyberdecks are some of the most complex consumer electronics ever made by mankind. They use dozens of different types of parallel processors, incorporate huge libraries of known vulnerabilities and malware attacks, hundreds of expert systems so advanced as to be bordering on semi-sapient AI, and have nitrogen-cooled quantum computing cores that can break some of the toughest encryption known to metahuman kind in minutes. They have about the same resemblance to commlinks as a variable-geometry VTOL fighter jet does to the Wright Brother’s first plywood-and-canvas airframe.
In other words, they’re kind of a big deal.
Although the Matrix started as a VR-only technology, once ubiquitous AR came along it rapidly fell out of favour. Most people just don’t feel comfortable completely disconnected from their surroundings, particularly if they’re in any sort of public space. Plus, while you can move really fast in VR - with the Matrix flowing as fast as your thoughts - it turns out that’s exhausting if you do it for more than a few hours. VR is now sufficiently uncommon that for most commlinks a SimSense module is an add-on and not a standard feature.
So for most ordinary folk, work time and leisure time that involves computers is mostly done through AR, not VR. They dip into VR now and again – mostly either for virtual meetings in work with people in different offices or when safe at home – but that’s all. Extensive time in VR is the domain of serious gamers, the most dedicated sports fans watching live broadcasts, and deckers/spiders/other socially isolated buttonheads.
This is motivated partly by aesthetics - I still want Shadorun to contain offices where people go to work, and I want them to look broadly like you expect offices to. If everyone is in VR all the time, there’s no need for huge spaces crammed with tiny desks and beige walls and miserable people. And that aesthetic, to my mind, is an important part of any pan-corporate dystopia.
I also think it helps make deckers feel distinct from everyday Matrix users. In early SR, VR wasn’t ubiquitous (requiring expensive cyberterminals to use), and was mostly only used routinely by hardcore hackers. I want this to still be true.
Consider the basic, unsculpted Matrix in full VR: how it looks if you disable all visual re-skins normally added by your service provider, your commlink manufacturer, your settings, and so on. Like you’re some sort of 2052-era cave-dwelling metahuman back in the primordial grid. What do you see?
Imagine an infinite plane of black, overlaid with a fine silver grid, stretching to the horizon. This is the lower grid. It’s populated with icons for all the devices within local mesh range of your commlink - maybe a few hundred meters, depending on network conditions. Personas are represented by a special icon that is configured according to the user’s wishes. Devices in PANs are hidden, by default, to make the display less cluttered; although you can turn that off if you want to see everything. Devices outside of PANs are represented by icons, typically utilitarian factory-default ones like cartoonishly coloured caricatures of what they are, tiny corporate logos of whoever made it, or eerily photorealistic modelled and rendered versions of whatever the icon represents.
In theory, the lower grid spans the planet - you can zoom your viewpoint up into the “sky” and see a map of the world, with data-sparse areas like the deep sea represented by areas where the silver grid fades out to blank nothingness. But you can’t see icons outside your local mesh, so it’s not that interesting to do so. Most of it would look empty from the perspective of your commlink.
This limited view of the local mesh can be very intense, though, with many hundreds or low thousands of icons - and even more fine filigree lines pulsing between them, representing the data flow from device to device. Even the most hardcore decker can’t do anything with that much information. Normal people run extensive filtering options that remove the clutter and only show the stuff they care about: typically, one icon for each device they are carrying, plus one icon for each PAN they can see.
There may also be local hosts visible in the lower grid. For example, a wageslave arriving at the office would see icons for one or more local hosts associated with the workplace - perhaps the main shared host for files and work, and a few more for security and building control. These are hosts that don’t have a dedicated connection to the backbone and work mostly through the local mesh. They would log on to the shared host at the beginning of their workday, and it wouldn grant them access to the stuff they need to do their job.
Stretching above them is the sky, by default rendered as a very dark blue-grey. Floating within it are icons for all the publicly visible hosts on the Matrix - many hundreds of thousands of them. Again, this is hopelessly cluttered, so people filter their view. You might see the main P2.1 public host, for example, where you can go to read or post social media updates. Your employer’s public host, where you can read PR updates like a good little wageslave. Your commlink fades all the other hosts in the world out, reducing their icons to barely more than a point, and fading all the colour out. The end result is to see perhaps a few dozen icons floating up there, the hosts you care about and use regularly, plus a sprawling constellation of stars representing the rest of the Matrix.
Finally, some cloud hosts like to be associated with particular geographic points. For example, Dante’s Inferno - the famous/infamous Seattle nightspot - has a host that links to the precise location of the club in the real world. Its host icon floats in the sky, as dictated by the rules; it’s a cloud host, not a local host, so it’s in the upper grid. But a thin line of neon pink and blue stretches down from the host to the precise location in the lower grid that corresponds to the club’s address. For hosts like Dante’s Inferno’s one, this is a key part of their branding, and it means when you are close to the club in real life you get a prominent link to the cloud host on the Matrix.
Neon-coloured wireframes and faceless chrome figures may have been cool last century, but in 2080, people demand a more a la mode view. Sculpting is the process of making things look different. It’s a combination of artwork, animation, and physics modelling; it’s very skilled work; and it’s a lucrative market for those who are good at it.
At the big end of the scale, hosts in VR are sculpted to look like… well, anything the owner desires, right down to changing the laws of physics inside the host. Want it to look like infinitely high sky scrapers with the users navigating sections of the host by jumping between them in zero gee? Sure, you can do that. You probably shouldn’t, unless you want to clean a lot of puke off the floors, but you can.
At the small end, people spend incredible amounts of time and nuyen sculpting their persona’s icon. Cosmetic options and add-ons and accessories can be bought from just about any corp on planet Earth, perfect to show your devotion to this or that brand. People often broadcast their persona icon in an ARO, so there’s a lot of pressure to get the look just right.
VR is yesterday’s tech. It’s where you go to use the computer, but who wants to go somewhere to use a computer? You want the computer to come to where you are. You want the computer to bleed into your everyday reality. Chummer: you want your reality augmented.
Welcome to AR.
Everything on the Matrix is represented by an icon. Each device – your commlink, your car, your toaster - has a corresponding icon, and each icon has a corresponding device. Mostly, these icons are set by the manufacturer and look like the device in question, although the art style can vary from photo-realistic to cartoonish to stylised. People can change them, but generally don’t for boring stuff like their toaster. Personas, however, have special icons that the owners can change to look however they want, within some limits. People spend many hours and many nuyen playing virtual dress-up with the personas.
So: suppose Wally Wageslave is using his commlink to view the Matrix. Spotting is the process by which his commlink discovers there’s an icon to show him. Spotting is tied to the local mesh, the part of the Matrix that runs on device-to-device connections. You can consider spotting range as a sort of short-range horizon, it’s the distance around you that you device is actively keeping track of so it can keep your connection going.
Wally’s commlink doesn’t concern itself too much with devices that aren’t really nearby, as it’s really only trying to keep its connection alive. By default, the spotting horizon extends to about a hundred metres or so (the exact amount can vary with network conditions.) If he wants - although he probably doesn’t - Wally can tell his commlink to look further than that, and show him all the devices it can find at a larger range, up to the limits of the local mesh.
There are some circumstances in which Wally might not see an icon for a nearby Matrix device.
The Matrix, or at least the local grid part of it, is a decentralised peer-to-peer mesh network. Previous Matrix crashes have taught the corps the value of robustness and the dangers of single points of failure, so there is no reliance on a controlling host to make the wheels turn. Toss a handful of Matrix 2.0 devices inside a Faraday cage and they’ll form a network automatically, without needing anything external to direct them.
Down at the device level, this is quite a complicated process. Each device has to be aware of the position and movements of all the other devices nearby, so it can make smart decisions about where to send its traffic. If Wally wants to send a message to his colleague Wanda, but she’s too far away to send it to directly, it doesn’t make any sense to send it via a nearby commlink belonging to someone in a car that’s about to move out of range. Better to pick a different intermediate that’s somewhere inbetween Wally and Wanda and isn’t moving.
The mesh network itself resolves this problem without any user intervention. In a fiercely complicated bit of co-ordination, each device uses signal strength measurements and triangulation to estimate the positions of every other device within spotting range. So for every device within spotting range, Wally’s commlink has an approximate location - usually plus or minus a few meters, maybe quite a bit more than that if the network is very quiet (not enough devices around to do triangulation) or very noisy (too much to keep track of.)
Devices do not usually broadcast their precise location publicly. Even the most naive Sixth World resident knows it is not a good idea to constantly tell every potential mugger within a few blocks exactly where you are. So the mesh network’s approximate position is all Wally’s commlink has to go on when trying to line up the icons it sees on the Matrix with the matching devices in the real world.
Positioning is the process by which Wally’s commlink decides where to put a device’s icon when Wally looks around in AR or VR.
In many ways the problem is easier in VR, because the commlink doesn’t need to line anything up with the real world. It can place icons for devices in places corresponding to its best guess, and if there’s a dense collection of overlapping icons in one place it can artificially spread them out so Wally can see them all individually. After all, if he’s in VR, Wally probably isn’t overly concerned with exactly where these devices are, he just wants to be able to see them all and interact with them all as easily as possible.
In AR, commlinks struggle. By default, they rarely show more than a fraction of nearby device icons anyway, lest they become distracting to the point of uselessness. But if Wally tells it to do so, it’ll dutifully have its best guess and place icons around him at some location that might or might not align with reality. This can make some funny things happen, like if Wally is talking to one other person somewhere and that person’s icon is shown as being ten metres off to one side.
This has consequences for, eg., beat cops on patrol. They might pass a crowd of 20 people, where one of the crowd is a SINless criminal scum. But unless they are very sharp-eyed and quick-witted, they are unlikely to notice that the crowd of 20 people only has 19 device icons floating around them. And even if they do, they can’t tell who is the odd one out.
Public augmented reality displays wouldn’t make a lot of sense if different people saw them in different places, so the Matrix protocols also have the ability for any ARO or icon to anchor its precise location and orientation. This anchoring be part of the public broadcast – in which case everyone will see the ARO at the exact same point. Examples include ARO adverts, signage, restaurant menus, art installations, and so forth. Or, it can be private – Wally can share his commlink’s location with his family so they can find him at the mall. Everyone else at the mall can see his commlink icon but not the location information.
Commlink icons have a special sidechannel that usually broadcast the owner’s SIN at all times. This isn’t quite mandatory, but will certainly prompt investigation from the cops if it’s turned off in most parts of town.
Nameplates are a sort of beefed-up public version of this. They are an ARO display that people can enable on their commlinks that shows their name, gender pronouns, P2.1 profile link, and other biographic information. People turn these on in situations where they’ll be useful, eg when they meeting new people. Some people spend quite a lot of time customising their nameplate AROs to reflect their personalty. These are also the kind of people that will have an obnoxiously over-the-top persona icon.
The etiquette around when it is and isn’t polite to show a nameplate is complicated and – frankly – still being worked out by society at large. Most people don’t walk around in public with one on, although some extroverts might. Most people would turn them on for a business meeting, to facilitate introductions. But turning it on at a private dinner party with people who know you can be considered rude because it implies you think other people there might have forgotten who you are.
In a society defined by the haves and the have-nots, the sharpest line between them is the possession of a System Identification Number. A combination of citizenship, a passport, voting rights, and taxation obligations, it guarantees you at least some protection under the law and the chance to work gruelling hundred-hour weeks until you die. What an honour.
SINs are issued by a wide variety of governmental and extra-territorial corporate entities. They can be granted by birth or by a similar process to obtaining citizenship. Sometimes, corps grant them to particularly desirable hires. Often, corps use the threat of revoking someone’s SIN to keep their workers in line.
Physically, a SIN is merely a string of alphanumeric characters. The only human-readable part of it is a prefix code indicating the issuing entity - country or corp - who owns and controls the SIN. What counts isn’t so much the SIN itself as the data associated with it in various online hosts and datafiles.
SINs have become the de facto unique identifier in the Sixth World. They are tracked everywhere, both in person and in the Matrix. Every interaction and transaction you have can be tied to your SIN and tracked in some database - and almost all of them will be. Hence every SIN has, trailing behind it, vast wakes of data, scattered across innumerable databases.
Those who don’t have a SIN - the SINless - are condemned to a life of misery. They are locked out of legal employment, of all banking, of reasonable healthcare. They cannot vote and they have no social safety net; even their basic civil rights are reduced almost to nothing. They face a lifetime of grinding for low cash-only wages and paying shady landlords high rent for shitty apartments, and praying that when they get sick there’s room at the charity hospital for them.
This naturally creates a market for fake SINs, anything that might give the hopeless some hope. And, in turn, that creates a market for checking SINs are real.
The Matrix protocols have baked-in support for all personas to broadcast a SIN in a special sidechannel. This enables pervasive tracking; every interaction you have on the Matrix and in real life can be cross-referenced against your SIN. Everywhere you go, everything you do, there is a data trail left in your wake, extending out behind you. And that trail is scanned and recorded by thousands of corps.
In most parts of the world, SIN broadcasts are not quite a legal requirement, but they are certainly strongly enforced. Not broadcasting any SIN in a lower-middle-class-or-better part of town will attract unwelcome attention from the authorities. In high-class areas, you can also expect that SIN to be routinely getting checked for validity against the GSINR (see below). Some public areas will actively alert authorities if you enter without a SIN broadcast, and most legal businesses, from shops to public transport, will refuse to do business with you.
The converse is also true; broadcasting a SIN out in the Barrens can mark you out as a rube and a target.
If the SIN is just a short string, and everyone is broadcasting theirs to the world at all times, why not just take someone else’s? Why bother with complicated fake SINs at all?
The first answer is that legal devices can’t do this at all. They don’t let you set your SIN yourself, nor do they store it anywhere. Instead, when you boot your persona, they query a host belonging to your SIN issuer, which does a DNI-auth check of your brainwave patterns before giving your device the SIN it should broadcast.
Even if you hack your device to broadcast an arbitrary SIN, though, this still doesn’t work. The same trackers and profiles that are listening for your SIN will almost immediately notice (a) if two different personas are broadcasting the same SIN at the same time and (b) if a SIN has moved from one persona to another. Either condition will result in them broadcasting an alert that will lock the persona completely out of the Matrix until they reboot their device and sign back in to their account.
This can be used as an attack vector, called “SIN-bombing”: deliberately copying someone else’s SIN just to get them temporarily booted offline. It’s typically little more than a minor inconvenience, though, so of little practical value.
If you are a corpsec architect, SIN broadcasts appear to be a very useful tool. It is supremly difficult to spoof or steal either personas or SINs, which means in theory they can provide very strong guarantees that someone trying to get through a security gate is who they say they are. Particularly when the corp in question is also the issuer of the SIN, as is typically the case for its employees, which means they have unfettered access to the SIN biographic and biometric data.
Unfortunately for the corps, it doesn’t work that way in practice. Several high-profile data thefts took place in the early 2070s where Shadowrunner teams used a SIN-bombing attack combined with a powerful local jammer to clog up Matrix traffic. The duplicate SIN was noticed and shut down a few seconds later, delayed by the jammers… but during that narrow window, the attackers were able to open doors, shut down security systems, and disable countermeasures. The third or fourth time this happened to any given corp, they quickly switched gears, and pulled SIN scanners out of critical security systems. Today, the state-of-the-art in local security systems consists of biometric scanners coupled with a database of allowed users held locally on a well-secured host.
It is crucial that the haves protect their stuff from the have-nots. Hence, it is important to be able to verify a given SIN is real and not an imposter. Fortunately for plucky criminals trying to live outside the law, a combination of inter-corp paranoia and mistrust makes checking if a SIN is fake a much more difficult problem than it could be1.
There are, broadly, three methods used to verify that someone presenting a SIN is doing so honestly.
The global SIN registry (GSINR) is a fairly simple database of every SIN, world-wide. Each SIN in the database is stored with several additional pieces of data:
It takes less than a second to look up a given SIN on the registry. The registry is administered by the Corporate Court and access to it is provided fairly cheaply to any interested corp or nation state, although there are additional fees for more detailed information.
For a check against the SIN registry, the querier provides a SIN and, optionally, some biometric data eg. a fingerprint. There are several possible outcomes of a check against the GSINR:
Returning the biographic data or confirming the biometric data (ie (3) and (4) above) incur extra fees for the querier, which quickly add up if scanning SINs routinely, so they tend to be reserved for more detailed checks.
The global registry does not permit “reverse searching” ie. you cannot take a fingerprint and ask the database what the corresponding SIN is, nor can you simply download all the biometric data and scan it yourself. The only type of query is “here is a SIN and some biometrics” with the response of “this does / does not match.” Every few years some do-gooder tries to get this changed on the grounds it would help fight crime; the megas that control the Corporate Court always shoot it down. They know that it would make their own staff too easily identified by and spied upon by their competitors.
Unfortunately, the global SIN registry is only as trustworthy as the least secure entity that can access it 2, and (by definition) data can be added to it by every entity that can issue SINs. It’s a relatively trivial process for the purveyors of fake identities to get enough of a hack against some smaller nation-state to insert fake SINs into the global registry. With a bit more effort, they can even get the biometrics to match whoever the user of the fake SIN will be. So, searches against the global SIN registry are a pretty low-grade check, and easy to fool. Still, it provides enough of a verification to keep out the real low-lifes, and is quick and cheap.
In game terms, a check against the global SIN registry is a rating 1-2 check. All purchased fake SINs have at least an entry on the global registry, and all except the very worst of them also have correct biometrics.
If you are the entity that issued the SIN, you have a lot more information about it at your fingertips to perform verifications with. And you can work in the knowledge that your SIN database is held much more securely than the global registry, and so much less likely to be polluted with fakes planted by hackers.
For a start, if a given SIN that claims you issued it is in the global registry but not in your own databases (quite common for low-grade fake SINs), then you’ve definitely caught a faker. You can flag the fake to the registry and deal with whoever is using it as you wish. Probably painfully.
Fortunately for the kinds of high-end criminals who rely on fake SINs to move through society, if you aren’t the SIN issuer of a SIN you want to check, you simply can’t do any of this. The SIN issuers are either secretive megacorps who compete with each other, or paranoid nation-states that are barely on speaking terms. They don’t share their SIN details except under the most exceptional circumstances. So criminals only face these kinds of near-impossible-to-fool checks if they’re foolish enough to roll up on (say) an Ares facility toting false Ares SINs. 3
Note that SIN issuers can also “reverse search” their own databases, ie take a DNA sample or fingerprint and scan for SINs that match it. The capability to do so is carefully controlled, however, and only accessible to people in positions of authority.
In game terms, a check against the issuer’s SIN registry is a rating 6+ check. These checks can take time, particularly if the biometric data being checked requires elaborate procedures (eg. DNA samples.) They might also incur a cost, depending on how byzantine the corp is organised. It is not uncommon for BigCorp Identity Services to only make the SIN database available to BigCorp R&D Subsidiary on a for-profit basis. 4
If you want more security than a global registry check but you need to check SINs you don’t own, then your only option is a verification check with a data profile broker.
Data profiling exists in the Sixth World as it does today. Companies that resemble a high speed collision between Experian and Facebook ingest the data trails people leave behind them - all conveniently tagged and cross-referenced with their SINs - and use pseudo-AIs to build predictive models of each person’s interests, desires, and behaviour.
These profilers’ primary market is advertising, but they long ago realised that a side effect of their work is spotting fake SINs. Their data analysis is so thorough that any inconsistencies in the data trail attached to a fake SIN stand out like a glowing beacon. A complex marketplace of realtime SIN checks quickly emerged.
Someone wishing to verify a SIN is real can send it to one or more of these brokers. They will look at the data trail associated with the SIN and scan it for gaps and conflicts. If they find any red flags, they will report back to the querier that the SIN looks suspicious, and they can take whatever further actions are appropriate.
In game terms, a check against profile brokers is a rating 3-6 check, depending on the number and quality of brokers involved. These checks become quite expensive to carry out for the querier, particularly at the higher end, so they are not done routinely. These types of test also have a false positive rate; they sometimes flag real SINs as fake, which can irritate VIPs being inconvenienced and get lowly security guards fired.
Fake SINs consist of several parts, of escalating levels of quality:
Lower rating fake SINs are created through a combination of outright hacks against smaller corps or nation-states that have access to the GSINR, coupled with bribery of corrupt insiders, but have no matching entries in the issuing entity’s private SIN database.
This section was written based on, in part, the discussion in this thread.
Shadowrun is a hyper-capitalist corporate dystopia, not a panopticon surveillance dystopia. ↩︎
This is a change from RAW, where the global SIN registry is very secure. ↩︎
I don’t intend to track/enforce this in practice, unless I want to build a specific plot point around it. I will assume all my PCs’ false SINs come from smaller/obscure corps or nation-states. ↩︎
If you think this sounds unlikely, I have alarming stories about real-world corporations to tell you. ↩︎
One reason commlinks are quite powerful is to protect you against hacking. They dedicate a fair bit of their time to monitoring threats around you, scanning for incoming attacks, and so on. That’s definitely important! But what about the rest of your stuff? Every other Matrix-linked thing you own, from your toaster to your gun to your smartglasses, is vulnerable too - and they don’t have enough CPU to protect themselves. They can borrow some processing on demand, via fog computing, to put up some (feeble) defence. But that won’t protect you from serious hackers.
What you need is a personal area network. A PAN connects and merges all your devices into a private little cloud on the local mesh. Your commlink takes charge, and all traffic to and from the mesh goes through it, instead of directly between the device and the mesh. That means it can watch over all traffic, scanning it for attacks, and intervening to defend your devices. Imagine Matrix traffic as acid rain, your commlink as an umbrella, and your devices sheltering safely beneath it.
PANs can be extended and merged, with the most powerful device becoming the one that protects the whole network. When William Wageslave travels to work, he has a PAN, centered on his commlink, protecting his devices. That provides moderate protection against hackers, but not enough for his corp employers to feel good about. So when he arrives at work, the first thing he does is tell his commlink to join the office’s local host. Once the host verifies his persona through DNI-auth it merges his PAN with the office’s Wide Area Network (WAN) and now all his stuff is even more protected, because all his traffic is going through the company host. At the same time, it grants his persona various permissions to access the company resources William will be using to do his job. These will be revoked automatically when he leaves at the end of the day and disconnects from the WAN.
Note that you can only form PANs or WANs on the local grid. You can’t create a WAN based on a cloud host because the latency is too great.
Megacorps are far too paranoid to allow their employees to connect to their servers full of secrets with an unprotected commlink. It would be much too easy for criminals to hack the commlink and use it to get in. So most wageslaves, when working, have to have their commlink connected to a WAN that simultaneously controls their access to work networks and protects them against hacking. This means “working from home” is not a thing that happens in the Sixth World. The user has to be using a device that is part of the company WAN, and that means they have to be within local mesh range of the company host in their office.
Perhaps the corps could solve this, if they cared to. But they’re micromanaging controlling assholes who like being able to watch their wageslaves, so they’re not trying very hard. Very important execs might have corporate local hosts installed in their houses so they can work remotely. Everyone else has to suffer a grinding commute and the watchful eye of their bosses.
What about poor William’s car, out in the parking lot? Or his toaster at home? He’s too far away from them to shelter them in his commlink’s PAN. But a passing hacker could really spoil his day by destroying these devices as they sit naked on the Matrix.
To solve this, at home, people typically use network defenders1: sort of like cut-down mini-commlinks (or, if you prefer, really really tiny local hosts) whose only job is to maintain a basic protection zone around their stuff. They’re usually a step or two less powerful than a commlink, so they’re far from bulletproof, but they’re better than nothing and will at least keep war-driving script kiddies from destroying your house while you’re at work by reprogramming your soy dispenser to “unending firehose” mode. Hopefully.
Vehicles get a special firewall package as part of their GridLink subscription. Whenever the vehicle leaves the user’s PAN, it connects itself to a cloud host that defends it against hack attacks. The effectiveness of this defence varies with the user’s GridLink subscription tier.
Per RAW, an unattended device typically rolls either 2 or 4 dice to resist hack attacks, which is almost the same as being entirely unprotected. The world can’t function like this, it would be full-on chaos. I’ve introduced network defenders as a slightly easier option to rewriting the entire Device Ratings table to give undefended devices more defence out of the box, although that is a viable alternative choice. ↩︎
When you boot up your commlink, the first thing you do is sign into it, via some combination of biometrics. This creates your persona, your digital mirror-image in the Matrix. The persona runs for as long as your commlink does.
Only certain devices can form your persona, and thus let you use the Matrix. These include commlinks, cyberdecks, and RCCs. These may be external devices or implanted ones.
Like any newborn, your persona comes into the world naked and powerless. So the next thing that happens is your commlink reaches out through the local mesh and up to various cloud hosts that live on the Matrix backbone.
Each of these hosts in turn establishes that the person using your persona matches their fingerprint. For users with direct neural interfaces, this is carried out as a brainwave challenge/response in a process called DNI-auth. The host reaches down through your interface and… pokes… your brain a little, inducing certain patterns. It measures how your brain responds to the poking, and compares it to patterns stored in very secure cloud hosts that were recorded as part of a cryptokey exchange when you created the account. If they match, the host is satisfied you are who you claim to be.
Think of it as being like tossing a rock into a lake, and carefully examining the patterns in the ripples.
The corps are very insistent that this process is completely safe. Any resemblance between the transient brainwave states triggered and those recorded in epileptics is purely coincidental. Apparently.
This process is extremely difficult to fool, particularly for lots of hosts at once; although there are urban legends of particularly wily deckers pulling off successful man-in-the-middle attacks against people using trodes rather than datajacks.
Unfortunately, users without DNI-auth suffer much lower security. They have to rely on crude biometrics such as fingerprints and retina scans, all of which are much more vulnerable to fakery, even if they use very expensive and high-end scanners.
Once a given host is happy the persona is under your control, it issues your persona with access permissions over whatever it is in charge of. (Deckers call these Access Control Lists, or ACLs - pronounced “ackles”.) One host might belong to Ford, and grant your persona access to drive your Americar. A Horizon host would give you access to your P2.1 social media account. An Ares host, after particularly thorough examination, would enable you to fire your Predator. And so on and so forth - even a low-key user will have hundreds of these permissions.
This all happens in a few seconds.
Personas are ephemeral things. They only last as long as the commlink is running and you are attached to it. (This is particularly irritating for trode users; if the trodes get jostled too much, they can disconnect entirely, and you have to sign in all over again.) Furthermore, to guard against shenanigans, the more secure hosts will re-run DNI-auth spot checks periodically.
Note also you can never have two personas. The cloud hosts will immediately detect if you attempt to sign in with a second device while the first is still running, and – depending on its paranoia level – either insist one persona is shut down first or completely lock the account down until you contact customer services to get it unlocked. This also works to prevent anyone stealing your persona.
Only being able to unlock and start your car via a cloud host is fine for a boxed-in ground-down wageslave driving to another 14 hour shift, but it’s not going to work so well for a Knight Errant HTR squad heading into a Barrens deadzone or a long-distance trucking convoy delivering supplies through wildlands. People like these need a fallback for when the signal fails.
Matrix protocols include the ability to offload cryptographic keys directly to your commlink for just such an emergency. For most people, this is nothing but an accident waiting to happen - anyone who hacks their commlink can now steal their stuff with impunity. But if you need to be able to work outside of reliable wireless Matrix access, it’s just what you need. Remember to buy a good commlink and all the security upgrades… and remember to back those keys up to a second device too, just in case.
Organised criminals like shadowrunners make use of these protocols so they leave less of a datatrail behind them in the Matrix, and so they can still start their cars regardless of which fake SIN they happen to be using right now. Yes, this means a wageslave’s car is a lot harder to steal than a shadowrunner’s, at least based on just the cryptographic security… ain’t irony grand? (Of course, many shadowrunners compensate for this with interesting booby traps, so don’t consider this a declaration of open season on their stuff.)
Most people are broadcasting a few AROs from their commlink at all times. A basic informational ARO contains their SIN and some basic biographic information: their name, gender representation and pronouns, age, and so on. Anything you’d find on a driving licence. Some people might redact all or part of this, for whatever reason; but not broadcasting at least a SIN will attract attention from the authorities in the better parts of town.
Some people also broadcast their persona’s icon at all times, typically scaled to a few inches high and floating over their head or sitting on their shoulder. Customising and sculpting the persona’s icon is a big business, with every kind of lifestyle brand imaginable making virtual accessories for you to play dress-up with on your digital twin, and that’s before you get to the expert artists and modellers who make all sorts of more outre icons than the basic metahuman figures your commlink came with.
There is no Matrix equivalent of Bing or Google Search. Like the political map, the informational one has Balkanised: split up, divided, and almost hopelessly fragmented. To search the Matrix, then, is not to enter some text into a box and get your ranked results in milliseconds. No, it’s a good deal more complicated than that. It often takes between several minutes and double-digit hours. What’s going on during that time?
The Matrix is divided into hosts. In some ways, a host is a little like a modern-day website; you can visit it, and then interact with the content it presents to you. You can go to a screamsheet’s host, for example, and read the current headlines, and search back issues. But unlike a modern-day website, you can’t deep link into a specific file in a host; you can’t build indices that span lots of hosts, and a file on one host can’t directly reference a different file on another host. The divisions between hosts are rigid. Hence: no Google Search.
So the simplest and crudest Matrix search, then, consists of going to a specific, trusted host and searching just that host’s contents using whatever search engine it might present to you. For example, you might go to the public library, and use it to search through reference books. Or to a particular news org’s host and search their historical archives.
Of course, this only gets you one take on the information - and in the Sixth World, most media is dangerously biased. So this isn’t a very good technique. Instead, xxx
The next stage of a Matrix search is sifting the results.
“We must be as stealthy as rats in the wainscoting of their society. It was easier in the old days, of course, and society had more rats when the rules were looser, just as old wooden buildings have more rats than concrete buildings. But there are rats in the building now as well. Now that society is all ferrocrete and stainless steel there are fewer gaps in the joints. It takes a very smart rat indeed to find these openings. Only a stainless steel rat can be at home in this environment…” — Harry Harrison
All the pervasive Matrix stuff makes the world seem intractable for professional criminals. Surely the second you come out of the Barrens, you’d be revealed six ways to Sunday, right? Fortunately it’s not that bad. Smart bad guys - by which I mean “anyone who’s not a gutter-punk scum” - have some tricks up their sleeves.
Alice is a shadowrunner, walking through a high-end commercial part of town, surrounded by throngs of wageslaves looking to buy lunch or scurrying to meetings. She passes Bob, a Knight Errant beat cop. Alice is up to no good, and therefore carrying a wide range of interesting and potentially illegal items, many of which have Matrix functionality. How does she slip past Bob undetected?
What’s the most fail-safe way to hide? By not having anything to hide in the first place.
If Alice is only lightly armed and has a good fake SIN, she could simply have a legal licence for all her armaments. Her commlink, in addition to her usual SIN and persona icon, will broadcast that she is armed and that she has appropriate licenses. This will probably attract a little attention from Bob; enough to warrant a SIN check, say. But licences to carry firearms are not uncommon so if she’s not doing anything else suspicious and her SIN stands up to scrutiny, Bob will let her pass.
What constitutes a gun that Bob will ignore and a gun that will attract his attention is very situational, however. Perhaps Alice is carrying more serious firepower than a light pistol: say, a hunting rifle, concealed under a long coat. She might have a licence for it, and it might be perfectly reasonable to be carrying out in the wilds of Snohomish, but that doesn’t mean she can broadcast that she has it now. If he sees that, Bob’s definitely going to know that something is up. Wageslaves don’t take long guns to lunch.
Alice’s next option is to completely disable the wireless features on all the things she wants to hide, while still leaving it enabled on innocuous devices like her commlink (which is still broadcasting her fake SIN, of course.) This means her illegal things can’t be spotted on the Matrix at all. However, it has a few disadvantages:
Obviously, if Alice was trying to sneak into a building in the dead of night, she’d also need to take her commlink offline. It’s pretty hard to sneak into anywhere when you’re broadcasting your Matrix presence to everyone within half a kilometre.
If she is trying to sneak into somewhere, though, Alice’s third option is to set her entire PAN to run silent. This means all the devices in it minimise their traffic to and from the Matrix, the commlink stops advertising itself as a Matrix node, and she generally disappears from the local grid.
Two downsides here:
Most of the time, Alice is only going to use running silent if she’s trying to sneak into somewhere. Taking selected devices offline is probably the better option in public spaces.
All those tags in your clothes and equipment, reporting their existence to anyone nearby and their location to servers at all times, would make sneaking around pretty tough. Shadowrunners and other dubious types get around this by scrambling them to destroy their code entirely, or randomising their IDs on a regular basis so no-one can discern any pattern from them.
Normal tags are very easy to mess with and have no countermeasures against this.
All the clever cloud security stuff described above doesn’t work for squat if you have a low-grade fake SIN or no SIN at all. Fortunately, there’s a fallback mechanism built into the protocols designed to work when the user is off-grid, for example, if there’s another Matrix crash or if you’re way out in the wilds. You can download backup copies of your digital keys and store them on your commlink, then use them to start your car or open your apartment without any hosts being involved. Bonus: it’s another way of tracking you that no longer works. Only downside is, if your keys get stolen by a script kiddie, so does your stuff - and if your commlink gets trashed, you’d better have backed them up somewhere… Better upgrade from that base model Meta Link, omae.
Mass media would like you to believe there’s a world of difference between the tools of the Matrix security specialist and those of the decker. After all, the good guys and the bad guys can’t use the same stuff, right? Otherwise you might question which was which. Well, actually, their ‘decks and their actions are more alike than they are different. Both groups of people need the ability to reach out and hack targets across the local mesh, whether to attack or counter-attack. So both groups need quantum decryption cores to crack encryption and armies of vuln scanners to find exploits on their targets.
What does differ, though, is the degree of monitoring by GOD. Legal cyberdecks are infested at every possible level with stealthmode code and hidden firmware designed to report back to the Grid Overwatch Division at every turn. This code is created by pseudo-AIs, different on each deck manufactured, in an attempt by the corps to stay one step ahead of the streets.
The high price of illegal cyberdecks doesn’t reflect the off-the-shelf hardware so much as the modifications necessary to turn it into a black market cyberdeck. Skilled technicians must labour for many hours to unpick the backdoors and boobytraps built into legal cyberdecks by the manufacturers before they can be used for illicit goals. Processors and memory cores sometimes have to be replaced with custom-manufactured replacements, assembled on nanoforges in anonymous back-alley workshops. An entire cottage industry exists, hidden from view, and the best of their work is always in high demand.
Somewhere in between cyberdecks and commlinks is a broad grey area of kitbashed decks. Usually not much more than a souped-up commlink running some custom software cobbled together by some backroom illicit tech, they are far less capable than even the weakest purpose-built ‘deck. However, they’re also a lot cheaper, and much easier to find on the streets. Many a novahot decker started out with nothing more than a kitbash ‘deck and a datachip full of dreams.
For legal Matrix users, the local mesh - the wireless peer-to-peer network that gets their data onto the backbone - is just an implementation detail. They rarely even think about it. But for deckers, it’s home.
The corps control and patrol the backbone, and going anywhere near it with an illegal device is begging for trouble. But the local mesh - that’s different. It’s a dizzying mishmash of devices, built up of protocols laid on top of protocols laid on top of protocols, each layer with its own cocktail of security holes. There’s no central control and no central oversight, it’s impossible to secure, and it’s where deckers earn their keep.
A decker begins by running routines to poison the local mesh routing protocols. Normally, the grid just passes traffic along to the nearest uplink node. But under the decker’s control, this is corrupted, causing it to pass traffic through the local mesh directly to the target of their hack. Like all local mesh connections, this has a limited range though, so deckers need to be brave enough to get out into the field and within range of the devices they wish to pwn.
Implanted cyberware always comes with the necessary neural interfaces so the user can make it work without requiring anything else. Nevertheless, legally manufactured cyberware makes heavy use of wireless Matrix networking, for a number of reasons:
The most important, however, is for communication between and coordination across different cyberware subsystems. It is quite difficult to run enough cables through squishy flesh to hook up everything to everything else. Plus, different pieces of cyberware from different manufacturers run on a mishmash of semi-incompatible low-level protocols, and that stuff is hard to change when it requires surgery to get at the controls. Instead, commercially available cyberware usually just uses the wireless Matrix as a sort of universal communication bus.
Consider a high-threat response soldier fitted with a smartgun system, cybereyes, and a cyberarm with recoil-compensating gyroscopes. When they fire their weapon, all these systems need to work together in harmony to compute trajectories, display the results of this computation to the user via an ARO, key up the gyros to make just the right motions to counteract the gun’s recoil as they fire, and so on.
To do all this without the wireless Matrix requires a lot of wires criss-crossing the user’s body plus a coordinating processor to mediate the different protocols used internally on each piece of cyberware. These devices exist - they are called internal routers - but they are invasive and expensive and offer limited benefits to legal users. Most people just rely on their devices’ ability to use the standardised protocols of the wireless Matrix to talk to each other.
Besides, the corps like it that way. Most corp security guards are under-trained, under-paid, over-worked, and over-dosed on (at least) stimulants and (quite possibly, at the first sign of trouble) combat drugs. The corps know they can’t be trusted not to wipe each other out in a hail of blue-on-blue gunfire. But proper training costs money, money that goes down the drain when the next shadowrunner team deletes Jimmy; and if there’s one thing the corps hate to do, it’s spend money.
The answer is ubiquitous wireless. Logging of patrol routes so you can be sure they’re not shirking. Inventory tracking of each and every valuable and dangerous item via RFID tags - right down to the bullets in Jimmy’s gun. Remote biometric monitoring, so you know if Jimmy gets jumped, knocked out, or flatlined by intruders. Smartgun fire systems with biometric triggers and linked to friend-or-foe tracking, so the bad guy’s can’t take Jimmy’s gun from him, and so Jimmy can’t get trigger happy and accidentally splatter your star researcher’s expensive brains everywhere.
This isn’t always the case, of course. Elite troopers, from HTR squads on up, are fully trained and perfectly capable of working as a team without the crutch of a wireless network (if they are willing to forgo the benefits of realtime heads-up tactical displays). But Jimmy? Honestly, if you took his wireless away, he’d be a straight-up liability to himself and others. With all this wireless gunk, you barely need the human being to think at all, and that’s the way the corps prefer it.
I’m back with another few excerpts from my Big Ol’ Matrix Re-fluff doc. This time I’m talking about xxx and xxx.
A reminder: my goal here is to re-write the existing fluff to support (my interpretation of) the rules as written. I’m of the opinion that a lot of existing SR material introduces tons of concepts then launches into the rules for how these concepts interact mechanically without first exploring how they interact narratively. So you have to try and reverse-engineer the narrative from the rules, but the rules are complex and sometimes ambiguous, so that’s difficult. I’m trying to bridge over that gap.
Previous posts in this series:
I am not the first to attempt something along these lines. Some other sources I have drawn on:
Consider a busy street. It’s lunchtime in a commercial district in a decent part of town. The sidewalks are thronged with corp workers looking for lunch, walking past various eateries and cafés. Above them tower offices, scores of stories of chrome and steel. Amongst them pass some less savoury characters: some street rat gangers looking for a score, some shadowrunners up to no good, some Knight Errant beat cops trying to keep the peace.
What does this scene look like, in augmented reality (AR), for each of the types of people in the scene? What Augmented Reality Objects (AROs) show up, and under what circumstances?
Let’s start with the corp wageslaves.
Each of them have a commlink. A bit over half of them have a datajack and are hooked into their ‘link wirelessly; most of the rest are using an image link built into cybereyes, glasses, or contacts. All bar a few of them have an active AR layer. The ones who don’t are usually obvious – they have to look at the screen of their commlinks to get around, clearly marking them as being too poor to afford even basic amenities. How primitive.
Each of them has their commlink set to broadcast their System Identification Number (SIN) like all good law-abiding citizens. This takes the form of a small augmented reality object (ARO) that is fixed in position somewhere over their head, moving with them. However, this produces a lot of distracting clutter, so most of the civilians will set their commlinks to filter out these types of objects. They’re there, if they want to look for them: but mostly they’re invisible.
Similarly, each person is carrying around their personal area network (PAN), consisting of their commlink and all their various items of gear that are slaved behind it (cyberwear, maybe a light pistol, perhaps glasses (or contacts) and earbuds if they don’t have cyberwear, etc etc.) In the Matrix, this appears as an icon for the commlink itself, plus a forest of smaller icons for the devices connected to it. But that’s an awful lot to look at in AR while walking down the street, so most people set their own commlinks to either hide it entirely, or at most show each PAN as a single icon and hide all the connected devices.
The businesses along the street are also broadcasting AROs: menus, flyers, advertising, logos. These vary in size and offensiveness of design. Huge flashing billboards outside a Stuffer Shack proclaim 2-for-1 on Nuke-’Emz Frozen Burritos. Wally and Wendy Wageslave pause to think if they want to partake in them.
Director Dan tuts as he nearly walks into Wally and Wendy. He doesn’t even see the Stuffer Shack promo; although it’s set up to broadcast to everyone, Dan’s high-end commlink treats it as spam and hides it from him. Dan’s eyes are focussed on a discreet, unmarked door up ahead. Unmarked in physical space, anyway. But in AR, Dan can see the logo of the members-only club he’s going to go to for lunch. This ARO is visible only to a select group of people, identified by their broadcast SIN, and Dan’s on the list.
That’s not the only difference between what Dan sees and what Wally and Wendy see. All up and down the street, advertising AROs are customised to various tracking profiles built from everything they do online and stored against their SIN. When they look at a particular blank piece of wall, Dan sees ads for the newest Ares special edition executive light pistol, with a real mother-of-pearl inlay on the handle. Wally sees a reminder that he won’t want to miss the big Urban Brawl match tonight for his favoured team, the Seattle Screamers. Wendy sees an advert for a new album from Null Shiva, a Doom Arcanometal band she’s been listening to a lot lately. This invasive and systemic tracking is just how the world is run, chummer. Dan’s profiles scream he has money to spend, and the ads adjust accordingly; the stuff is pricier and the ads are classier. Wally and Wendy aren’t so lucky in life, so they see cheaper stuff in garish colours. So it goes.
Overhead, some ARO graffiti (sometimes called “graffitaro” by dorks) lurks; an animation of a swooping dragon in neon colours. It’s being broadcast from a well-hidden data tag stuck behind the facade of the Stuffer Shack. Occasionally, people with cheaper commlinks flinch as the dragon appears to swoop towards them. Those with more expensive commlinks don’t see it, as the ‘link correctly deduces this is graffiti and should not be displayed. The pranking deckers who place these tags are in a constant, unending war with the spam filtering heuristics deployed by commlink manufacturers.
Moved to this doc (private.)
The SR6e ruleset contains a gently streamlined version of the Matrix rules from Shadowrun 5e; these have several useful changes that reduce book-keeping and give deckers a simpler and more agile action economy. In this section, I lay out a backport of these rules to work within the Shadowrun 5e ruleset.
The SR6e ruleset contains a gently streamlined version of the Matrix rules from Shadowrun 5e; these have several useful changes that reduce book-keeping and give deckers a simpler and more agile action economy.
Some of the changes to the Matrix rules are not compatible with the rest of SR5e: for example, the use of attack and defence ratings to distribute Edge during Matrix actions. Fortunately, it is easy to ignore those, and still use other parts of the SR6e Matrix system within SR5e. These houserules aim to do just that.
I will ignore here the wider changes to SR6e that the decker rules fall into line with, eg. attack-rating-vs-defence-rating, Edge, and so forth. I’m concentrating on Matrix rules.
This section is very long, but you don’t need to read most of it.
The second and larger section - Comparing SR5e and SR6e - goes through the two systems item-by-item, and is the section I wrote first, to convince myself I understood both rulesets. This is the bulk of the section.
However this section is not needed if you just want to read the houserules. For those, you only need to read the Rule Changes section (which is a good deal shorter, at ~8 pages.)
These rules are canon for my current campaign. However, I am working on superseding them with a set of rules that is further streamlined.
Remove the concept of marks entirely. Replace with three levels of access:
(Note there is no equivalent to 2 marks, a small efficiency gain. GMs don’t need to track it and deckers don’t need to pass through it on the way to Admin access.)
All iconography around marks is also removed. No more visible marks or designing a mark that matches your persona.
In addition, most of the time, a character’s hack targets will be an entire PAN or WAN, not not an individual device (see below). Accordingly, access levels are tracked against the entire PAN or WAN. This also reduces book-keeping.
There are a variety of things in 5e’s version of the Matrix rules that derive an effect from the number of marks you possess, eg. the Brute Force action does extra Matrix damage, so does the Mugger program, and so on. I am preserving these by ruling that User access is equivalent to 1 mark, and Admin access is equivalent to 3 marks.
For the purposes of this doc, a WAN is a PAN that is run off a host rather than a commlink/cyberdeck/RCC. Same game mechanics, though, just with more dice.
No changes to make here.
Any device that uses the Matrix to function - including any gear like guns and cyberware that have wireless bonuses - incurs dice pool penalties when they take Matrix damage: -1 per three full boxes. This makes Data Spike wielding deckers more dangerous.
No changes to dumpshock or link-locking.
Your failed Attack actions no longer give you Matrix damage, and your failed Sleaze actions no longer give the target marks against you.
Rejected rules: 6e also reduces matrix damage and changes the damage resistance test, in line with how normal damage works throughout 6e, but I’d rather keep these rules consistent with 5e’s damage model. 6e has a slightly different Matrix repair test using the extended test mechanics, but it’s slower to resolve, so I have left it out. 6e changes the damage codes for dumpshock, again to be inline with the reduced damage codes used throughout the edition. This is better left alone in 5e.
However, I’ve kept the changes to failed actions in, because getting hurt just because you failed to hit someone seems un-fun and (more importantly) not at all how any other Shadowrun combat type works. I prefer mechanical consistency across systems, where possible.
No changes.
No changes.
As in 5e, all hits rolled against the decker in opposed tests on illegal actions add to the Overwatch Score. These are any actions that use the [Attack] or [Sleaze] stats of your deck to determine their limit.
However, remove the secret +2d6 that is added to OS every 15 minutes. Instead, deckers accumulate OS in three new ways:
As before, Overwatch Score is reset when the decker logs out or reboots their deck. And Convergence happens when the Overwatch Score reaches 40, and has the same effects.
SR6e does not have the special rules for convergence when inside hosts (instead of decker getting dumped, the host starts launching IC.) I’m keeping those rules as I think it adds more variety.
In addition: in 5e, the deck takes 12 boxes of resisted Matrix damage when Convergence happens. In 6e, it is automatically bricked. The latter can be very dangerous for deckers, as it’ll always strip Firewall away from their biofeedback damage resistance test. I prefer the former approach for this reason.
Grids add little to the rules beyond book-keeping, and make some stuff confusing. Keep them for fluff and flavour (the Ares grid has Ares propaganda, the Seattle grid has Emerald City spam) but remove all mechanical effects. All hosts and devices are accessible from all grids without penalties.3
Keep only the -2 dice pool penalty to all actions while using the public grid - it still hurts to be poor, and the free public access grid still sucks.
Three important changes:
Stealth tags are always running silent and resist Matrix perception actions with 10 dice.
Remove the Hack on the Fly action. Replace it with two new linked actions:
You probe a host, PAN, or device for weaknesses, looking to gain access and create a lasting backdoor to the system. You take your time not to alert any security to your presence, and you can create an exploit that may last until you are ready to use it. While not as fast as using Brute Force, Probing a device does not raise an alarm automatically. Even if your attempt initially fails, it will not trigger an alarm unless you glitch. Systems and devices will not detect your presence until you have gained access to them.
Once you create the exploit, you may then use the Backdoor Entry action at a later time. Net hits on this test count as a dice pool bonus on your future Backdoor Entry test. The duration of these backdoors depends on the device or host—generally speaking, the backdoor lasts for [10 – Host/Device Rating] hours. Most systems create a changelog and will automatically correct and report differences to their configurations caused by the presence of these exploits.
According to Banshee (the Matrix rules author) the intention was that Probe can be repeated, albeit at a cost, using a variation on Shadowrun’s usual extended test mechanism. The decker can keep attempting further rolls (at -1 dice pool each time, as usual for extended tests) against a threshold determined by the targeted system’s defence roll, all while the Overwatch Score ratchets upward. It’s a push-your-luck mechanism.
However the German CRB simply makes Probe a normal opposed test that happens to take one minute of game time to resolve. This is the rule I am applying in my game, principally because I prefer standardised game mechanics to one-off bespoke rules. But also because the former approach can result in a decker putting 50+ dice down on the table across multiple rolls, slowing down gameplay.
It isn’t completely clear if a decker’s Probe results persist if they log out of the Matrix then log in again later. For these houserules, I am ruling that they do.
Once a decker has successfully run Probe against a target, they can move onto the second new action:
You attempt to use a backdoor you have put in place to gain illicit entry into a host, device, or other Matrix area. This action can only be used if you have previously used Probe on the target successfully; net hits from that successful Probe count as a dice-pool bonus on this test. If the test is successful, you gain Admin access to the target, and it does not count as illegal Admin access (though taking illegal Matrix Actions will still increase your Overwatch Score).
If this test fails, the backdoor you have made was detected and removed, and you cannot attempt Backdoor Entry again with the same host until a new backdoor is made through the Probe Action. Failing this test does not immediately set off alarms, but the character’s OS increases as normal.
By default, a successful Brute Force check grants User access. If the decker wants to go from Outsider to Admin access in one go, they may attempt to do so, at a -6 dice pool penalty (reduced to -4 with the Go Big Or Go Home quality).5
Note that access gained via Brute Force will accrue Overwatch Score as long as the decker maintains the forced access; at a rate of +1 per Combat Turn for User access, or +3 per Combat Turn if the decker has Admin access. So once you use this, the clock is ticking!
Also: Brute Force no longer does optional Matrix damage, in the name of up speeding play and simplifying things. One action = one result.
In these houserules, as in SR6e, Spoof Command no longer needs any marks on anything to work. (In SR5e, it requires a mark on an icon that can legitimately command the target device.)
The scope of Spoof Command has always been fairly unclear. Can you use it to eject a clip from a smartgun? Can you use it to loop a camera feed? These seem reasonable. Can you use it to shut down an opponent’s wired reflexes or cyberarm? That seems overly powerful, as well as making Spoof Command overlap with other, more explicit methods to achieve that goal (eg Data Spike, Format Device / Reboot device.) Force a hostile drone to fire on its allies? That one seems ok…?
“You spoof a device’s owner’s identity, making the device think that your command is a legitimate one from its owner. … This trick only works on devices and agents, not IC, sprites, hosts, personas, or any other icons.”
This needs consideration and playtesting; I don’t have the answers yet.
A sort of stun-damage analog to the physical-damage attack of Data Spike:
Sometimes you want to deliver as much hurt as possible; sometimes you want to deliver a little pain and a little slowness, in order to make the rest of your blows land easier. If you succeed in making this attack, do (1 + net hits) damage to the icon you attacked while also reducing their Data Processing rating by the same amount. If a device’s Data Processing rating is reduced to 0, the user cannot perform a Matrix action until it is 1 or more. The Data Processing rating recovers at a rate of 1 point per combat round.
A very minor detail, but this is the counterpart to Crack File. This functionality is in 5e but buried in a weird little alternate mode in a footnote to the Edit File action.
The hits on the Encrypt File test establish an Encryption Rating that’s used to oppose future Crack File attempts.
There are a large number of small changes to various dice rolls and mechanics for actions throughout 6e. In the main, I am choosing not to include these in my houserules. I don’t think any of them have a drastic effect on gameplay, and they will invalidate the 5e quick reference material I use, which is painful. All these changes are documented in the Matrix Actions Comparison section, if you want to see them.
Here are some smaller changes I do think it’s worth making:
Almost all programs can be left as-is. 6e removes a number of programs that are in 5e (see the comparison for details), but they are harmless to leave in place, I think. 6e also changes how a few programs work in order to use the new Edge mechanic; again, this can be ignored.
The only exception is the Guard program, which should be removed, as it only works in the context of marks gained against the decker.
6e’s cyberdecks have double the number of program slots that 5e’s do. I am not adopting this rule in my game, as I think it encourages analysis paralysis from players as they try to juggle 8+ programs. It also results in modifier explosion as each program’s effects is added together. YMMV.
Additional houserule for my table: Remove the Wrapper program. If it exists, it leads to requirement for endless Matrix Perception tests, slowing down gameplay.
Keep host and IC initiative, stats, and attack rolls the same. See below for a detailed comparison, but in general, make the following changes to IC effects:
No -2 dice pool penalty to Matrix actions for running silent - this is another fiddly detail to remember and easy to forget about. Furthermore, with the move to make running silent a setting that applies to an entire PAN rather than an individual device, it becomes quite painful for players to make decisions about. So it is removed in these houserules, in line with SR6e.
To make it explicit, I don’t suggest changing anything on this list. They should still work fine with the former changes in this section.
Cyberdecks: Leaving aside the splitting of 5e’s cyberdecks into 6e’s cyberdecks and cyberjacks, the stats are broadly equivalent in both editions. No particular adjustments are needed to 5e’s deck’s stats to fit into the backported rules.
However, I’d recommend GMs consider reducing the cost of cyberdecks significantly, at least by 50%, perhaps even more… or be prepared to make upgraded cyberdecks an occasional run reward from Mr Johnson, and give all PC’s decks plot armour, as losing one will be financially ruinous.
Use of ASDF stats to determine test limits; also how cyberdeck stats are assigned and moved around between the ASDF slots.
All mechanics for what happens when Convergence occurs.
Noise is unchanged in this ruleset, both in terms of how it is calculated and its mechanical effects.
Matrix Search in 6e appears to have been the victim of mangled editing resulting in dubious maths7. A strict reading of RAW suggests a decker can make an extended test, so rolling 50-100 dice in aggregate, against a results table where 10 hits reveals “deep secrets others are trying to actively hide” - a trivial accomplishment on so many dice. It is best left as-is in 5e, I think.
“PAN’s were not originally meant to be as restrictive on number of devices as they ended up (if errata does not get approved to change it a good house rule would be to make it Device Rating x3 for max number of devices)” source ↩︎
This is a houserule; in 6e RAW, direct connection doesn’t grant the firewall bypass. ↩︎
I have little love for the extended test mechanic in general. It’s good in theory, but it simply takes too long to roll 50-100 dice and count the hits. ↩︎
This is the rule in 5e, also, as of Kill Code (see page 32.) ↩︎
Confirmed by Banshee (Matrix rules author) as his intention here. ↩︎
RAW is one minute; Banshee originally intended it to be an hour. I prefer his version. ↩︎
Note I have removed the word “extended” here – see the note below. ↩︎
What follows in this section is a line-by-line comparison of the 5e and 6e Matrix rules. I wrote this section first, to make sure I understood the changes across the two systems. I’ve kept it here in case you are interested but you shouldn’t need to read this to use the houserules presented above.
The formatting of this section has suffered a bit when I transferred it from Google Docs to this website. It might be clearer to read the original doc.
| 5e | 6e | |
| Matrix attributes | There are four attributes (ASDF.) These are intrinsic to the deck the decker is using. They act as limits on most skill checks. | The same four attributes are intrinsic to the deck and cyberjack the decker is using. They are used to calculate Attack and Defence Ratings, which in turn grant Edge on Matrix actions. |
| Matrix condition monitor | 8 + (Device Rating / 2) boxes. No penalties to actions from accumulated damage | Same. -1 to all tests per three boxes of damage |
| Data Spike damage | Persona’s Attack rating | (Persona’s Attack rating) / 2 |
| Matrix damage resistance | Device Rating + Firewall | Firewall |
| Dumpshock | 6S if in cold-sim, 6P if in hot-sim. Resisted with Willpower + Firewall (if deck just got bricked, Firewall is 0). -2 dicepool on everything for (10-Willpower) minutes | 3S if in cold-sim, 3P if in hot-sim. Resisted with Willpower only. Cannot gain or use Edge on any actions for (10-Willpower) minutes |
| Link-locking | Cannot use Switch Interface Mode, Enter/Exit Host, or Reboot on the device your persona is using. Defeated with a successful opposed Jack Out action. (But will give dump shock.) | Same. |
| Repairing Matrix damage | Straight test: Hardware + Logic [Mental]. Takes 1 hour. Each hit = 1 box repaired or cut time in half | Extended test: Engineering + Logic (num_box_damage / 1 hour) |
| Overwatch score (OS) |
|
|
| Convergence | When OS reaches 40 Not in a host: Device takes 12 DV Matrix damage User dumped (w/dumpshock) Physical location reported In a host: Host gets three marks on deck IC is deployed | When OS reaches 40 Bricks device User dumped (w/ dumpshock) Physical location reported No special rules for convergence in a host. |
| Matrix initiative | AR: physical init VR cold sim: VR hot sim: | AR: physical init VR cold sim: VR hot sim: |
There is no major difference in skills between 5e and 6e, other than the fact that the 5e Skill Groups become Skills in 6e. The way the skills are used are the same however.
| 5e skill | 5e skill group / 6e skill |
| Cybercombat | Cracking (illegal) |
| Electronic Warfare | |
| Hacking | |
| Computer | Electronics (legal) |
| Hardware | |
| Software | |
| Compiling | Tasking (Resonance - Technomancers only) |
| Decompiling | |
| Registering |
Any action using any skill in the Cracking group - so any action that uses the Cybercombat, Electronic Warfare, or Hacking skills - is considered to be illegal by the Grid Overwatch Division. These actions will increase a decker’s overwatch score when used.
| 5e | 6e | |
| Getting into a Host |
|
|
| Getting more than one level at once | On Brute Force or Hack on the Fly: By default, they only grant one mark. Decker can shoot for two marks at a -4 dice penalty, or three marks at a -10 penalty. | Backdoor: always grants Admin access. Brute Force: normally grants User access. Decker can opt to attempt for Admin access, but target gets +2 dice pool and +4 Defence Rating in their test. |
| Legitimate access to public Hosts | The host sends Invite Mark to let users get one mark. The user does that, then uses Enter Host. | The host can be configured to allow access to users with Outsider access level. |
Where I list the 6e mechanics as “same” below, what I mean is:
| 5e | 6e | |
| Brute Force (illegal) | roll: Cybercombat + Logic [Attack]
resist: Willpower + Firewall
action: Complex requires: no marks Gain one mark on target per net hit. Every two net hits optionally also does 1 DV or Matrix damage, resisted with Device Rating + Firewall. Can attempt to get two marks in one go at -4 dice pool, or three marks in one go at -10. Can also use this action to hop grids. | roll: same
resist: same
action: same
requires: same Gain User or Admin access on the target if the test succeeds. No mechanic for doing Matrix damage. Can attempt to get Admin access from Outsider, at a cost of +2 dice on the resistance test and +4 bonus to target’s Defence Rating. No mechanics for grid hopping. |
| Hack on the Fly (5e) Probe / Backdoor Entry (6e) (illegal) | Hack on the Fly: roll: Hacking + Logic [Sleaze] resist: Intuition + Firewall action: Complex requires: no marks Gain one mark on target per net hit. Every two net hits also counts as a one hit on a Matrix Perception test, so you get some information too. Can attempt to get two marks in one go at -4 dice pool, or three marks in one go at -10. Can also use this action to hop grids. | Probe: roll: same resist: Willpower + Firewall or Firewall x2 action: Extended, 1 minute[^12] requires: no access Backdoor Entry: roll: same resist: Willpower + Firewall action: Major Action requires: no access No mechanics for grids. |
| Erase Matrix Signature (illegal) | roll: Computer + Resonance [Attack] resist: Signature Rating x 2 action: Complex Action requires: No marks If the test is successful, the signature dissipates. Character must have a Resonance rating to attempt this action. This is a real Matrix Action, and illegal, so risks Matrix damage and Overwatch Score when done. | roll: Electronics + Logic resist: Willpower + Firewall or Firewall x2 action: same requires: User/Admin Same. Same. |
| Invite Mark (legal) | No test | N/A |
| Erase Mark (illegal) | roll: Computer + Logic [Attack] resist: Willpower + Firewall action: Complex requires: 3 marks | N/A |
| 5e | 6e | |
| Control Device (legal) | roll: varies or Electronic Warfare + Intuition [Sleaze] resist: Intuition + Firewall action: varies requires: varies Perform an action through a device you control. Test is usually determined by the device you are controlling eg. a turret would be Gunnery+Agility. All tests are limited by [Data Processing] if that is lower than the limit you’d normally have. If there is no test associated with an action, use the test above. Can use this against multiple targets. If you are the Owner of them all and it’s the same command, no penalty. Otherwise, have to split your dice pool. Free/Simple/Complex is determined by the command given, as is the access level required (1/2/3 marks.) This is a Sleaze action, so OS accumulates. | roll: varies or change stat to Logic resist: Willpower + Firewall action: Major requires: User/Admin Same. Same. N/A. Same. Not mentioned. Always a Major action. Requirement for User or Admin access determined by GM fiat. This is a legal action. If in AR, use normal physical stats. If in VR, use mental stats (Body->Willpower, Agility->Logic, Reaction->Intuition,. Strength->Charisma.) |
| Format Device
(illegal in 5e) (legal in 6e) | roll: Computer + Logic [Sleaze] resist: Willpower + Firewall action: Complex requires: 3 marks Next time device reboots, it fails to restart until repaired. Repair is an extended Software+Logic [Mental] (12, 1 hour) test. | roll: same
resist: Willpower + Firewall or Firewall x2
action: same
requires: same (Admin) Same. Repair is the same as a bricked device, requiring number of hits equal to the devices Device Rating. |
| Reboot Device (legal) | roll: Computer + Logic [Data Processing] resist: Willpower + Firewall action: Complex requires: 3 marks Can’t be linked-locked, suffer dumpshock, reset OS. Comes back online at end of next Combat Turn. | roll: same
resist: Willpower + Firewall or Firewall x2
action: same
requires: same (Admin) Same. |
| Spoof Command (illegal) | roll: Hacking + Intuition [Sleaze] resist: Logic + Firewall action: Complex requires: 1 mark, on some other device Give device or agent command. Need mark on owner you are imitating. “You spoof a device’s owner’s identity, making the device think that your command is a legitimate one from its owner. You need one mark on the icon you are imitating; you do not need a mark on the target. The opposing dice roll is still based on the target, though. This trick only works on devices and agents, not IC, sprites, hosts, personas, or any other icons.“ | roll: Cracking + Logic
resist: Firewall + (Data Processing or Pilot)
action: same
requires: none Same. No access needed on anything. “You send a signal to a device with a command the target perceives as coming from its owner. The device then automatically attempts to perform the action as its next available major action.” |
| 5e | 6e | |
| Crack File (illegal) | roll: Hacking + Logic [Attack] resist: Protection Rating x2 action: Complex requires: 1 mark Remove encryption on a file. | roll: same
resist: same
action: same
requires: same Same. |
| Disarm Data Bomb (illegal[^13]) | roll: Software + Intuition [Firewall] resist: Data Bomb Rating x2 action: Complex requires: no marks Attempt to disarm a data bomb. Bomb deleted if you get any net hits. If not, data bomb activates, damaging file it was attached to. | roll: Cracking + Logic
resist: same
action: same
requires: User or Admin Same. |
| Edit File (legal) | roll: Computer + Logic [Data Processing] resist: Intuition + Firewall action: Complex requires: 1 mark Create, change, copy, delete file. Defender is either the host holding the file or the owner of the file if it’s not on a host. | roll: same
resist: same or Intuition + Sleaze[^14]
action: same
requires: same Same. Same. |
| Set Data Bomb illegal | roll: Software + Logic [Sleaze] resist: Device Rating x2 action: Complex requires: no marks Player chooses:
| roll: same
resist: same
action: same
requires: same Same Same Same Does (Rating x 4) Matrix damage. Same. |
| Encrypt File (legal) | N/A | roll: Electronics + Logic
action: Major
requires: User/Admin Number of hits is the Encryption Rating on the file. |
| 5e | 6e | |
| Check Overwatch Score (illegal) | roll: Electronic Warfare + Logic [Sleaze] resist: 6 dice action: Simple requires: no marks Find out your own Overwatch Score. The 6 dice rolled against this increases your score, and the player finds the score before they are (secretly) added, not afterward. | roll: Same resist: threshold 4 resist: 10 dice (if target is a stealth tag) action: Major requires: Admin[^15] Same. Doesn’t seem to increase your OS…? |
| Matrix Perception (legal) | roll: Computer + Intuition [Data Processing] resist: (if opposed) Logic + Sleaze action: Complex requires: no marks Simple test when used to analyze a Matrix object or scan for silent running icons. For each net hit, get an answer to one question on the table below. If trying to spot icons further than 100 m away, take a simple test: first hit spots target, then additional hits reveal things as above. To spot an icon running silent, make an opposed test as above. First hit spots it, other hits can be used for more information. | roll: same resist: same action: Major; Minor if user has ‘deck or Resonance requires: no access “A successful test gives you information about the target[^16]. With a tie, you can perceive the item’s icon. A single net hit will give you basic information, such as device rating, or whatever name the device or icon calls itself. Two net hits will give you more specific information, including individual attribute ratings, and what programs it is currently running. Additional hits will give you more information based on what the gamemaster wishes to reveal. This test can also be used to attempt to spot any icons in the vicinity that are running silent.” |
| Matrix Search (legal) | roll: Computer + Intuition [Data Processing] resist: threshold; see below action: special requires: no marks Search the Matrix for information about a subject. Threshold determined by table below. Hit beyond the threshold can be used to reduce the time taken (divide the time by the number of net hits.) If you fail the test, still spend the entire base time looking. Can also use Matrix Search while inside a host. Always has a base time of 1 minute. Only works if the information is online within the host; some is in cold (offline) storage. | roll: same resist: none action: “extended, 10 minutes” requires: same Same. Threshold determined by Legwork Table (see below.) N/A. Replaced by the Hash Search action (see below.) |
| Snoop (illegal) | roll: Electronic Warfare + Intuition [Sleaze] resist: Logic + Firewall action: Complex requires: 1 mark Intercept traffic sent to and from target. Listen to, view, or read data live, or save it to storage. | roll: stat changes to Logic
resist: same or Data Processing + Firewall[^17]
action: same
requires: Admin access Same. |
| Trace Icon (illegal but I think should be legal) | roll: Computer + Intuition [Data Processing] resist: Willpower + Sleaze action: Complex requires: 2 marks Find the physical location of a device or persona. After succeeding with this action, you know the target;’s location as long as you have at least one mark. Doens’t work on hosts (as they have no physical location), or IC programs (as they live inside hosts.) | roll: same
resist: same or Firewall + Sleaze[^18]
action: same
requires: Admin access Same. You know the location “as long as you can detect the target.” Same, but it does work on offline hosts with physical hardware. (But you likely know where the are already.) |
| Hash Check[^19] (illegal) | N/A | roll: Electronics + Logic (1 or 4)
resist: threshold 1 or 4
action:Major
requires: User access Search for a file on a host or device based on known metadata. Threshold is 1 if the hash data was known (eg. given to them by Mr Johnson), 4 otherwise. Passing the test narrows the number of possible files down to 32. For every net hit, that number is divided in half. So 5 net hits in total will narrow it down to a single file. If the number of matches is too large after the first test, can repeat, with the usual -2 dice pool penalty. Again, each net hit reduces the number of possible files by 2. |
| 5e | 6e | |
| Crash Program (illegal) | roll: Cybercombat + Logic [Attack] resist: Intuition + Firewall action: Complex requires: 1 mark Overload a chosen program on a chosen target, crashing it. Can use Matrix Perception first to figure out what programs are running, or can observe its effects. Device has to reboot to use the program again. | roll: same
resist: Data Processing + Device Rating
action: same
requires: Admin access Same. |
| Data Spike (illegal) | roll: Cybercombat + Logic [Attack] resist: Intuition + Firewall damage resist: Device Rating + Firewall action: Complex requires: no marks Does Matrix damage. DV = persona’s Attack rating ...plus one box of damage per net hit ...plus two additional boxes of damage for each mark you have on the target | roll: same
resist: Data Processing + Firewall damage resist: Firewall action: same requires: same Same. DV = persona’s Attack rating / 2 (round up) ...same ...no additional damage from access levels |
| Full Matrix Defence (legal) | action: Interrupt (-10 init) requires: 4 marks (owner)[^20] Adds Willpower to defence pool against all Matrix Attack actions for the rest of the Combat Turn. | action: Major
requires: any access level Add Firewall to the “next time you are attacked in the Matrix.”[^21] |
| Tarpit | N/A | Tarpit is a sort of stun-damage analog to the Matrix damage attack of Data Spike. |
| 5e | 6e | |
| Change Icon (legal) | action: Simple requires: 4 marks Change target’s icon to one you have a copy of or have designed yourself. This doesn’t change the results of a Matrix Perception action, but might fool a cursory inspection. You can target your own icon. | action: same requires: User/Admin Same. |
| Enter/Exit Host (legal) | action: Simple requires: 1 mark on host | action: same requires: depends on host |
| Grid hop (legal) | action: Complex requires: no marks Can only do this if you have access to the target grid. If you don’t have legal access, can use Brute Force or Hack on the Fly. Can’t hop grids inside a host. | N/A (removed) |
| Hide (illegal) | roll: Electronic Warfare + Intuition [Sleaze] resist: Intuition + Data Processing action: Complex requires: no marks If test succeeds, target has to do a new Matrix Perception test to find you again. Cannot hide from a target that has a mark on you. | roll: same
resist: same or Data Processing + Sleaze
action: same
requires: same Same. Same. |
| Jack Out (legal) | roll: Hardware + Willpower [Firewall] resist: Logic + Attack (only if link-locked) action: Simple requires: 4 marks Jacks out, reboots device being used. Suffer dumpshock if in VR. Defence pool only applies if persona is link-locked and comes from the persona that link-locked you; if multiple you have to roll against them all. Can only Jack Out to yourself. | roll: same
resist: Charisma[^22] + Data Processing or Attack + Data Processing action: Major requires: any Same. Same. Same. Same. |
| Jam Signals (illegal) | roll: Electronic Warfare + Logic [Attack] action: Complex requires: 4 marks Turns device into jammer. Range: 100m Jam rating: hits on test Cannot use it for anything else while it is being a jammer. | roll: same
action: same
requires: Admin[^23] Same. Same. |
| Jump In (legal) | roll: Electronic Warfare + Logic [Data Proc] resist: Willpower + Firewall action: Complex requires: 3 marks Jump into vehicle, drone, or other device. Requirements:
| roll: Electronics + Logic
resist: same or Firewall x2
action: same
requires: User/Admin Same. Same. Same. Same. When jumped in, the device’s icon becomes part of your persona. |
| Send Message (legal) | action: Simple requires: no marks Send a message to a commcode: a short sentence, or an image, or a single file. If you’re using the Matrix through DNI (even if via AR), can send a longer message (about a paragraph.) Can also use this to open a live feed (audio/video/whatever) to one or more recipients. | action: same
requires: same Same. |
| Switch Interface Mode (legal) | action: Simple requires: no marks Switch from AR to VR, or vice versa. Cannot do this if you are link-locked. Can’t do it to other people. | action: same
requires: same Same. Can also turn silent running on or off. |
| 5e | 6e | |
| Firewall & hacking in | All devices inside the PAN can use the commlink, deck, or host’s Firewall stat to make Matrix defence tests, unless it is being hacked via a direct cable connection. If you get a mark on any slave, you also get a mark on the master. | All devices inside the PAN can use the master commlink or deck’s Firewall stat and the master device’s owner’s Willpower attribute to make Matrix defence tests. Deckers attempting to gain access levels to a device inside the PAN must first compromise the PAN. They cannot Hack on the Fly or Probe devices within a PAN directly. Once they get a level of access against the PAN (User or Admin), they have that level of access for every device on the PAN. However, Data Spike, Tarpit, and Spoof Command can be used against any device a decker can see on the Matrix, regardless of its PAN status, and without hacking the PAN first.1 |
| Direct connections | If you are directly connected to a device inside a PAN or WAN, you bypass the cyberdeck or host’s Firewall stat. Remember that if you get a mark on a slave, you also get a mark on the host. | No specific rules. Getting a direct connection to a device still rolls the PAN/WAN’s full Firewall stat. |
| Maximum size & nesting PANs | A commlink or deck can slave up to (Device Rating x3) devices. PANs cannot be nested. | RAW: A commlink or deck can slave up to (Device Rating) devices.[^25] |
| Iconography | “The PAN is the primary means of displaying the persona, or the icon of the user. Programs and devices attached to the PAN appear as smaller representations of their normal icons, carried by the persona.” | |
| WANs | Same as a PAN, but slaved to a host instead of a commlink or cyberdeck If you are inside a host with a WAN, you are considered to be directly connected to all devices in the WAN | Not explicitly mentioned. |
Nose is the same in 5e and 6e: the same numeric values, under the same conditions, and with the same mechanical effect.
| 5e | 6e | |
| Basics | Switching to silent running is a Simple Action. Running silent imposes a –2 dice pool modifier to all of your Matrix actions due to “the processing power needed to cover your tracks.” Silent running is switched on/off on a per-device basis. | Switching to silent running is the “Change Device Mode” Minor Action. No dice pool penalty. Silent running is applied to an entire PAN at once (say, a user’s commlink and all their devices.) |
| Matrix Perception (legal) | roll: Computer + Intuition [Data Processing] resist: (if opposed) Logic + Sleaze action: Complex requires: no marks Simple test when used to analyze a Matrix object or scan for silent running icons. For each net hit, get an answer to one question on the table below. If trying to spot icons further than 100 m away, take a simple test: first hit spots target, then additional hits reveal things as above. To spot an icon running silent, make an opposed test as above. First hit spots it, other hits can be used for more information. | roll: same resist: same action: Major; Minor if user has ‘deck or Resonance requires: no access “A successful test gives you information about the target[^26]. With a tie, you can perceive the item’s icon. A single net hit will give you basic information, such as device rating, or whatever name the device or icon calls itself. Two net hits will give you more specific information, including individual attribute ratings, and what programs it is currently running. Additional hits will give you more information based on what the gamemaster wishes to reveal. This test can also be used to attempt to spot any icons in the vicinity that are running silent.” |
| Silent running vs Matrix Perception | If there are multiple icons running silent, user has to pick icons (at random) to be revealed. | User can reveal all icons that fail the Matrix perception resistance test in one go. |
| Range for automatically spotting icons | Everything not running silent within 100 m of your deck or commlink is always considered spotted. | No defined concept of “spotting.” |
| 5e | 6e | |
| Host stats | Host Rating, HR+1, HR+2, HR+3 Distributed across ASDF similarly to how cyberdecks work | Same. Same. |
| Launching IC | Launch 1 IC per Combat Turn (at the beginning of the turn). Can run up to (Host Rating) IC simultaneously. Can only run 1 copy of any given IC at once. Can restart “bricked” IC next turn | Same. |
| IC stats | (Host Rating x 2) for IC Attack Rating (limited by hosts’s [Attack]). Initiative: Host Rating + Data Processing + 4D6. Condition monitor: 8+(Host Rating /2)[^27] Defensive rolls and effects vary by IC type. | (Host Rating x 2) for Attack Rating, Condition Monitor, and most rolls. Initiative: (Data Processing x 2) + 3D6. Condition monitor: (Host Rating x2) Same. |
| 5e | 6e | |
| All IC rolls the same attack roll: roll: (Host Rating x 2) [Attack] action: Complex | All IC rolls the same attack roll: roll: (Host Rating x 2) attack rating: Host Attack Rating action: Complex | |
| Acid | resist: Willpower + Firewall If it gets 1 or more net hits, reduces target’s Firewall by 1. If Firewall is 0, causes 1 DV Matrix damage per net hit. Firewall stat cannot be restored until you reboot. | resist: same Firewall attribute reduced by number of net hits. Does not cause Matrix damage. Firewall stat restores itself after you leave the host, at the rate of 1 point per minute. |
| Binder | resist: Willpower + Data Processing Same as Acid, above, but affecting Data Processing. | resist: same Same. If Data Processing is reduced to 0, no Matrix actions can be taken at all. |
| Black IC | resist: Intuition + Firewall If get 1+ hits, target is link-locked. (Attack) DV Matrix damage ...+1 DV per net hit …+2 DV per mark on target Plus the same amount of biofeedback damage | resist: same Doesn’t mention link-locking.[^28] Deals (host rating + net hits) in Matrix damage and biofeedback damage. |
| Blaster | resist: Logic + Firewall As Black IC but only causes Stun biofeedback damage. | resist: same (Host rating[^29]) Matrix damage and link-locks target. |
| Crash | resist: Intuition + Firewall If Crash IC (or its host) has a mark on you, a random one of your programs crashes. It cannot be run again without a deck reboot. | resist: same Same. Doesn’t need a mark on you, though. |
| Jammer | resist: Intuition + Firewall Same as Acid, above, but affecting Firewall. | resist: Willpower + Attack Same as Acid, above, but affecting Firewall. No Attack actions can be used if your attack rating is 0. |
| Killer | resist: Intuition + Firewall (Attack) DV Matrix damage …+1 DV per net hit …+2 DV per mark on target | resist: same Deals (host rating + net hits) in Matrix damage. |
| Marker | resist: Willpower + Sleaze Same as Acid, above, but affecting the Sleaze attribute. | resist: same Same. |
| Patrol | Patrols a host, regularly using Matrix Perception actions on all icons within it. | Rolls Matrix Perception once per minute. |
| Scramble | resist: Willpower + Firewall If the host has three marks on you and you are hit by this, it immediately reboots your deck, hitting you with dumpshock. | resist: same If it hits, it forces you to reboot on your next turn, unless you are link-locked. (No marks required.) |
| Sparky | resist: Intuition + Firewall (Attack) DV Matrix damage …+1 DV per net hit …+2 DV per mark on target Plus the same amount of biofeedback damage. | resist: same Deals (host rating + net hits) in biofeedback damage. |
| Tar baby | resist: Logic + Firewall If it hits, you are link-locked. If you’re already link-locked, it puts a mark on you. | resist: same Same. Does not change access levels. |
| Track | resist: Willpower + Firewall If this IC hits and the host has 2+ marks on you, the host (and its owners) discover your real-world location. | resist: Willpower + Firewall Same, but does not require any access levels / marks on the target. The location is revealed if it hits, regardless. |
| 5e | 6e | |
| Baby Monitor | N/A; Baby Monitor is a “hacking program” in 5e | Make user aware of their Overwatch Score at all times.[^30] |
| Browse | Cuts time for Matrix Search actions in half. | Grants 1 Edge to be used on the Matrix Search roll. |
| Configurator | Store a deck config (ASDF allocation & program load.) Swap the entire config for a Free action, rather than a single pair of stats. | Same. |
| Edit | +2 to [Data Processing] limit for Edit tests. | 1 Edge on Edit File actions. |
| Encryption | +1 to Firewall. | +2 dice pool when using Encrypt File actions. |
| Signal Scrub | Rating 2 noise reduction. | Same. |
| Toolbox | +1 to Data Processing. | Same. |
| Virtual Machine | +2 program slots, but whenever your persona takes Matrix damage, it incurs an additional box that cannot be resisted. | Same. |
| 5e | 6e | |
| Armor | +2 dice to resist Matrix damage. | +2 to matrix Defense Rating. |
| Baby Monitor | Always know your current Overwatch Score. | N/A; Baby Monitor is a “common program” in 6e |
| Biofeedback | When you attack a persona that’s backed by a biological entity (eg. a decker), the character takes Stun or Physical damage equal to the Matrix damage you do (depending on if they are in cold sim or hot sim.) Damage is resisted with Willpower + Firewall, as usual. | Same. Damage is resisted with Willpower alone, as usual. |
| Biofeedback filter | +2 dice pool to resist biofeedback damage. | Allow Device Rating or Body to soak Matrix damage. |
| Blackout | As Biofeedback, but only ever causes Stun damage. | Same. |
| Decryption | +1 to Attack. | +2 dice on Crack File action. |
| Defuse | +4 dice pool modifier to resist damage from Data Bombs. | Allow Device Rating or Body to soak damage from Data Bomb. |
| Demolition | +1 rating to any Data Bombs you create. | N/A |
| Exploit | +2 to Sleaze attribute when attempting Hack on the Fly. | Reduce defense rating of hacking targets by 2. |
| Fork | Can perform a single Matrix action against two targets without splitting your dice pool - make one test, and each target defends separately against the test result. | Same. |
| Guard | Reduces the extra damage you take from marks against you by 1 DV per mark. | N/A |
| Hammer | +2DV to all Matrix damage dealt. | N/A |
| Lockdown | When you cause Matrix damage, link-locks your target until you stop running Lockdown or they Jack Out. | Same. |
| Mugger | Bonus Matrix damage from having a mark on your target is increased by 1 DV per mark. | N/A |
| Overclock | N/A | Add two dice to a Matrix action; one must be the wild die. |
| Shell | +1 dice pool to resist Matrix damage and biofeedback damage. Stacks with similar modifiers from other programs. | N/A |
| Sneak | +2 dice pool to resist Trace User. If you are Converged on, GOD don’t get your physical location. | N/A |
| Stealth | +1 to Sleaze. | Gain 1 Edge when doing the Hide action. |
| Track/Trace | +2 to Data processing when doing Trace User tests, or negate the +2 bonus from Sneak if your target is using that. | Gain 1 Edge when doing the Trace Icon action. |
| Wrapper | Change icon of something to look like a different sort of icon entirely. Can be penetrated by Matrix Perception. | N/A |
Bit weird, that one. It’s not like you can do Full Matrix defence to anyone else. ↩︎
https://forums.shadowruntabletop.com/index.php?topic=30050.msg524803#msg524803
“If all devices are linked to his Commlink PAN then all the cop would see is the PAN as a casual observer, but if the cop then makes a matrix perception check then he will see all active wireless devices unless the guy is actively hiding them and then it becomes an opposed test.”
https://forums.shadowruntabletop.com/index.php?topic=30059.msg529755#msg529755
“[Technomancers] kind of got hosed and can’t join a PAN until they get Living Nerwork .. which I tried to make a Complex Form so it wasn’t locked behind submersion. Skinlink would also allow them to form a direct PAN for their own gear but not join a party network.” source